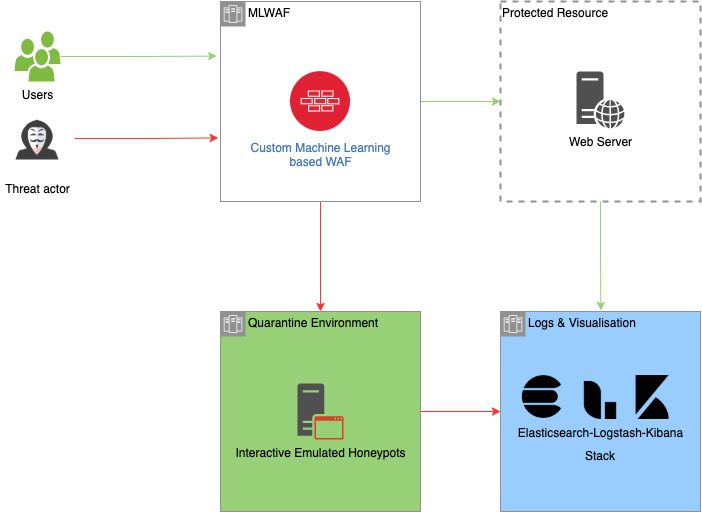
High-level architecture of NGWAF with expected traffic flows from different parties
What is the N3XT ST3P?
With the explosive growth of web applications since the early 2000s, web-based attacks have progressively become more rampant. One common solution is the Web App Firewall (WAF). However, tweaking the rules of current WAFs to improve the detection mechanisms can be complex and difficult. NGWAF seeks to address these drawbacks with a novel machine learning and quarantine-to-honeypot based architecture.
Inspired by actual pain points from operating WAFs, NGWAF intends to simplify and reimagine WAF operations through the following processes:
| Pain point | NGWAF Feature |
|---|---|
| Maintenance of detection mechanisms and rules can be complex | Leverage machine learning to automate the process of creating and updating detection mechanisms |
| Immediate blocking of malicious traffic reduces the chances of learning from threat actor behavior for future WAF improvements | Threat elimination through redirected quarantine as opposed to conventional dropping and blocking of malicious traffic |
To make deployment simple and portable, we have containerised the different components in the architecture using docker and configured them in a docker-compose file. This allows running it on a fresh install to be quick and easy as the dependencies are handled by docker automatically. The deployment can be expanded to be deployed into a local or cloud provider-based kubernetes cluster, making it scalable as users can increase the number of nodes/pods to handle large amounts of traffic.
How does NGWAF work?
NGWAF runs out-of-the-box with three key components, these components as mentioned above are all containerised and are scalable according to the desired usage. The protected resource can be customised by making a deployment change within the setup.

Key Benefits
NGWAF was engineered with the following key user benefits in mind:
1. Rule Complexity Reduction
NGWAF replaces traditional rulesets with deep learning models to reduce the complexity of managing and updating rules. Instead of manually editing rules, NGWAF’s machine learning automates the pattern learning process from malicious data. Data collected from the quarantine environment are automatically scrubbed and batched, allowing it to be retrained into our detection model if desired.
2. Cyber Deception
NGWAF adopts a novel architecture consisting of an interactive and quarantine environment built to isolate potential hostile attackers. Unlike conventional WAFs which block upon detection, NGWAF diverts threat actors to emulated systems, trapping them to soften the impact of their malicious actions. The environment also acts as a sinkhole to gather current attack methods, enabling the observation and collection of malicious data. These data can be used to further improve NGWAF’s detection capability.
3. Compliance with Internationally Recognised Standards
The guiding principle behind the creation of NGWAF is to guard against the risks highlighted in the Open Web Application Security Project’s standard awareness document – The OWASP Top 10 2021.
Training data and compliance checks for NGWAF are collected and conducted based on this requirement.
Install & Use
Copyright (c) 2021 FA-PengFei