ASEC
AhnLab Security Intelligence Center (ASEC) has recently uncovered a concerning development in ransomware attacks. A new threat actor, previously known as Trigona ransomware, has been identified as installing Mimic ransomware. This discovery sheds light on the evolving tactics of cybercriminals who continue to target MS-SQL servers, exploiting vulnerabilities in the Bulk Copy Program (BCP) utility.
Trigona ransomware, active since June 2022, has a history of targeting MS-SQL servers. Notably, it was implicated in an attack on the ManageEngine vulnerability (CVE-2021-40539) in February 2023. In April 2023, AhnLab’s ASEC Blog highlighted another case where Trigona struck poorly managed MS-SQL servers.

In the recent attack, the threat actor behind Trigona employed BCP to export the ransomware from a database to a local file. The attacker’s email address “farusbig@tutanota[.]com” was found in the ransom note, linking this new Trigona attack to previous instances.
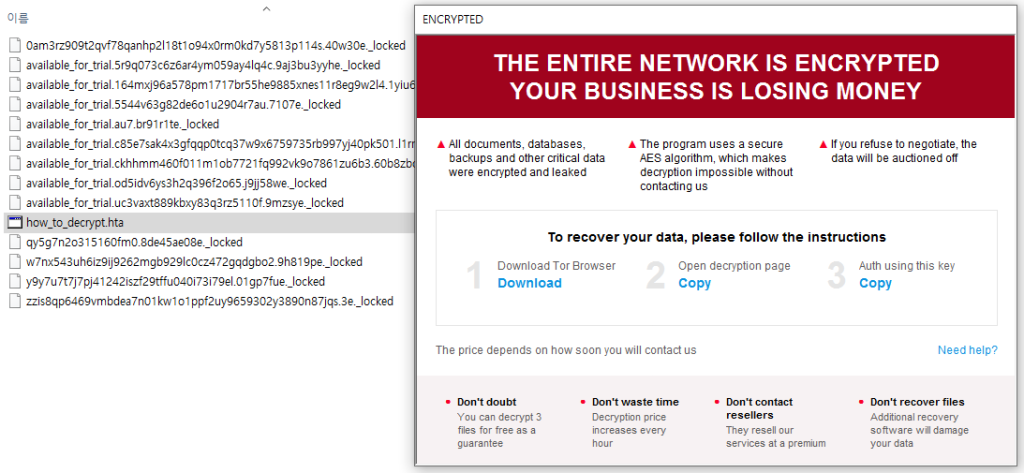
Mimic ransomware, which first emerged in June 2022, is notorious for abusing the file search program called Everything to expedite file encryption. It also borrows features from the Conti ransomware due to a source code leak during its development.
The recent attack cases involving Mimic ransomware are similar to earlier reports from Trend Micro and Securonix. The malware is packed into a 7z self-extracting executable file, containing a password-protected “Everything64.dll” collection. When executed, this malware is decompressed, along with the Everything tool. The attacker’s email address, “getmydata@list.ru,” differentiates this attack from prior Mimic ransomware samples.
The attackers primarily target poorly managed MS-SQL servers with weak account credentials, leaving them susceptible to brute force and dictionary attacks. This modus operandi aligns with previous Trigona attacks and is confirmed by infection logs of other malware strains like LoveMiner and Remcos RAT.
BCP utility (bcp.exe) is a command-line tool frequently used to import or export large volumes of data in MS-SQL servers. In this attack, the threat actor used BCP to save the malware in a database and create a local file from it.
Various malware strains and tools were extracted using BCP commands, including AnyDesk, Port Forwarder malware, Launcher malware, Mimic ransomware, Trigona ransomware, and others. This method allows attackers to deploy malicious payloads efficiently.
Before creating malware with BCP, the threat actor gathers system information using commands like “hostname,” “whoami,” and others. This information helps tailor the attack to the victim’s environment.
Although there is no direct evidence of Mimikatz usage, attackers sometimes configure the UseLogonCredential registry key to obtain plaintext passwords.
The threat actor installs AnyDesk for remote control of infected systems, exploiting its legitimate features for malicious purposes.
Besides utilizing BCP, attackers use safe mode to their advantage. They create launcher malware that can run in safe mode and a port forwarder malware for remote control.
The launcher malware copies itself into a temporary directory, registers as a service, and runs ransomware with safe mode deactivation after execution.
The port forwarder malware supports port forwarding to the RDP service, enabling remote control even in NAT environments.
The evolving tactics of ransomware threat actors pose a significant threat to organizations. To defend against such attacks, administrators should enforce strong password policies, update software regularly, and implement security measures like firewalls.
Failure to do so can result in not only data breaches but also the encryption of entire networks, leading to catastrophic consequences. Proactive cybersecurity measures are essential in the battle against ransomware attackers, who are becoming increasingly sophisticated in their methods.