North Korean Espionage Group Springtail Unveils New Linux Backdoor in Escalating Cyber Campaign

Symantec’s Threat Hunter Team has revealed a concerning development in the cyber espionage landscape: the North Korean state-sponsored group Springtail (also known as Kimsuky) has added a new Linux backdoor, dubbed Gomir, to its arsenal. This discovery comes on the heels of a recent campaign targeting South Korean organizations, further highlighting the group’s persistent and evolving cyber capabilities.

Springtail is a well-organized espionage group that has been active since at least 2014. Initially focusing on public sector organizations in South Korea, Springtail gained notoriety after the South Korean government attributed an attack on Korea Hydro and Nuclear Power (KHNP) to them. The U.S. government has linked Springtail to North Korea’s military intelligence agency, the Reconnaissance General Bureau (RGB). Recently, the group has been involved in spear-phishing campaigns, exploiting vulnerabilities in VPNs and deploying malware through Trojanized software packages.
The newly identified Gomir backdoor appears to be a Linux variant of the previously known GoBear backdoor. Both backdoors share a significant amount of code, indicating a common origin. Gomir mimics much of GoBear’s functionality, albeit tailored for the Linux environment.
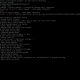
When executed, Gomir checks if it contains the string “install” in its command line arguments. If so, it attempts to install itself with persistence:
- Superuser Privileges: If running with superuser privileges, Gomir copies itself to
/var/log/syslogdand creates a systemd service named “syslogd” to ensure it starts on boot. - Non-Superuser Privileges: If not running with superuser privileges, Gomir configures a crontab entry to start on every reboot.
Once installed, Gomir establishes communication with its command-and-control (C&C) server, using HTTP POST requests to exfiltrate data and receive commands. It supports 17 different commands, closely mirroring those of the GoBear backdoor.
Springtail’s recent campaign, documented by South Korean security firm S2W, involved delivering a new malware family named Troll Stealer through Trojanized software packages. Troll Stealer, written in Go, shares much of its code with earlier Springtail malware and targets South Korean government personnel by stealing files, screenshots, browser data, and system information.
Springtail has shown a heavy focus on supply chain attacks, using Trojanized software installers and fake software packages to distribute their malware. This tactic was evident in their use of compromised software from SGA Solutions and Wizvera VeraPort. The compromised packages were hosted on third-party sites or masqueraded as official applications, maximizing the chances of infecting targeted South Korean entities.
Organizations, especially those in South Korea, should remain alert to these threats and ensure that their security protocols are up-to-date to defend against such sophisticated attacks. For more detailed information on the Gomir backdoor and its capabilities, refer to Symantec’s full report.