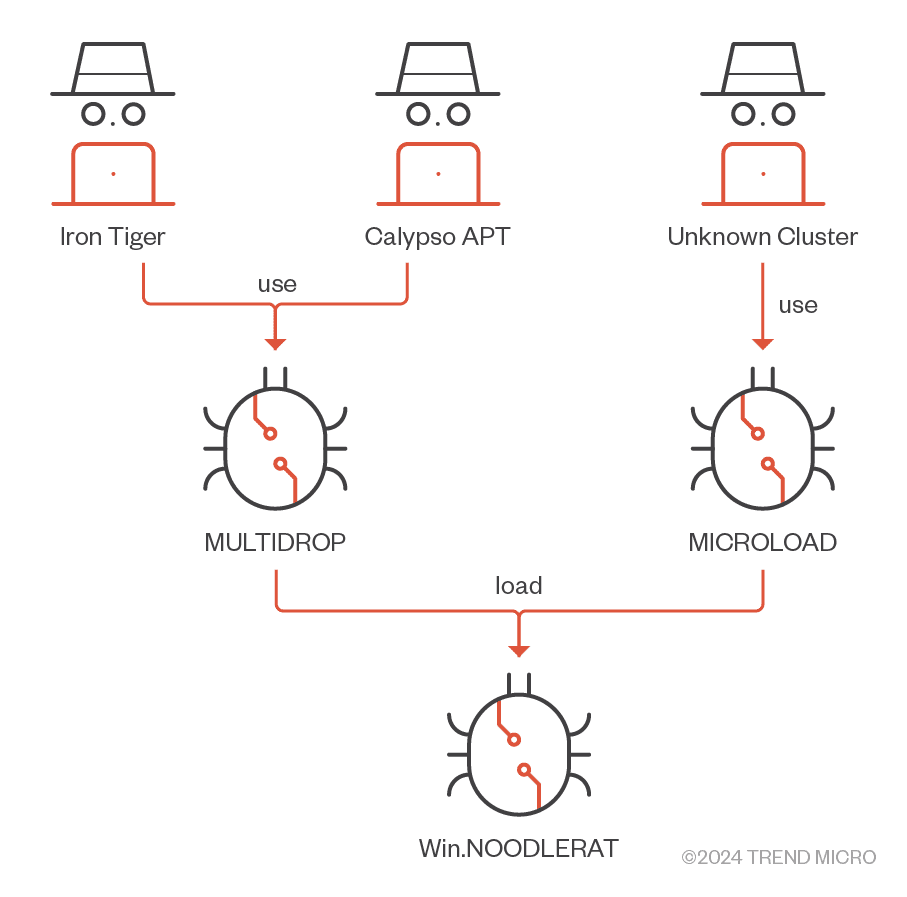
Relations of Win.NOODLERAT with threat groups
Cybersecurity researchers at Trend Micro have unveiled a previously undocumented backdoor malware dubbed “Noodle RAT,” believed to be utilized by Chinese-speaking groups in espionage and cybercrime operations across the Asia-Pacific region since 2022.
Noodle RAT, also known as ANGRYREBEL or Nood RAT, exists in both Windows (Win.NOODLERAT) and Linux (Linux.NOODLERAT) versions, demonstrating its versatility in targeting different operating systems. Despite its existence since 2016, Noodle RAT has evaded proper classification until now, often being misidentified as variants of existing malware families such as Gh0st RAT or Rekoobe.
This backdoor has been linked to various espionage campaigns targeting countries like Thailand, India, Japan, Malaysia, and Taiwan. It has also been observed in cybercrime operations for financial gain. Noodle RAT’s modular design and extensive capabilities, including file manipulation, remote code execution, and proxy functionalities, make it a potent tool for threat actors.

Win.NOODLERAT:
- Functionality: A shellcode-formed in-memory modular backdoor capable of downloading/uploading files, running additional modules, and acting as a TCP proxy.
- Installation: Utilizes loaders like MULTIDROP and MICROLOAD to deploy the payload.
- C&C Communication: Supports TCP, SSL, and HTTP, with communications encrypted using RC4 and a custom algorithm involving XOR and AND instructions.
Linux.NOODLERAT:
- Functionality: Includes reverse shell capabilities, file download/upload, scheduling execution, and SOCKS tunneling.
- Initialization: Typically deployed via exploits against public-facing applications, it performs process name spoofing and decrypts its configuration using RC4.
- C&C Communication: Uses TCP and HTTP, with encryption algorithms differing for command processing (RC4, XOR+AND) and reverse shell sessions (HMAC_SHA1, AES128-CBC).
Both Windows and Linux versions of Noodle RAT implement a range of backdoor commands, categorized into distinct types based on command IDs. These commands facilitate various malicious activities, from file operations to maintaining persistent communication with the C&C server.
Trend Micro’s analysis also uncovered a control panel and builder for Linux.NOODLERAT, suggesting the existence of a well-developed malware ecosystem. Notably, these server-side components were submitted with release notes in Simplified Chinese, hinting at the involvement of a developer and client relationship.
The exposure of Noodle RAT sheds light on the evolving threat landscape and highlights the importance of continuous research and analysis to identify and mitigate new and emerging threats. Organizations and individuals are urged to remain vigilant and implement robust security measures to protect against such backdoor malware.
For a detailed technical analysis of Noodle RAT, please refer to Trend Micro’s research blog.