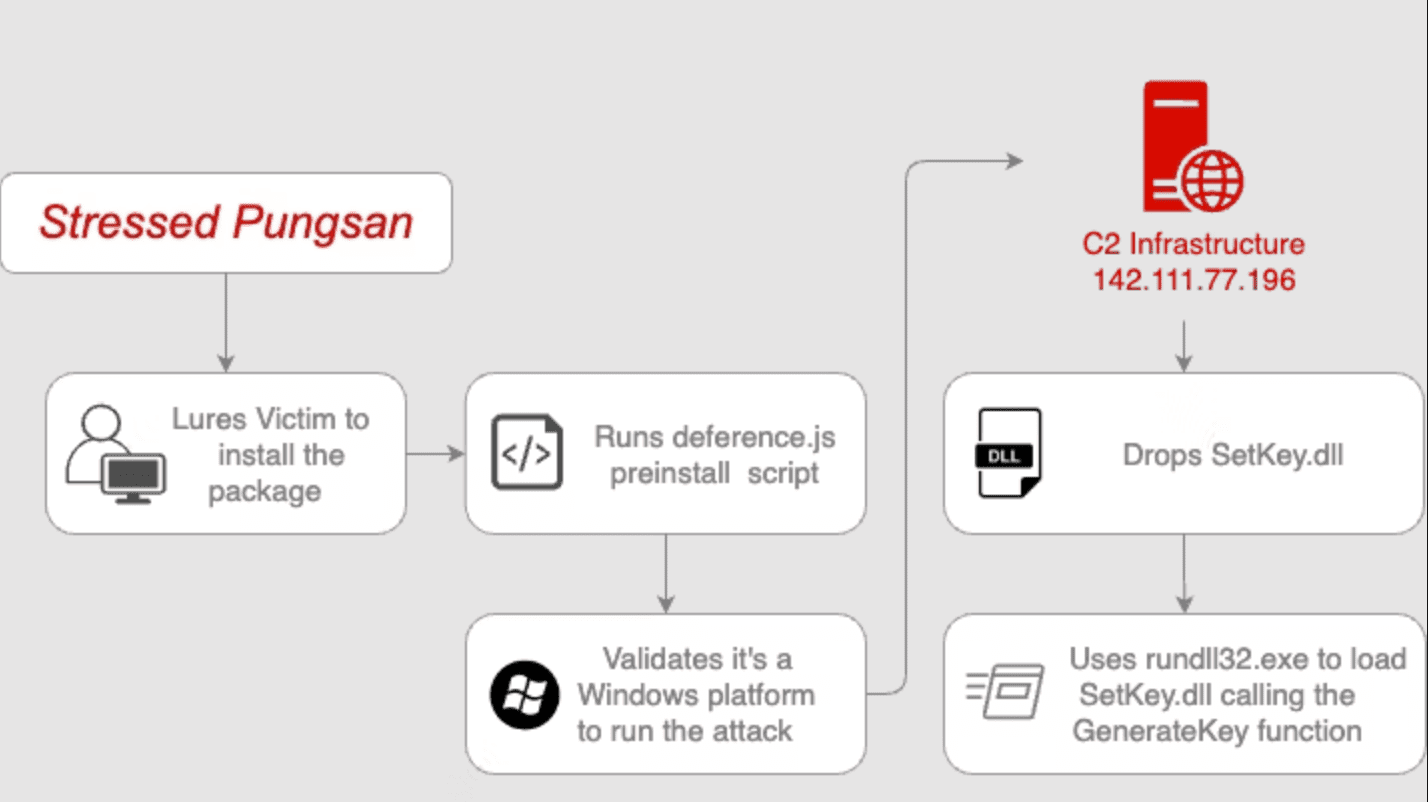
Attack Flow
On July 7th of this year, a user of the npm developer repository with the nickname “nagasiren978” published two malicious packages: “harthat-hash” and “harthat-api,” which contained code that installed additional malware from the attackers’ C2 server. The primary targets of these attacks were Windows-based systems.
The methods and infrastructure used in the malicious packages align with the tactics of a hacker group associated with North Korea, tracked by Microsoft under the name MOONSTONE SLEET. Within Datadog, the company that first identified these malevolent packages, this threat cluster is known as “Stressed Pungsan,” a name derived from a breed of dog raised in North Korea.
The hackers aimed to infiltrate software supply chains and development environments. Upon gaining the necessary access, the attackers stole personal information, API keys, and cloud service access credentials, while also moving laterally across other systems within the victim’s network.
In response to such threats, Datadog’s security team developed infrastructure to scan packages on PyPi and npm using the GuardDog software. During a scan on July 7th, specialists detected the two packages exhibiting suspicious behavior.
The “harthat-hash” version 1.3.3 and “harthat-api” version 1.3.1 packages employed pre-installed scripts to execute and subsequently delete “.js” format files. They contained links to suspicious domains and downloaded malicious DLL files, which were executed via “rundll32.exe.”
Both packages were nearly identical in content, differing only in the id parameter value in the C2 server links. The malicious code downloaded a file named “Temp.b,” renamed it to “package.db,” and executed it through “rundll32.exe.” After execution, the script was deleted, and the “package.json” file was replaced with “pk.json,” complicating the detection of malicious activity.
The DLL file downloaded by the malicious packages contained suspicious Windows API calls, such as “IsDebuggerPresent” and “GetTickCount,” used for anti-debugging and protection against reverse engineering. However, static analysis did not reveal explicit malicious logic, suggesting that the DLL file might not have been fully operational or was used for testing the C2 infrastructure.
The attackers utilized code from the popular “node-config” repository, adding some malicious modifications. Notably, the packages were removed from npm very quickly, not by moderators, but by the authors themselves.
Software developers are advised to check if the “harthat-api” or “harthat-hash” packages are installed in their infrastructure. If detected, immediate measures should be taken to rotate credentials, isolate the application, and investigate potential threat propagation.
The threat from malicious npm packages is becoming increasingly pertinent. Attackers disguise them as legitimate packages to inject malicious code. Rapid response to such incidents can help prevent severe consequences for data security and infrastructure.
Related Posts:
- Major npm flaw crashes Linux Systems, force users to reinstall
- npm’s Hidden Threat: The Covert Trojan Lurking in Your Windows System
- Cybersecurity in Focus: ECB Stress Test Exposes Banks’ Vulnerabilities