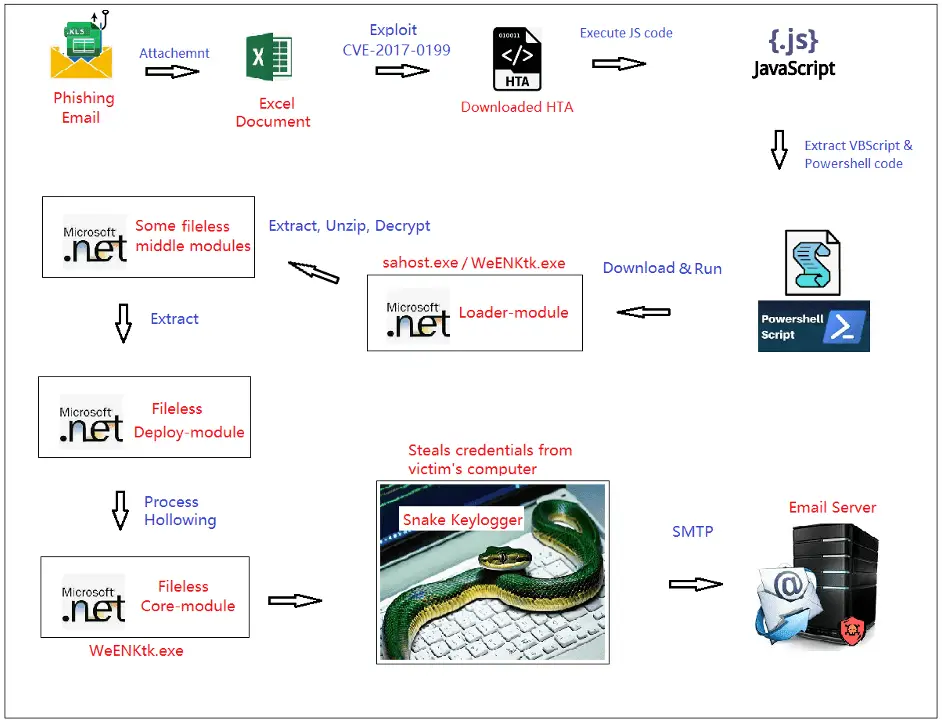
Snake Keylogger campaign workflow | Image: FortiGuard Labs
Fortinet’s FortiGuard Labs has unearthed a new variant of the notorious Snake Keylogger, delivered through a malicious Excel document in a phishing campaign. This keylogger, also known as “404 Keylogger” or “KrakenKeylogger,” has resurfaced with enhanced capabilities, targeting unsuspecting victims by exploiting a well-known vulnerability to infiltrate systems and steal sensitive information.
The attack begins with a seemingly innocuous phishing email, disguised as a notification of a fund transfer. The email, with the subject line marked as “[virus detected]” by FortiGuard’s security filters, contains an attached Excel file named “swift copy.xls.” This document is the gateway to infection; once opened, it triggers a series of malicious activities that culminate in the deployment of Snake Keylogger on the victim’s computer.
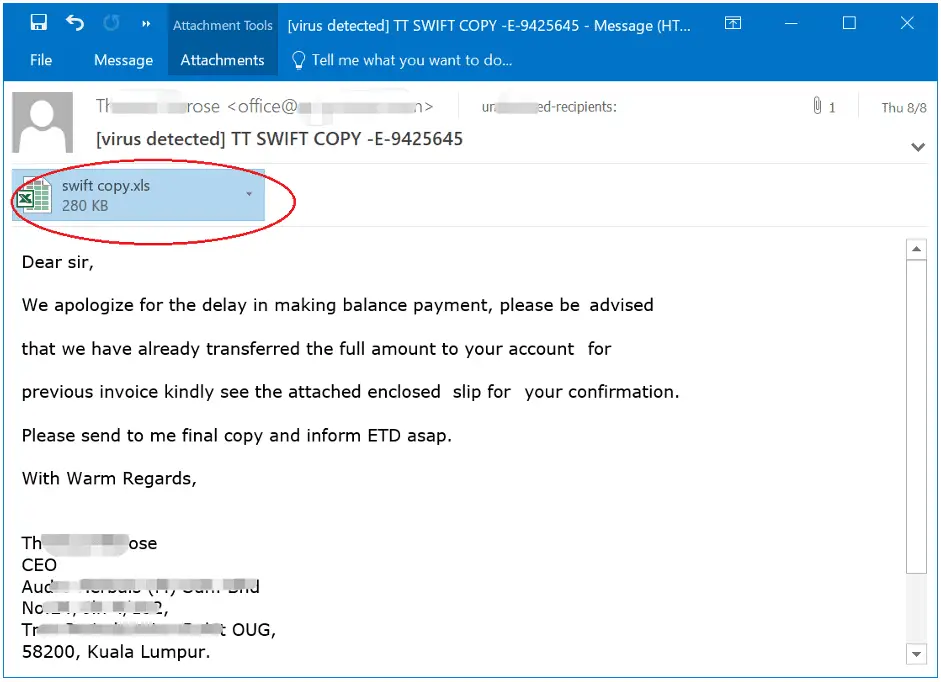
The attached Excel file is no ordinary spreadsheet. Embedded within its binary data is a specially crafted link object that exploits the CVE-2017-0199 vulnerability—a flaw that allows remote code execution via a maliciously crafted file. When the document is opened, this hidden link silently requests a remote URL, which in turn delivers a second-stage payload in the form of an HTA (HTML Application) file.
The HTA file, filled with obfuscated JavaScript code, is automatically executed by Windows’ mshta.exe, setting the stage for the next phase of the attack.
As FortiGuard Labs’ analysis reveals, the HTA file contains VBScript code that creates a “Script.Shell” object, executing a piece of PowerShell code. This PowerShell script, hidden in a base64-encoded string, downloads the final malicious executable—“sahost.exe”—from a remote server and launches it on the victim’s machine.
This executable, which FortiGuard refers to as the Loader module, is the harbinger of the new Snake Keylogger variant. The Loader module is carefully designed to evade detection, using multiple layers of encryption and obfuscation to hide the true nature of its payload.
The Loader module is more than just a delivery mechanism; it is a sophisticated piece of malware engineering. Upon execution, it extracts and decrypts several modules from its own resources, including the core module of Snake Keylogger, which is hidden within an encrypted Bitmap resource named “KKki.”
This complex process involves multiple decryption steps, with the final payload—a DLL named “Tyrone.dll”—being loaded into memory and executed. FortiGuard Labs has aptly named this critical component the Deploy module, responsible for ensuring Snake Keylogger’s persistence and executing its core functions.
Once deployed, Snake Keylogger burrows deep into the victim’s system, establishing persistence by creating a scheduled task that launches the keylogger at system startup. It then uses a technique known as process hollowing to hide its activity. This involves creating a new process and injecting malicious code into it, allowing the malware to operate stealthily, and avoiding detection by conventional security measures.
The heart of Snake Keylogger lies in its ability to steal a wide array of sensitive information. This variant, like its predecessors, is capable of logging keystrokes, capturing screenshots, and siphoning off saved credentials from web browsers, email clients, FTP clients, and instant messaging software. The list of targeted applications includes over 50 popular programs, making this keylogger a versatile and dangerous tool in the hands of cybercriminals.
One particularly insidious feature of Snake Keylogger is its ability to send stolen data to the attacker via SMTP, using email as the exfiltration method. This allows the attacker to receive the victim’s credentials and other sensitive information in real-time, facilitating further exploitation or financial theft.
FortiGuard Labs’ deep analysis of this new Snake Keylogger variant also uncovered several anti-analysis techniques designed to thwart security researchers. These include the use of multiple layers of encryption and obfuscation, as well as hardcoded IP addresses that allow the malware to detect if it is running in an analysis environment. If the malware detects a known IP address associated with analysis systems, it only collects credentials without sending them to the attacker, further complicating detection efforts.
The researcher recommends that users exercise caution when opening unsolicited emails, especially those containing attachments. Keeping software up-to-date and employing robust security solutions can also help mitigate the risk of falling victim to such attacks.
Related Posts:
- North Korean Hackers Exploit Old Office Flaw to Deploy Keylogger
- Keylogger in Microsoft Exchange Server Breaches Government Agencies Worldwide