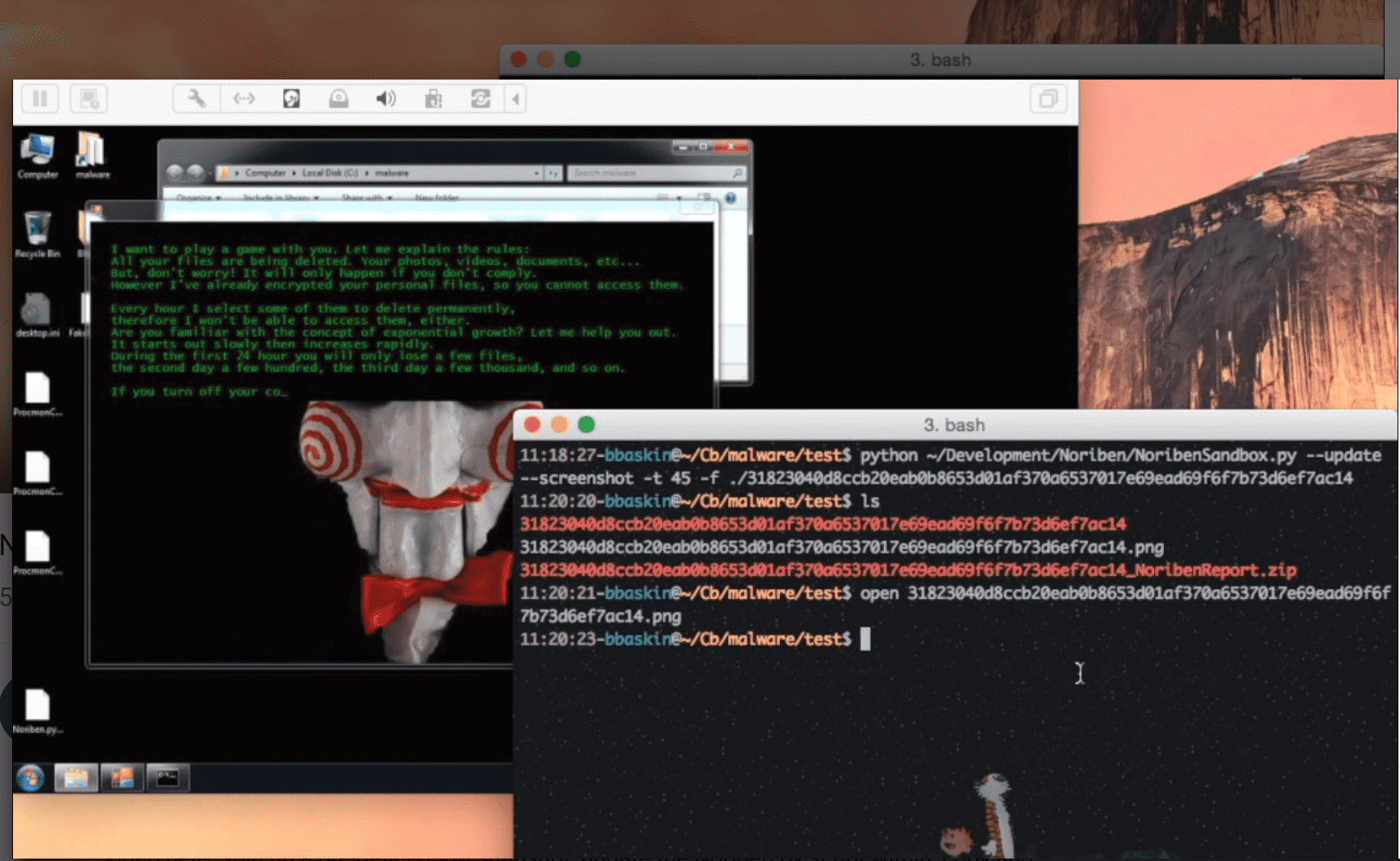
Noriben Malware Analysis Sandbox
Noriben is a Python-based script that works in conjunction with Sysinternals Procmon to automatically collect, analyze, and report on runtime indicators of malware. In a nutshell, it allows you to run your malware, hit a keypress, and get a simple text report of the sample’s activities.
Noriben allows you to not only run malware similar to a sandbox but to also log system-wide events while you manually run malware in ways particular to make it run. For example, it can listen as you run malware that requires varying command-line options, or user interaction. Or, to watch the system as you step through malware in a debugger.
Noriben only requires Sysinternals procmon.exe (or procmon64.exe) to operate. It requires no pre-filtering (though it would greatly help) as it contains numerous whitelist items to reduce unwanted noise from system activity.
For a more detailed explanation, see my slide deck from Black Hat 2015 Arsenal. And a more detailed blog post.
Cool Features
If you have a folder of YARA signature files, you can specify it with the –yara option. Every new file creates will be scanned against these signatures with the results displayed in the output results.
If you have a VirusTotal API, place it into a file named “virustotal.api” (or embed directly in the script) to auto-submit MD5 file hashes to VT to get the number of viral results.
You can add lists of MD5s to auto-ignore (such as all of your system files). Use md5deep and throw them into a text file, use –hash to read them. This will ultimately go under changes, though.
You can automate the script for sandbox-usage. Using -t to automate execution time, and –cmd “path\exe” to specify a malware file, you can automatically run malware, copy the results off, and then revert to run a new sample.
The –generalize feature will automatically substitute absolute paths with Windows environment paths for better IOC development. For example, C:\Users\malware_user\AppData\Roaming\malware.exe will be automatically resolved to %AppData%\malware.exe.
Changelog
Version 1.8.4 – 22 Nov 19
- Minor updates. Added ability to run a non-executable, such as a Word document
Download
git clone https://github.com/Rurik/Noriben.git
Usage
Demo
Copyright 2015 Brian Baskin
Source: https://github.com/Rurik/