According to Techspot, Play Store had no stranger to applications that appeared to be legitimate but contained malicious software. However, McAfee researchers found something different from the past: three malicious applications targeting specific individuals. program. The security organization said that a group related to North Korea has uploaded these applications, which are designed to penetrate Android devices that are part of North Koreans.

Image: McAfee
Although North Korean hackers usually refer to the infamous Lazarus Group, the attacker is Sun Team. The organization participated in an event called RedDawn, which attempted to attract fertilizers to download software before the malware-laden application was added to the Google Play store.
From January to March this year, these three apps appeared on Google Play Store. One of the applications, Food Ingredients Info, provides information on food ingredients. The other two applications, Fast AppLock and Fast AppLockFree, are security tools. All three applications can steal the personal data of users who download the application. The data may be used to extort, threaten or track victims. The information includes the user’s photos, contacts, call logs, and text messages.
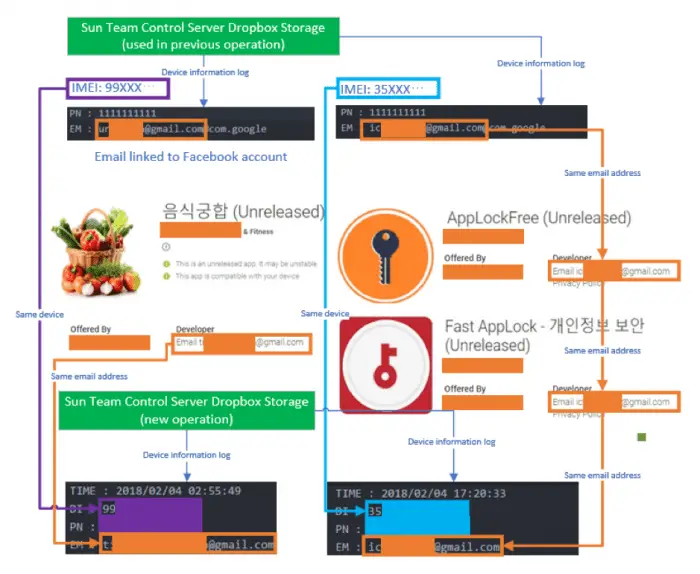 Image: McAfee
Image: McAfee
“After infecting a device, the malware uses Dropbox and Yandex to upload data and issue commands, including additional plug-in dex files; this is a similar tactic to earlier Sun Team attacks,” wrote Jaewon Min of McAfee. “From these cloud storage sites, we found information logs from the same test Android devices that Sun Team used for the malware campaign we reported in January. The logs had a similar format and used the same abbreviations for fields as in other Sun Team logs. Furthermore, the email addresses of the new malware’s developer are identical to the earlier email addresses associated with the Sun Team“
The Sun Team attempted to allow North Korean defectors (more than 30,000 of them in 2016) to download applications by using fake Facebook profiles or sending direct personal messages through the site. The popular chat application KakaoTalk in Korea is also used to send links to the target.
Apps that have been deleted so far have been downloaded about 100 times in Google Play Store. According to reports, the two fake Facebook profiles set by Sun Team are still active. Further evidence linking the attack with North Korea includes the IP address belonging to the country found in the test log file.
Source: TechSpot