NGate Android Malware Steals NFC Payment Data at ATMs
Researchers from ESET have uncovered a new malicious campaign targeting customers of three Czech banks. The attackers employed a unique malware known as NGate, which transmitted payment card data from victims through infected Android devices to the perpetrator’s phone.
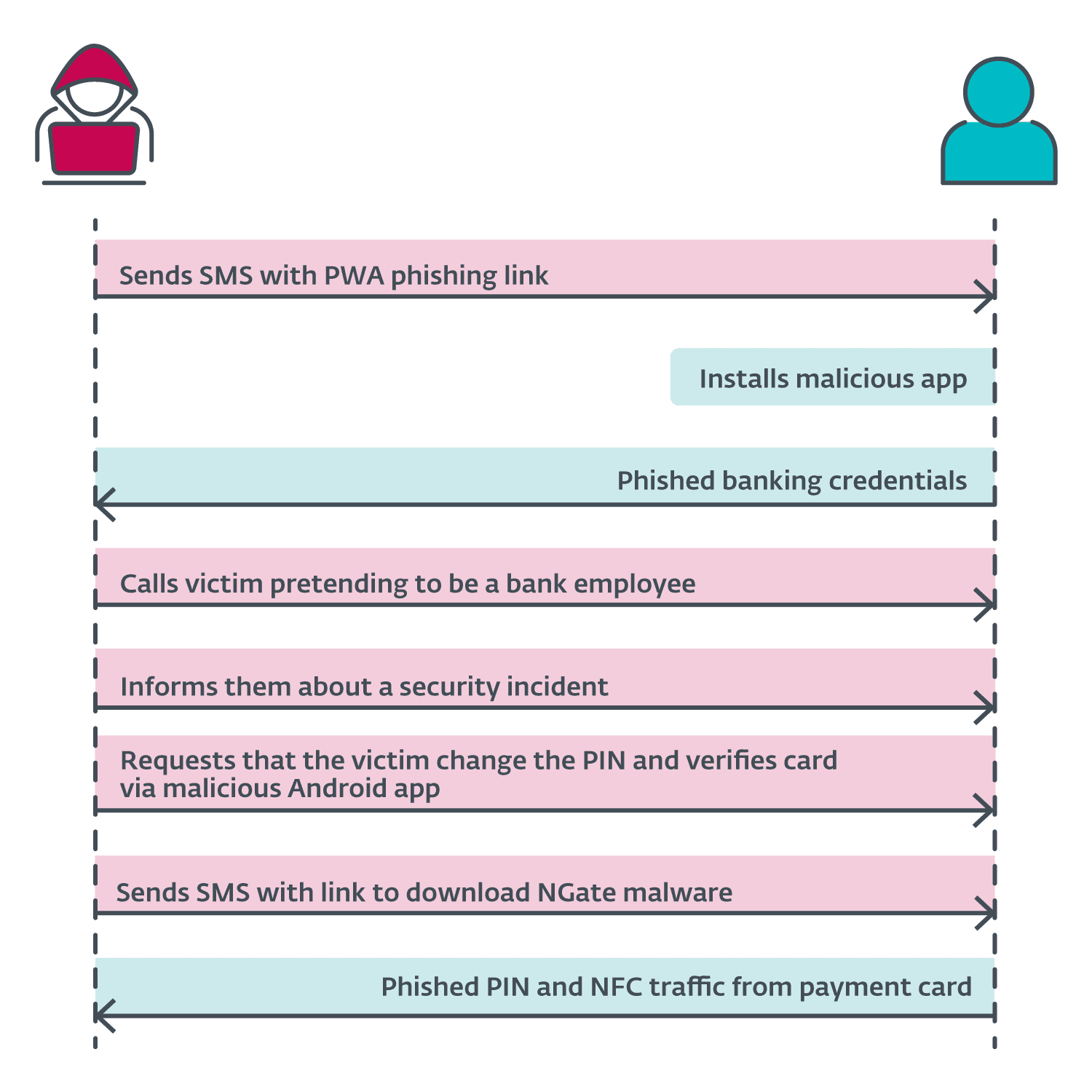
The attack was a combination of standard social engineering techniques, phishing, and Android malware. It is believed that the fraudsters sent messages to random phone numbers, attempting to lure bank customers into falling for fake notifications.
Since November 2023, the group of attackers has been actively using Progressive Web Apps (PWA) and WebAPK to deliver malware. However, in March 2024, a new technology, NGate, was deployed, enabling the copying of NFC data from victims’ payment cards and transmitting it to the attacker’s device. This allowed the fraudsters to simulate the card and withdraw money from ATMs.
This attack represents the first recorded instance of Android malware with such capabilities. Notably, the victims’ devices did not require rooting for NGate to operate, whereas even manual NFC card emulation on Android traditionally requires root access.
The primary objective of the attackers was the unauthorized withdrawal of funds from victims’ bank accounts via ATMs. If the NFC method failed, the attackers had a backup plan—transferring the victim’s funds to other accounts.
NGate Adnroid malware was closely linked to phishing activity carried out by the group in the Czech Republic since November 2023. However, after the arrest of a suspect in March this year, the attackers’ activity decreased. The detained 22-year-old man is suspected of stealing money from ATMs in Prague. At the time of his arrest, he was found in possession of 160,000 Czech korunas (over 6,000 euros), stolen from the last three victims. Meanwhile, the total damage could be significantly higher.
The attackers used Progressive Web Apps to disguise the malware as legitimate banking applications. These apps created the illusion of a real banking interface, prompting victims to enter their credentials, which were then sent to the attackers’ servers.
With the advent of NGate, the attack became even more sophisticated. The malware utilized a tool called NFCGate, developed in Germany, which was initially intended for analyzing NFC traffic. NGate used this tool to transmit payment card data from victims to the attacker’s device, enabling the latter to withdraw money.
Such attacks can be prevented by following a few simple rules: verifying the authenticity of websites, downloading apps only from official sources, keeping PIN codes secret, and using reliable apps to protect mobile devices.
This story underscores the importance of digital security and vigilance in our time. Even familiar technologies like NFC can be exploited if users do not exercise sufficient caution. Protecting personal data and remaining vigilant are crucial factors in preventing such threats.





