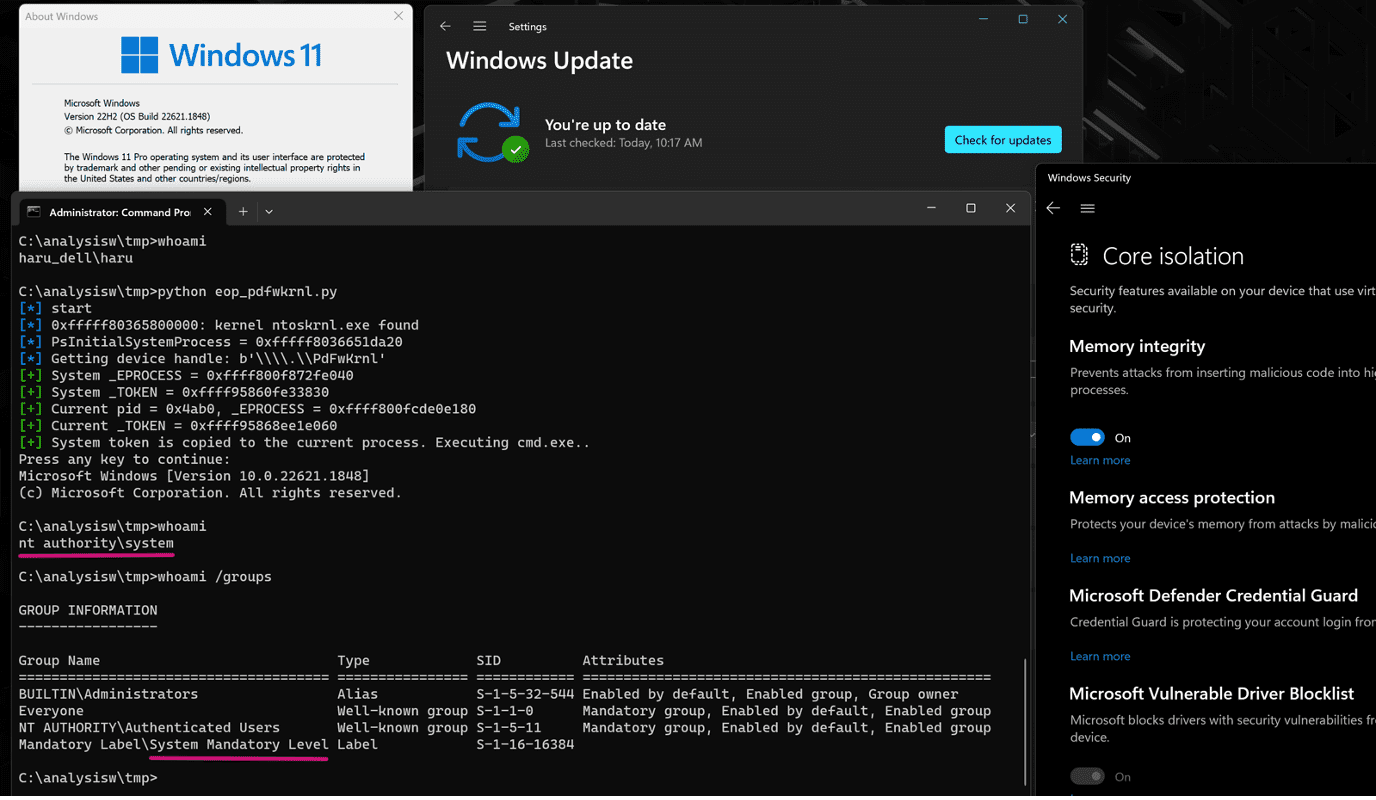
EoP exploit for AMD driver (PDFWKRNL.sys) on HVCI-enabled Windows 11 | Image: VMware Carbon Black
VMware’s Threat Analysis Unit (TAU) has disclosed 34 kernel drivers susceptible to exploitation for firmware modification and privilege escalation by attackers.
Kernel driver exploitation by cyber criminals and state-sponsored hacking collectives is not uncommon. Such drivers can grant perpetrators the ability to manipulate system processes, maintain persistence, and circumvent security measures.
The TAU specialists examined approximately 18,000 Windows driver samples collected via YARA rules from the VirusTotal database. Excluding known vulnerable drivers, the team identified several hundred file hashes linked to 34 unique, previously unrecognized vulnerable drivers.

The investigation covered drivers from the Windows Driver Model (WDM) and Windows Driver Framework (WDF), and the company has published a list of file names associated with the problematic drivers. These include products from leading BIOS, PC, and chip manufacturers.
The exploitation of any of these drivers could permit attackers without system privileges to gain complete control over the target device.
“By exploiting the vulnerable drivers, an attacker without the system privilege may erase/alter firmware, and/or elevate privileges,” states VMware’s blog.
Developers of the susceptible drivers were notified in the spring of 2023; however, only two—Phoenix Technologies and Advanced Micro Devices (AMD)—have addressed the vulnerabilities.
VMware has developed proof-of-concept exploits for several of the vulnerable drivers to demonstrate their potential use in erasing firmware or for privilege escalation. The company has also provided an IDAPython script which was utilized to automate the discovery of the vulnerable WDM and WDF drivers.