
In a recent report, the Datadog Security Research Team exposed the latest nefarious activities of the Tenacious Pungsan group, a North Korean cyber-espionage threat actor. Known for its persistence, the group has continued its efforts to target developers using a new wave of name-squatting attacks on popular open-source software repositories.
The Datadog Security Team, using their in-house tool GuardDog, identified a significant supply chain attack on the npm ecosystem. This attack involved several backdoored versions of widely used npm packages, including passports-js, bcrypts-js, and blockscan-api, all altered to include malicious JavaScript code designed to steal sensitive information.
The attackers employed namesquatting—creating packages with names very similar to legitimate, trusted software hoping that developers would mistakenly download the malicious versions. For instance, passports-js is a backdoored version of the popular passport npm package, used in authentication frameworks for Express applications. Similarly, bcrypts-js is a malicious imitation of bcryptjs, a bcrypt library with millions of weekly downloads.
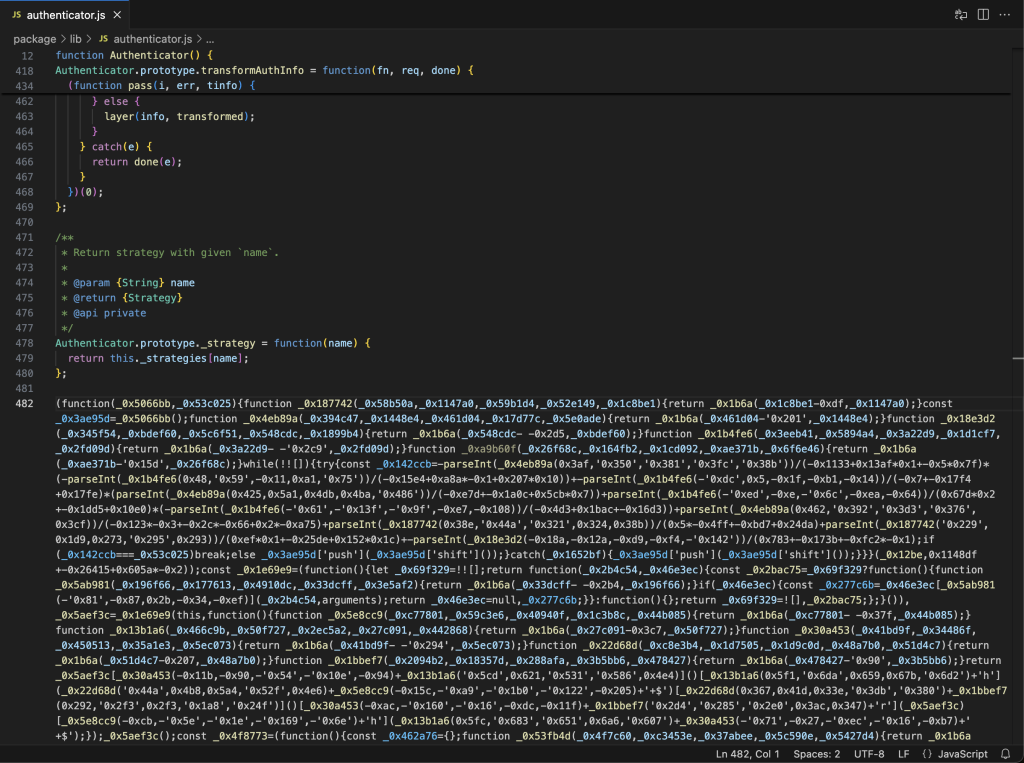
A single, highly obfuscated line of JavaScript buried within otherwise clean source code sets these backdoored packages apart. This obfuscation was key in disguising the malicious intent, hiding a variant of BeaverTail, a JavaScript infostealer and downloader malware used by DPRK actors in the infamous Contagious Interview campaign. The malware targets cryptocurrency wallets, login keychains, and browser caches, exfiltrating data to attacker-controlled command-and-control (C2) servers.
The obfuscation found in these packages was sophisticated but not impervious to analysis. By using open-source deobfuscation tools, Datadog was able to reverse-engineer the malicious code and uncover the hidden agenda of the attackers. The same malware was identified across all three compromised packages, though slight differences in the obfuscation pointed to possible variant-specific campaigns.
Datadog’s research team drew clear parallels between this latest attack and the broader Contagious Interview campaign, which has been ongoing since 2023. The Tenacious Pungsan group has been linked to this campaign, which primarily targets developers seeking jobs in the tech industry. According to the report, the attackers reused infrastructure from earlier campaigns, including C2 servers and directory structures.
One of the key pieces of evidence linking the Tenacious Pungsan group to Contagious Interview is the use of InvisibleFerret, a second-stage backdoor downloaded by BeaverTail. The malware uses predefined URLs containing campaign IDs, which allowed the researchers to trace this specific campaign back to earlier DPRK-linked operations.
By exploiting open-source supply chains, these threat actors can inject malicious code directly into the software ecosystem, putting countless downstream users at risk. The Datadog report warns, “Copying and backdooring legitimate npm packages continues to be a common tactic of threat actors in this ecosystem. These campaigns, along with Contagious Interview more broadly, highlight that individual developers remain valuable targets for these DPRK-linked threat actors.”
Related Posts:
- North Korean Hackers Target Windows Users with Malicious NPM Packages
- North Korean Threat Actors Targeting Tech Job Seekers with Contagious Interview Campaign
- AWS Under Siege: Attackers Target Vaults, Buckets, and Secrets in Widespread Campaign
- North Korean Hackers Launch Job Interview Scam to Deploy BeaverTail and InvisibleFerret Malware