Image: Cisco Talos
In a recent disclosure, cybersecurity researchers at Cisco Talos have uncovered a newly developed Remote Access Trojan (RAT) named “MoonPeak,” attributed to a North Korean nexus cluster identified as “UAT-5394.” This advanced malware, rooted in the XenoRAT family, represents a significant evolution in the tactics, techniques, and procedures (TTPs) employed by the threat actor, revealing intricate connections within their infrastructure.
MoonPeak, which has evolved from the open-source XenoRAT, showcases continuous development and sophistication, marking a departure from its predecessors. The malware’s evolution is indicative of the strategic shifts within UAT-5394, raising questions about the group’s affiliation with the notorious North Korean state-sponsored group, Kimsuky. While overlaps in TTPs and infrastructure patterns suggest a possible connection, Cisco Talos remains cautious, treating UAT-5394 as a distinct entity until further intelligence can conclusively link them.
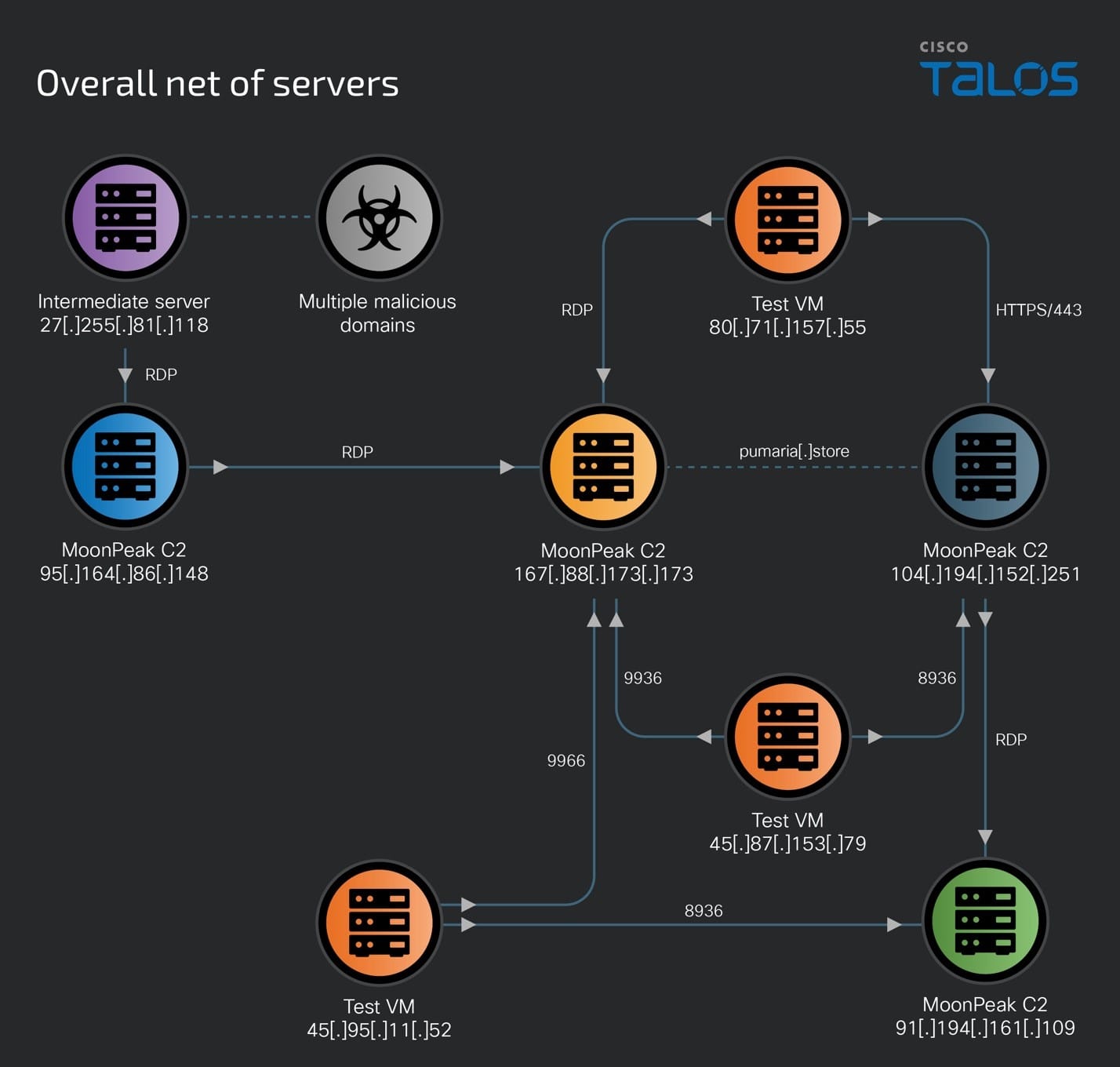
Cisco Talos’ investigation has meticulously mapped the infrastructure underpinning this campaign, uncovering a network of servers and payload-hosting sites intricately woven together. The transition from cloud services to attacker-owned infrastructure, particularly after AhnLab’s recent disclosures, marks a pivotal shift in UAT-5394’s strategy. The group now relies on a robust network of remote access and command-and-control (C2) servers, including a key server at 95.164.86.148, which has been central to their operations since June 2024.
The complexity of UAT-5394’s infrastructure is exemplified by the dynamic nature of its servers. For instance, 167.88.173.173, a high-flux server, has undergone multiple transformations, both in operating systems and web server configurations, within just two months. This server played a critical role in compiling and deploying MoonPeak malware variants, with connections to other servers such as 104.194.152.251, further extending the threat actor’s operational reach.
Analysis of MoonPeak samples reveals a deliberate effort to enhance obfuscation and thwart detection. Changes in namespace identifiers and the forced use of compression before encryption are among the tactics used to evade analysis. Additionally, the adoption of State Machines in MoonPeak’s code adds another layer of complexity, making reverse engineering significantly more challenging.
The discovery of MoonPeak and the associated infrastructure offers valuable insights into the tactics and capabilities of North Korean cyber actors. While attribution to Kimsuky remains inconclusive, the sophistication and evolving nature of this campaign underscores the critical importance of maintaining a proactive and multi-layered defense strategy in today’s complex cybersecurity landscape.
Related Posts:
- Kimsuky APT: New TTPs Revealed in Rapid7 Cybersecurity Report
- North Korean APT Group Kimsuky Targets Japanese Organizations with Stealthy Malware Campaign
- Kaspersky Lab Exposes TTPs of Asian Cyber Espionage Groups
- QiAnXin Uncovers New Kimsuky Malware Campaign
- North Korean Hackers Exploit Old Office Flaw to Deploy Keylogger