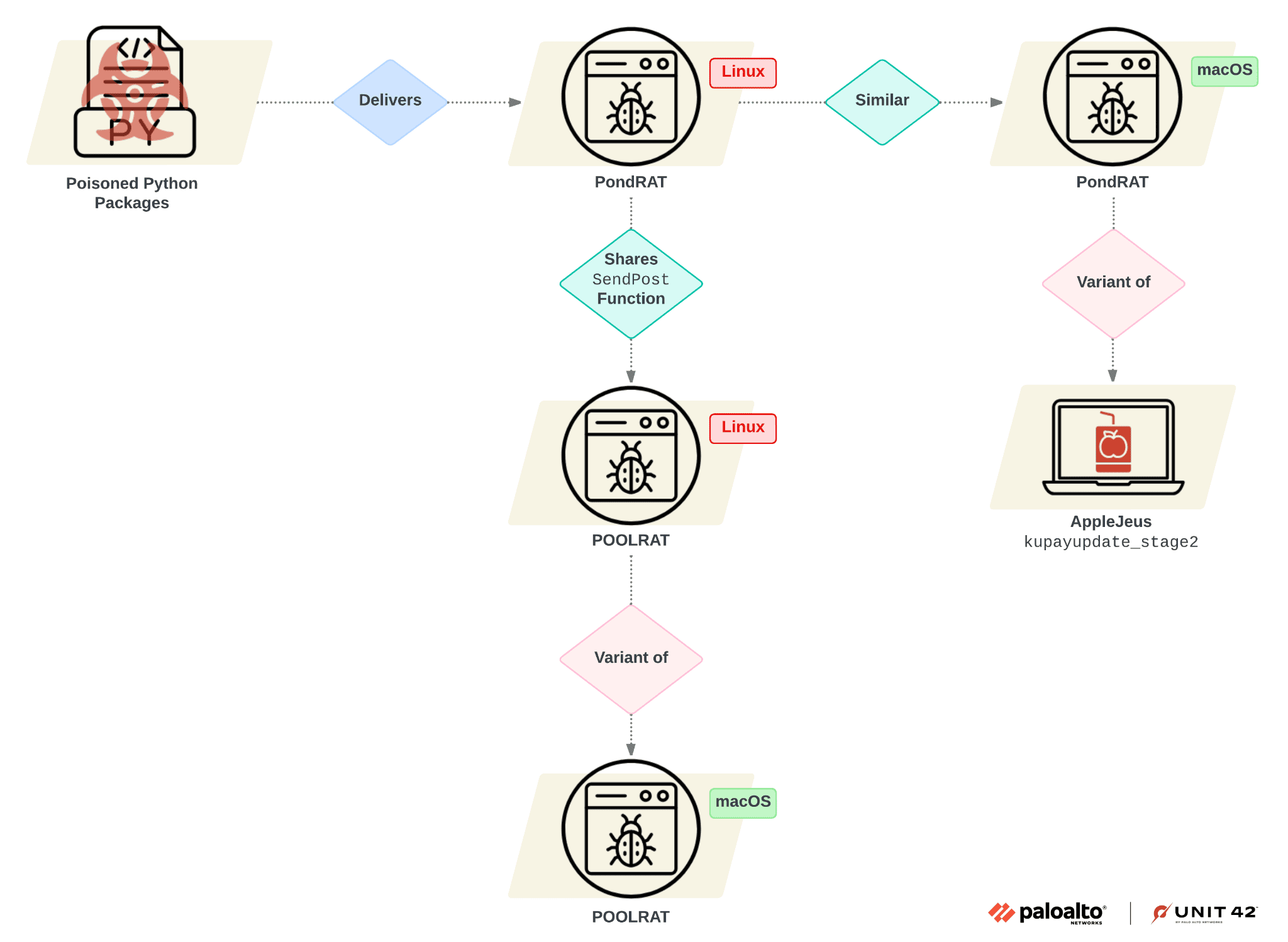
Similarities between the malware we found and other malware previously attributed to Gleaming Pisces | Image: Unit 42
Unit 42 researchers have uncovered a new cyberattack campaign by the North Korean-affiliated APT group, Gleaming Pisces, targeting Linux and macOS systems via poisoned Python packages. The campaign involves the distribution of malicious software packages through the PyPI repository, delivering a backdoor known as PondRAT. This backdoor is a lighter version of POOLRAT, a remote administration tool (RAT) previously linked to Gleaming Pisces.
The attack begins with malicious Python packages uploaded to PyPI, a popular repository for developers. Among the infected packages are “real-ids,” “coloredtxt,” “beautifultext,” and “minisound.” Once downloaded and installed, these packages initiate a chain of events leading to the deployment of PondRAT, a remote administration tool (RAT) designed to take control of the victim’s system.
The infected Python packages execute bash commands to download the RAT, which then grants the attacker full control, including the ability to upload and download files, run commands, and even pause system operations. What makes this attack especially dangerous is its cross-platform nature, with both Linux and macOS variants being deployed seamlessly.
PondRAT, which researchers have identified as a lightweight version of the POOLRAT backdoor previously linked to Gleaming Pisces, is designed to operate efficiently on compromised endpoints. Its functionality allows attackers to silently control infected systems, making it a versatile tool in the hands of cybercriminals. While lighter than POOLRAT, PondRAT still carries enough capability to disrupt networks and steal sensitive data.
Unit 42’s analysis found that the command structure of PondRAT mirrors that of POOLRAT, with only a few streamlined differences. Commands such as uploading and downloading files, executing remote commands, and checking the status of implants are all available to the attacker, ensuring they can maintain a foothold on the system for as long as necessary.
Gleaming Pisces, a North Korean threat actor known for its ties to the Reconnaissance General Bureau (RGB), has a long history of sophisticated attacks, particularly in the cryptocurrency sector. The group gained notoriety with its AppleJeus campaign, which distributed fake cryptocurrency trading software as a means to infiltrate networks. The recent campaign with poisoned Python packages demonstrates the group’s ability to adapt and expand its attack vectors.
Unit 42 researchers discovered code similarities between PondRAT and malware used in previous AppleJeus campaigns, reinforcing the connection to Gleaming Pisces. Identical function names, overlapping code structures, and shared encryption keys provide solid evidence that this campaign is part of the group’s ongoing efforts to infiltrate supply chains.
While PyPI has removed the malicious packages linked to this campaign, the threat of poisoned software packages remains an ongoing concern. To mitigate the risk, organizations must remain vigilant when incorporating third-party packages into their development environments. Security measures, such as regular code reviews, package verifications, and runtime monitoring, are essential in detecting and preventing such attacks.
Related Posts:
- Python Developers Targeted in Massive Supply Chain Attack; Over 170,000 Users Affected
- Malicious PyPI Packages Expose User Credentials
- Hackers make poisoned Final Cut Pro specifically to target Mac users