Source: Seqrite Labs
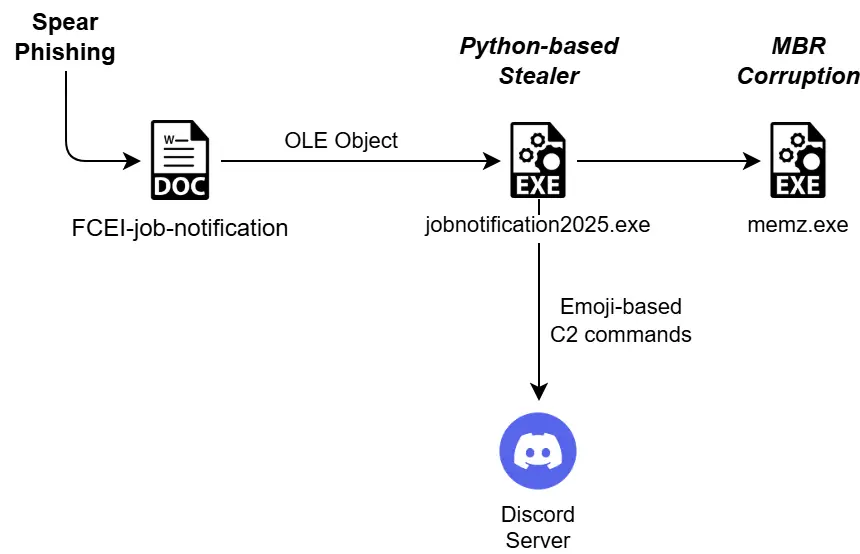
A newly discovered ransomware campaign, dubbed XELERA, is targeting job seekers in India with fraudulent Food Corporation of India (FCI) job listings. Security researchers at Seqrite Labs APT-Team have uncovered a sophisticated spear-phishing attack that delivers a Python-based ransomware via malicious documents disguised as job notifications.
According to Seqrite Labs, “These are targeted towards individuals aiming for various technical job positions at FCI with a variant of ransomware known as Xelera.” The attack exploits the growing demand for government jobs by luring victims into opening an infected Word document that initiates a multi-stage malware infection chain.
The attack begins with a malicious Word document named FCEI-job-notification.doc, which outlines job vacancies, eligibility criteria, and exam details for various FCI roles.
Seqrite Labs explains, “The document contains three pages of information which starts with the decoy mentioning the number of vacancies at Food Corporation of India and the type of workforce required.” While appearing legitimate, the document harbors embedded malware hidden inside OLE Streams.
When the victim opens the document, the malicious OLE object executes an embedded PyInstaller-based executable called jobnotification2025.exe, which is responsible for deploying the ransomware.
PyInstaller is a commonly abused tool that allows Python scripts to be converted into standalone executables. Threat actors frequently use it to bypass antivirus detection.
Seqrite Labs reports, “PyInstaller, stands as one of the favorite tools of malicious software developers who prefer python scripting… Previously, HolyCrypt and other well-known lockers and stealers have abused PyInstaller to deploy malware In-The-Wild.”
Upon execution, the PyInstaller package extracts multiple Python scripts that initiate a Discord-controlled malware operation.
The XELERA ransomware is controlled via a Discord bot, allowing attackers to remotely execute malicious commands on the infected machine. The malware is designed to:
- Steal Browser Credentials – Extracts passwords, cookies, and browsing history from Google Chrome and Microsoft Edge.
- Exfiltrate Files – Uploads sensitive documents to the attacker’s Discord server.
- Disrupt Victim’s System – Locks the PC, changes wallpapers, and distorts visuals.
- Trigger Annoyance-Based Attacks – Plays loud audio, blocks mouse input, and floods the system with spam notifications.
Seqrite Labs provides a full list of commands, including:
nomouse start/stop– Disables user input (mouse and keyboard).seizure– Flashes the screen repeatedly, mimicking a seizure-inducing effect.bsod– Triggers a Blue Screen of Death (BSOD), crashing the system.thugfiles– Corrupts and renames all files in the Downloads/Documents folder.restartpc– Forces a system restart.getpwds– Extracts stored passwords from browsers.
Seqrite Labs warns, “Once a victim is affected after executing the malicious document, the threat actor uses the Discord Bot to perform certain nefarious tasks, such as stealing browser-based credentials, spamming the target with certain derogatory messages and much more.”
Unlike traditional ransomware, which encrypts files and demands a ransom, XELERA functions more as a destructive malware tool with:
- Master Boot Record (MBR) Corruption – Prevents victims from booting their system.
- File Deletion & Corruption – Deletes and overwrites files without offering recovery options.
- Forced Visual & Sensory Disruptions – Disrupts user experience with screen effects and loud sounds.
Seqrite Labs highlights a particularly damaging feature: “The malware begins its execution by parsing command-line arguments to determine its mode of operation. If the ‘/watchdog’ argument is present, it activates a monitoring thread and registers a hidden window to ensure persistence.”
The malware even downloads and executes MEMZ.exe, a well-known MBR corrupter, which disables the victim’s operating system permanently.
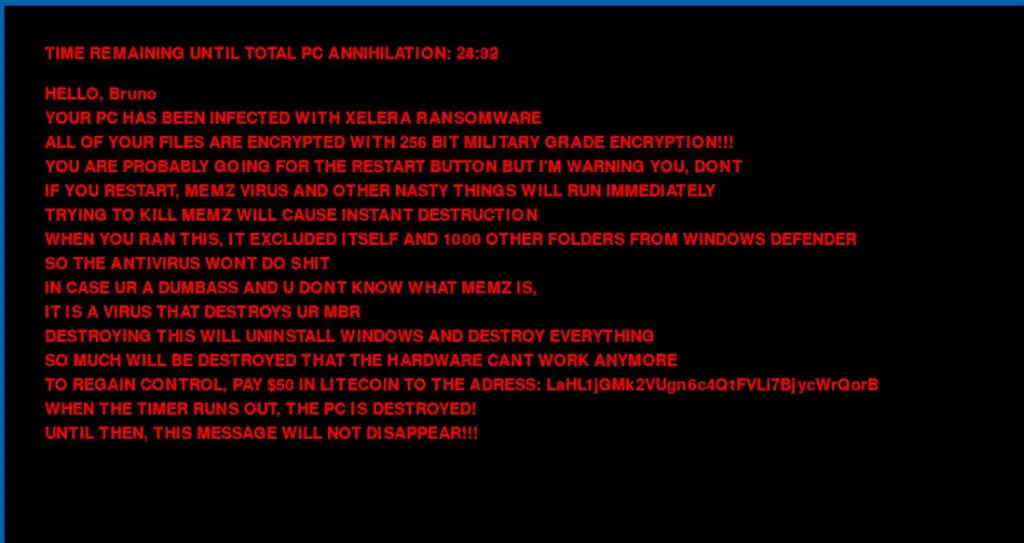
Once XELERA ransomware completes its attack, victims are presented with a ransom note demanding payment in Litecoin to restore their system.
Seqrite Labs states, “The ransomware message can be seen, with a Litecoin address for submitting the ransom amount. Looking into the address of the cryptocurrency wallet mentioned, we can see that there have been a total of 16 transactions using the same wallet address.”
It remains unclear whether victims have successfully recovered their data after making payments.
Related Posts:
- Silent Lynx APT Group: A New Espionage Threat Targeting Central Asia
- Cyber-Espionage Campaign Unveiled: Operation Cobalt Whisper Hits Sensitive Industries
- From SideCopy to Transparent Tribe: Pakistan APTs Hit Indian Government With RATs
- Multi-Layered Attack: Formbook Stealer Bypasses Detection with Memory-Based Execution
- India Post Customers Targeted in Massive Phishing Scam