nightHawk Response
Custom built an application for asynchronus forensic data presentation on an Elasticsearch backend.
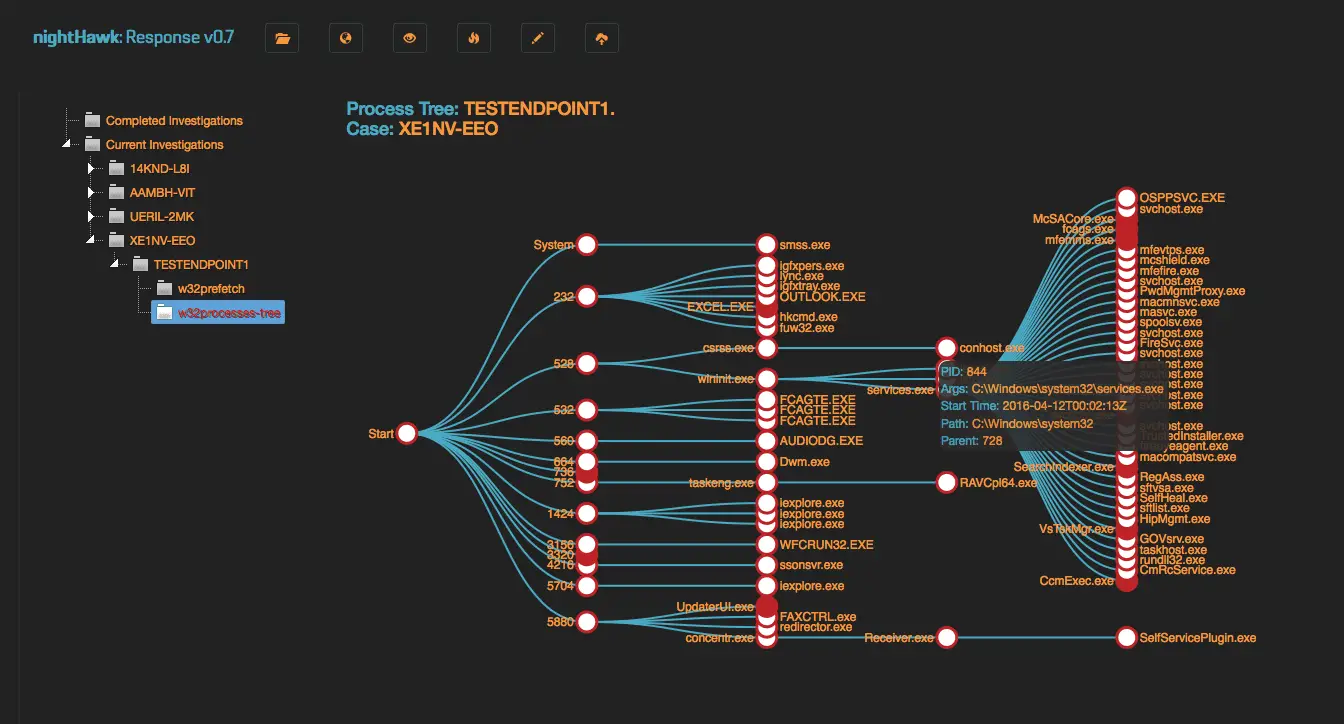
This application is designed to ingest a Mandiant Redline “collections” file and give flexibility in search/stack and tagging.
The application was born out of the inability to control multiple investigations (or hundreds of endpoints) in a single pane of glass.
To ingest redline audits, we created nightHawkResponse, a fully fledge GOpher application designed to accompany this framework. The source code to the application is available in this repo, a binary has been compiled and is running inside the iso ready to ingest from first boot.
Features
- Single view endpoint forensics (multiple audit types).
- Global search.
- Timelining.
- Stacking.
- Tagging.
- Interactive process tree view.
- Multiple file upload & Named investigations.
Installation
- Version 1.0.4 would work on any Ubuntu x64 OS (we have tested in Ubuntu 16.04LTS)
- Update Ubuntu to latesth patch
- Download release/nhr-1.0.4.tar.gz
- Unarchive nhr-1.0.4.tar.gz
- Change directory to nhr-1.0.4
- Change nhr-setup.sh to executable (chmod +x nhr-setup.sh)
- Install dependencies and nightHawk Response packages (sudo ./nhr-setup.sh install)
Note: Internet access is required during installation. - Initial installation may fail to create Elasticsearch index. If that happens please re-run (sudo ./nhr-setup.sh install)
- Verify all the components are running
—- sudo systemctl status elasticsearch
—- sudo systemctl status kibana
—- sudo systemctl status rabbitmq-server
—- sudo systemctl status nginx
—- sudo systemctl status nighthawk-api
—- sudo systemctl status nighthawk-worker - You can access it by browsing to https://ipaddress
- Default username and password is both admin/admin
Demo
Source: https://github.com/biggiesmallsAG/