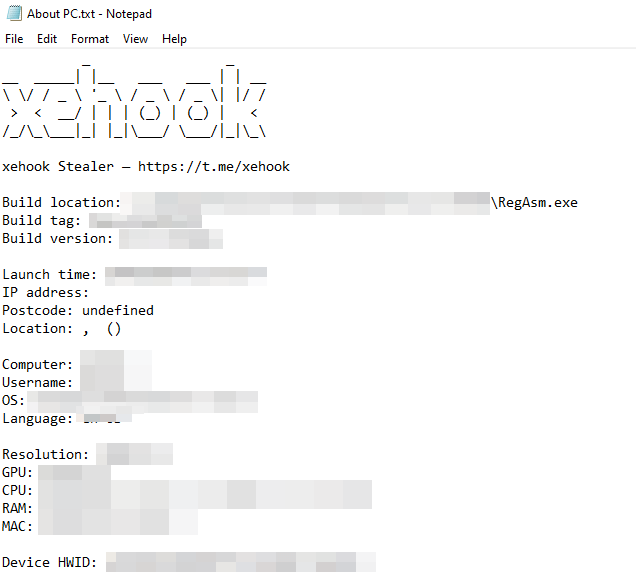
In a detailed analysis, researchers at Cyble Research and Intelligence Labs (CRIL) have shed light on a sophisticated new threat: Xehook Stealer. This sophisticated piece of malware targets the Windows operating system and is developed using the .Net programming language.
Xehook Stealer: Capabilities and Danger

The Xehook Stealer goes beyond traditional password and credit card theft, posing an exceptionally broad threat. Xehook Stealer sets itself apart by offering dynamic data collection from all Chromium and Gecko-based browsers. This functionality is not just limited to traditional data theft but extends to supporting over 110 cryptocurrencies and 2FA extensions, making it a highly versatile tool in the hands of malicious actors. The threat actor (TA) behind Xehook has meticulously designed it to include customizable build settings, seamless integration with Telegram for real-time notifications, and the ability to send logs directly to the messaging platform. Furthermore, the stealer provides an API for creating custom traffic bots and features for recovering dead Google cookies.
The stealer’s ability to gather a wide range of data — from passwords, cookies, autofill information, and credit cards to sessions from messaging platforms like Telegram and Discord — positions Xehook as a significant threat to personal and organizational cybersecurity. Moreover, its support for over 15 desktop cryptocurrency wallets and a recursive file grabber for collecting specific file formats from user directories highlights its targeted approach toward financial theft.
The Evolution of a Threat
CRIL’s investigation uncovered a disturbing pattern. Evidence strongly indicates Xehook Stealer is the latest iteration in an ongoing malware development campaign. Threat actors appear to have started with the Cinoshi project, offering a free malware-as-a-service model, then progressed to the Agniane stealer, and finally, the commercialized Xehook Stealer. This evolution highlights the importance of tracking threat actor groups and their malware lineages.
Interestingly, Xehook Stealer is commercialized through a subscription model, accessible on a monthly, quarterly, and semi-annual basis, with prices ranging from $50 to $600 for an unlimited period. This pricing strategy, combined with an additional $100 for indefinite API access, ensures comprehensive support and functionality for its subscribers.
CRIL’s analysis further reveals that Xehook is an upgraded iteration of the Agniane stealer, sharing numerous similarities in their codebase and functionalities. This revelation, coupled with their communication with the same command-and-control (C&C) server, suggests a strong connection between the two variants.
Distribution and Defense Evasion
Xehook Stealer is commonly spread through the SmokeLoader malware, increasing its reach. Additionally, it employs techniques designed to make analysis difficult, such as a time-based restriction that can hinder researchers’ efforts.
Recommendations: Protecting Yourself and Your Organization
- Endpoint Security is Key: Endpoint detection and response (EDR) solutions, antivirus software, and application whitelisting are crucial layers of defense.
- User Education: Train staff to recognize phishing attempts, avoid suspicious links or downloads, and use strong, unique passwords.
- Threat Intelligence: Subscribing to reputable threat intelligence sources keeps you informed about evolving malware trends and tactics.
- Behavior-Based Detection: Solutions focused on detecting anomalous system behavior offer a proactive approach against novel threats like Xehook.