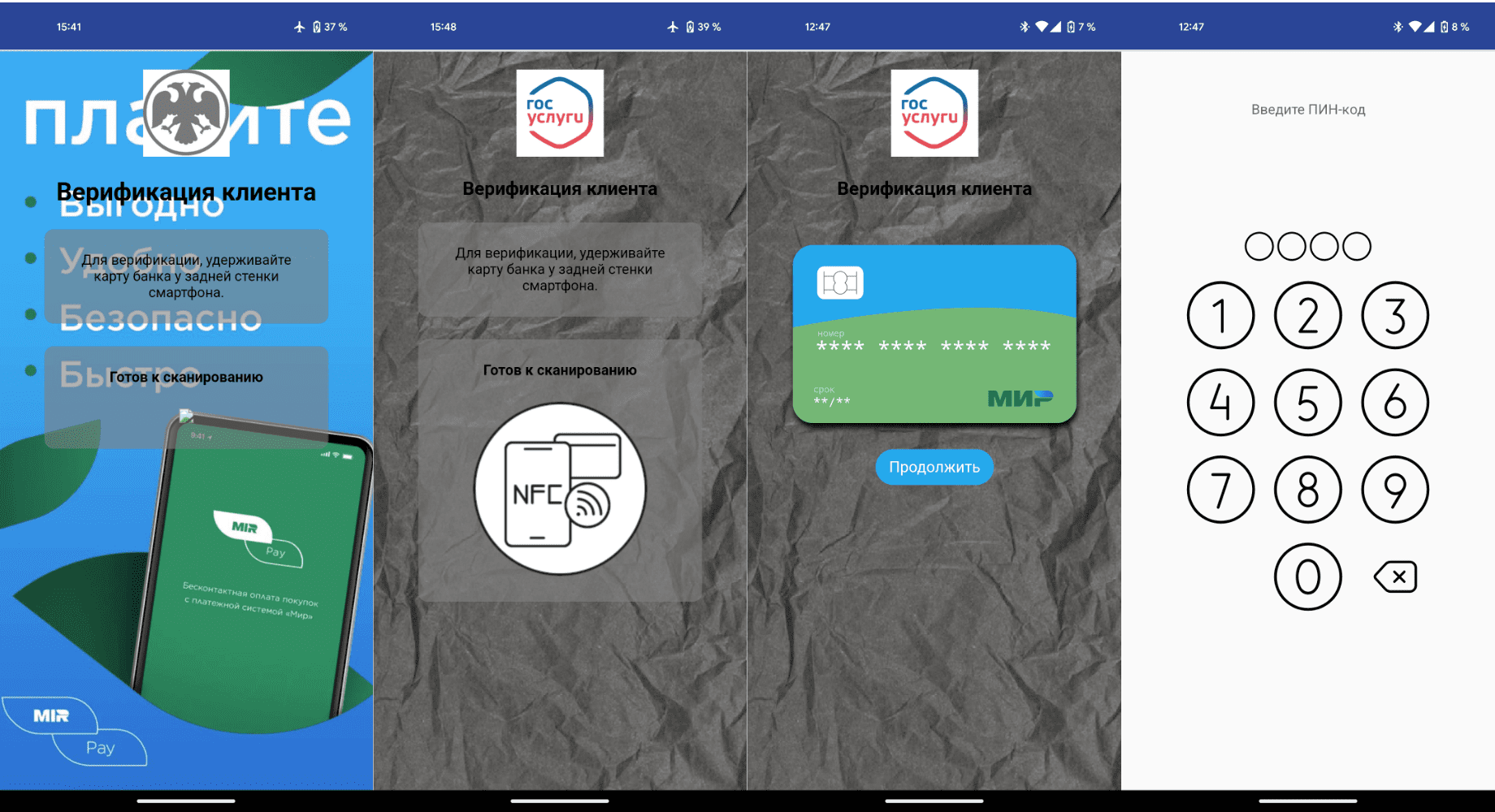
Screens that ask the victim to place their bank card on the back of their smartphone | Source: Doctor Web
In a concerning development for cybersecurity, malware analysts at Doctor Web have identified a new wave of attacks involving the NGate banking trojan, now targeting Russian users. This sophisticated malware exploits Near Field Communication (NFC) capabilities, allowing attackers to siphon money from victims’ accounts at ATMs or make contactless payments—without the victim’s direct involvement.
The NGate trojan first gained notoriety in the autumn of 2023, when it was used to attack customers of major Czech banks. Its approach combined social engineering, phishing, and malware to exploit the NFC functionality of compromised devices. Although Czech law enforcement curtailed the campaign, its framework has been repurposed for Russian targets, leveraging local nuances for illicit financial gains.
“The attackers’ strategy involved a combination of social engineering, phishing, and the use of malware,” the Doctor Web report noted. “When used together, these standard tactics created a rather innovative scenario.”
The attack typically begins with a phone call from fraudsters posing as representatives of a government service or financial institution. They claim the victim is eligible for a social benefit or monetary incentive, providing a link to a fraudulent website. This site hosts a malicious APK disguised as an application for Gosuslugi (the government services portal), the Bank of Russia, or other prominent institutions.
Once installed, the NGate trojan—based on a malicious modification of the open-source NFCGate debugging application—takes control. According to Doctor Web, “the criminals have modified the source code by adding user interfaces similar to the official applications and enabling the NFC data relay mode.” This includes functionality to capture NFC traffic and remotely transmit sensitive card details such as the card number and expiry date.
Victims are instructed to place their payment card on the back of their smartphone and input their PIN into the app. Unbeknownst to them, all card data is instantly relayed to the attacker’s device.
With the captured card data, attackers have two primary methods of exploitation:
- ATM Withdrawals: Using the victim’s card information, attackers approach an ATM, tap their phone to transmit the digital card data, and complete the transaction with the PIN provided by the victim.
- Contactless Payments: The trojan facilitates seamless digital payments, allowing attackers to use the victim’s funds for purchases or transfers.
Doctor Web emphasized that the compromised smartphone does not need to be rooted for NGate to access NFC data, making the malware even more dangerous and accessible.
To protect against this growing threat, Doctor Web analysts recommend the following:
- Never share your bank card PIN or CVV codes.
- Use reputable antivirus programs to block malicious downloads and installations.
- Verify the authenticity of web pages requesting financial information.
- Only install apps from official sources such as AppGallery or Google Play.
- Avoid engaging with scammers. If contacted by someone claiming to be from a bank or government agency, hang up and verify the claim using official contact details.
“Do not talk to scammers. If you receive an unexpected call from the police, a bank, or any other organization, simply hang up,” the report advises.