Windows SmartScreen warning
The notorious Mispadu Stealer infostealer has been lurking in the digital shadows since 2019, primarily targeting Spanish- and Portuguese-speaking victims, with a strong focus on Latin America (LATAM). Unit 42 researchers recently made significant discoveries related to this malware, shedding light on its latest incarnation, the evolving techniques it employs, and the SmartScreen vulnerability it exploits.
Mispadu Stealer first came to the attention of cybersecurity experts when it was initially reported by ESET in November 2019. Written in Delphi, this banking Trojan primarily targeted victims in Brazil and Mexico. Over the years, it has continued to evolve and adapt to new security measures, making it a persistent and challenging threat.
Unit 42 researchers stumbled upon Mispadu Stealer’s latest variant while hunting for the SmartScreen CVE-2023-36025 vulnerability. This security feature bypass vulnerability within the Windows SmartScreen function is designed to protect users from potentially harmful websites and files by issuing warnings. However, attackers have found a way to exploit CVE-2023-36025 to bypass these warnings.

The bypass technique involves crafting a specially designed internet shortcut file (.url) or hyperlink that references a network share, rather than a URL. This clever manipulation of the SmartScreen warning system tricks Windows into not displaying the warning message. Instead, upon clicking the .url file, the victim is directed to the attacker’s network share, where a malicious payload is retrieved and executed.
In November 2023, while investigating attempts to bypass SmartScreen by identifying binaries executed from network shares, Unit 42 researchers uncovered a .url file that executed a command to retrieve and execute a malicious binary. This .url file was initially contained within a .zip archive downloaded by the Microsoft Edge browser. This distribution method can involve email attachments or downloads from malicious websites.
Upon further analysis, researchers identified several similarities between this new Mispadu Stealer variant and previous versions. The campaign’s command and control (C2) infrastructure, as well as its info-stealing functionality, closely resembled those used by Mispadu Stealer samples from May 2023.
Notable similarities between the samples include the use of SQLite to read stored credentials and targeting specific banking websites. However, the newer samples seemed to have evolved their techniques, shifting from known tools like WebBrowserPassView and Mail PassView to using SQLite for credential extraction, likely to evade detection.
Another similarity was the exploitation of the WebDAV client for execution. While specifying an HTTP port within the UNC path forced Windows to use WebDAV over HTTP instead of SMB, this technique is not exclusive to Mispadu Stealer, as other malware strains have employed it as well.
The campaign from August 2023 also showed parallels, with both using .url files for initial delivery. However, the earlier campaign leveraged PowerShell code for its info-stealing capability and possessed additional capabilities not found in the newer variant.
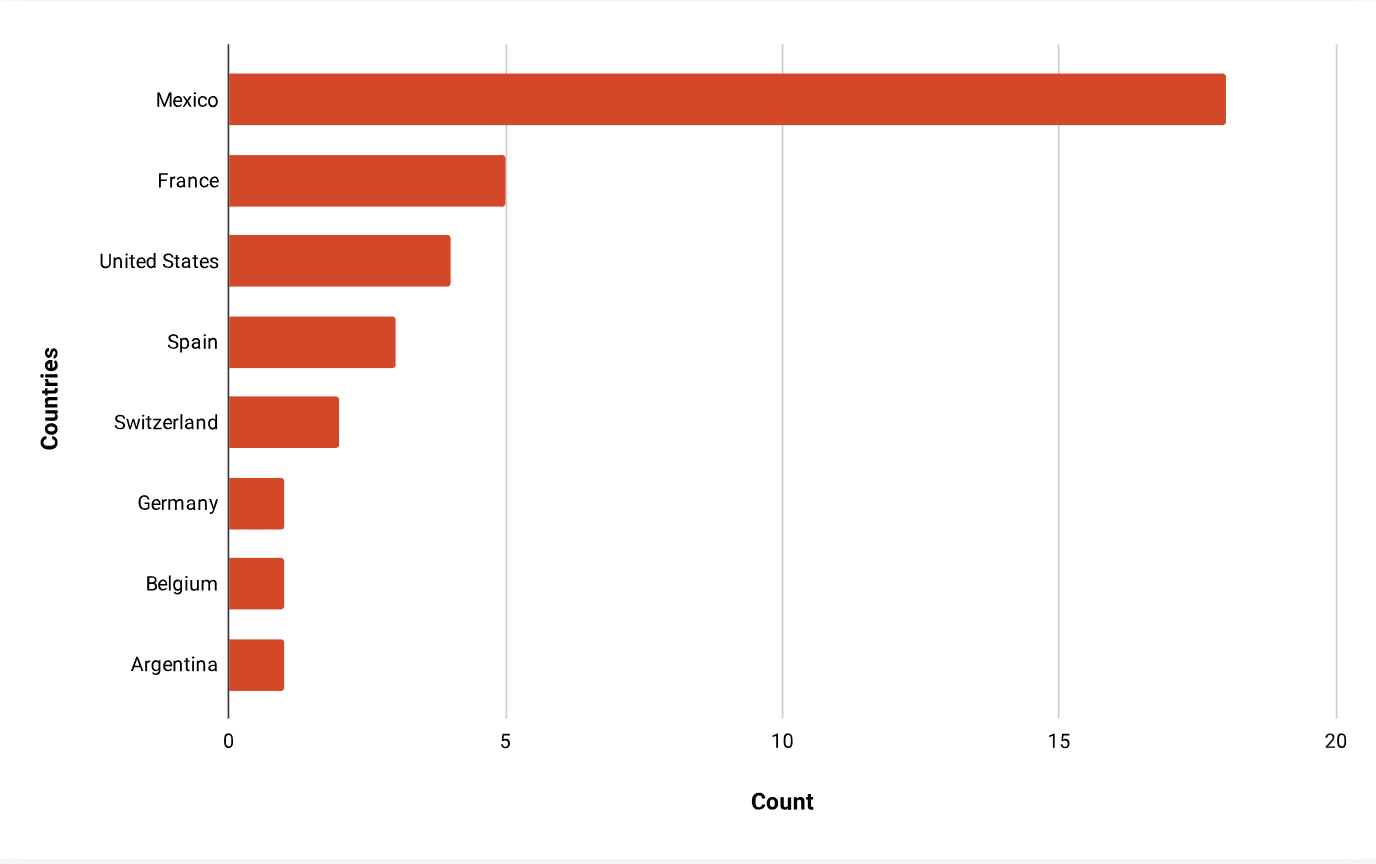
While Mispadu Stealer typically focused on Latin American countries and Spanish- or Portuguese-speaking users, this latest campaign has been detected in various regions, with Mexico being the most prominent. The malware’s rapid spread into other European regions suggests that its threat authors may have broader aspirations in the future.
The evolution of Mispadu Stealer serves as a stark reminder of the constantly changing threat landscape in the world of cybersecurity. While this malware strain has undergone significant transformations, researchers can still identify subtle similarities that help attribute it to previous campaigns.
Staying informed about the latest threat intelligence, deploying robust endpoint protection, and fostering a culture of cybersecurity awareness among users are all crucial components of defending against ever-adapting threats like Mispadu Stealer.