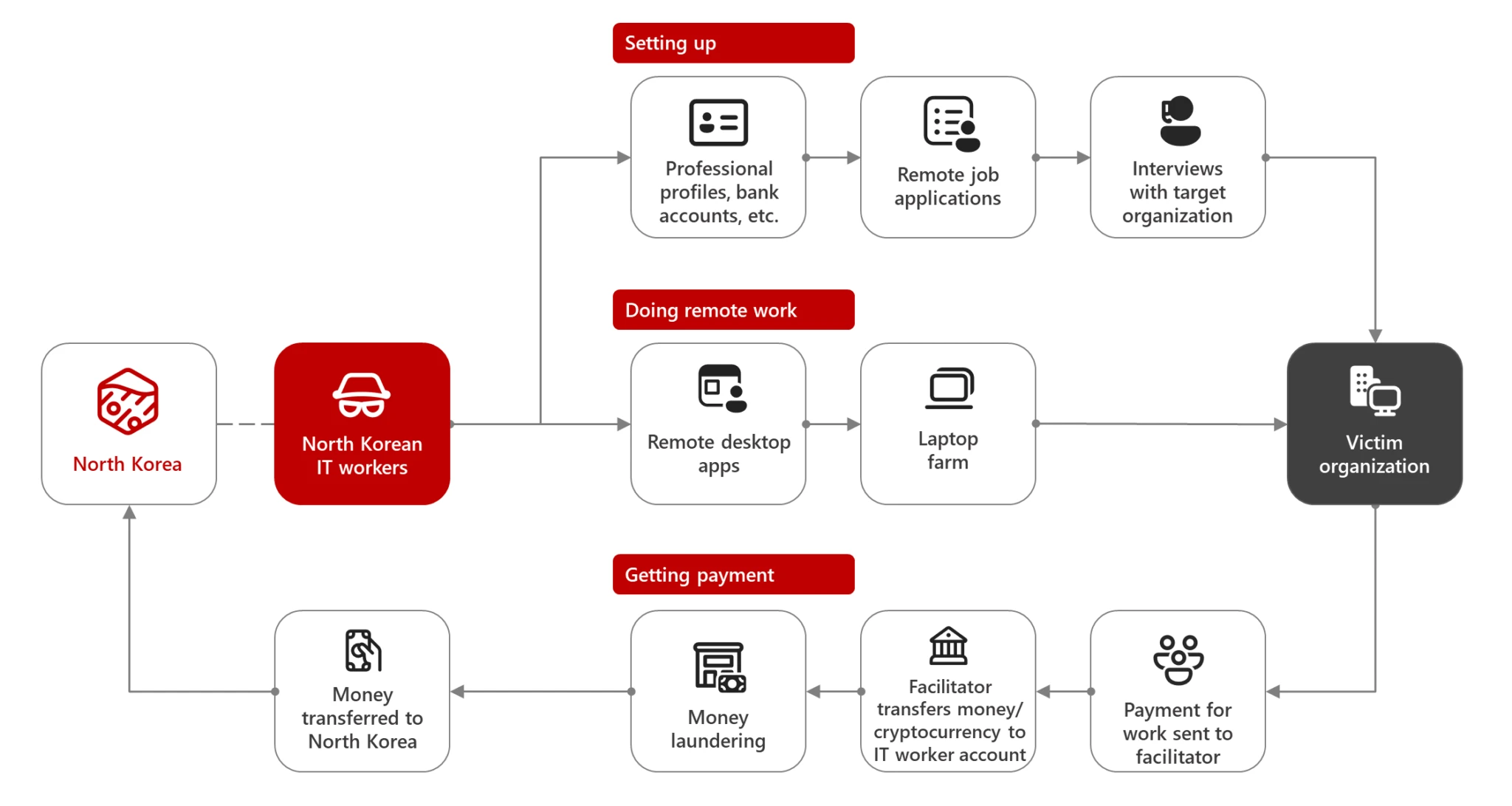
The North Korean IT worker ecosystem
At CYBERWARCON 2024, Microsoft Threat Intelligence unveiled groundbreaking research on two major nation-state cyber actors: North Korea and China. These revelations provide a closer look at their tactics, techniques, and motivations, underlining the sophistication and reach of their operations in cyberspace.
North Korea: From Cryptocurrency Theft to IT Worker Ecosystems
North Korea has become a major player in the global cyber threat landscape, with groups like Sapphire Sleet and Ruby Sleet spearheading diverse campaigns.
- Sapphire Sleet: Cryptocurrency Thieves
Active since at least 2020, Sapphire Sleet has stolen over $10 million in cryptocurrency within a six-month window. Their primary method involves masquerading as venture capitalists or recruiters, deploying malware through cleverly disguised phishing scripts and job assessment tools. As Microsoft noted: “The threat actor then works towards obtaining cryptocurrency wallets and other credentials on the compromised device, enabling the threat actor to steal cryptocurrency.” - Ruby Sleet: Targeting Defense and Aerospace
Ruby Sleet has escalated their phishing sophistication by signing malware with compromised certificates and conducting supply chain attacks. In December 2023, they replaced legitimate software with backdoored versions targeting Korean defense contractors. Such operations are believed to support North Korea’s missile and drone research. “Ruby Sleet has targeted and successfully compromised aerospace and defense-related organizations,” Microsoft stated in their report. - IT Worker Ecosystem
North Korea’s IT workers operate covertly in countries like China and Russia, generating revenue and accessing sensitive systems. These workers use fake profiles and AI-enhanced resumes to secure jobs and siphon critical information. According to Microsoft: “this group of North Korean IT workers appears to have made at least 370,000 US dollars through their efforts.“
China: Storm-2077 – Intelligence Collection Across Sectors
The Chinese threat actor Storm-2077 epitomizes the complexity of tracking cyber operations from China. Since January 2024, this group has targeted sectors including government, aviation, and telecommunications. Using phishing and cloud exploitation, Storm-2077 focuses on email data theft to extract sensitive information for long-term intelligence use.
Microsoft’s analysts described their approach: “Access to email accounts and the ability to steal email communication could enable an attacker to further their operations.”
Storm-2077’s operations highlight the blurred lines between cybercrime and state-sponsored espionage. “All sectors appear to be on the table, leaving no targets behind,” noted Microsoft.
Conclusion
North Korea and China demonstrate an ability to adapt and innovate, leveraging advanced tools and global networks to pursue their strategic objectives. For organizations, vigilance and proactive defense strategies are essential to counteract these evolving threats.
Related Posts:
- North Korean Threats Target TeamCity CVE-2023-42793 Bug: Microsoft Raises Alarm
- CVE-2024-7971: North Korean APT Citrine Sleet Exploits Chromium Zero-Day
- North Korean Hacking Group Sapphire Sleet Employs Social Engineering to Steal Cryptocurrency
- Emerging Cyber Threat: Moonstone Sleet Identified as New North Korean Threat Actor
- Expert: North Korean hackers harvest 11,000 Bitcoins in 2017