NtHiM – Super Fast Sub-domain Takeover Detection
Changelog v0.1.4
- Updated the dependencies to the latest version, without breaking the functionalities | here,
- Added panicking for problem while opening the file containing list of hostnames | here,
- Properly handled the Threads argument parsing workflow | here,
- Added an argument for Timeout during connections | here, and also implemented the functionality for Timeout, as requested in #12 | here,
- Implemented a fix (set up a pre-parser for hostnames) for the issue #18 | here,
- Started using v3.0.10 of clap, plus replaced the “about” method with the “help” method for arguments, (optional fix to #19) | here,
- Refactored the implementation of Single and Multiple Hostnames arguments | here,
- Implemented a new strategy to handle signatures, leading to huge performance boost (Complete Resolution to the issue #12) | here,
- Implemented further URL parsing for preventing error types like “RelativeUrlWithoutBase” (extra fix to #18) | here,
- Implemented Error Handling for hostnames with non-UTF-8 characters | here!
Installation
Method 1: Using Pre-compiled Binaries
The pre-compiled binaries for different systems are available on the Releases page. You can download the one suitable for your system, unzip the file and start using NtHiM.
Method 2: Using Crates.io
NtHiM is available on Crates.io. So, if you have Rust installed on your system, you can simply install NtHiM with the following command:
cargo install NtHiM
Method 3: Manual Build
You will need Cargo to perform the manual build for NtHiM. If you have Cargo installed, you can simply follow the steps below:
- Clone this repository, git clone https://github.com/TheBinitGhimire/NtHiM;
- Go inside the folder, cd NtHiM;
- Use the cargo build command,
- Go inside the newly-created target folder, and open the debug folder inside it, cd target/debug;
- You will find NtHiM.exe (on Microsoft Windows) or NtHiM binary (on Linux).
The installation walkthrough for NtHiM has been uploaded to YouTube, covering all of these three methods, and you can watch the video here.
Use
| Flag | Description | Example |
|---|---|---|
| -h | Display help related to usage! | NtHiM -h |
| -t | Scan a single target! | NtHiM -t https://example.example.com |
| -f | Scan a list of targets from a file! | NtHiM -f hostnames.txt |
| -c | Number of Concurrent Threads! | NtHiM -c 100 -f hostnames.txt |
| -V | Display the version information! | NtHiM -V |
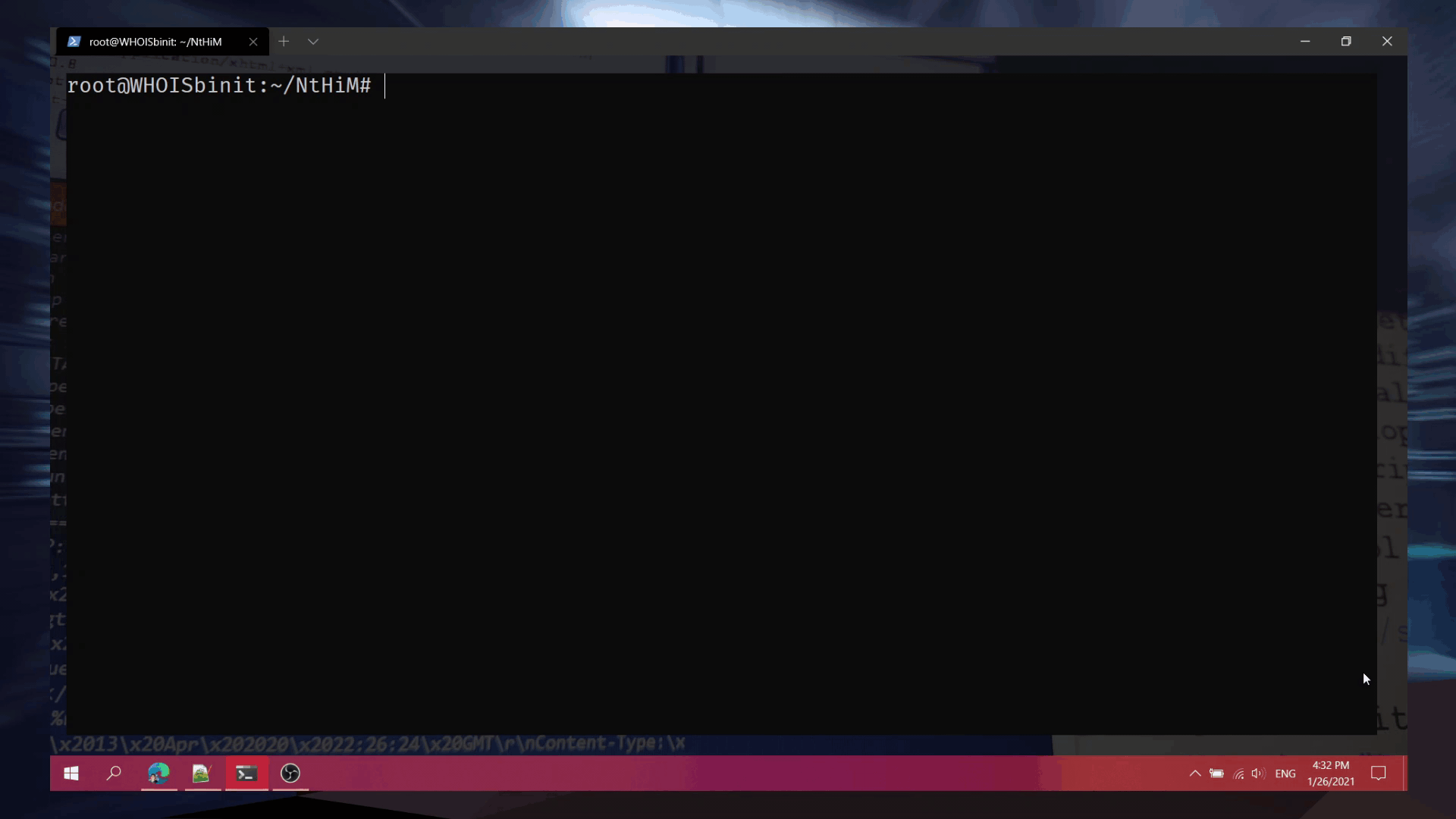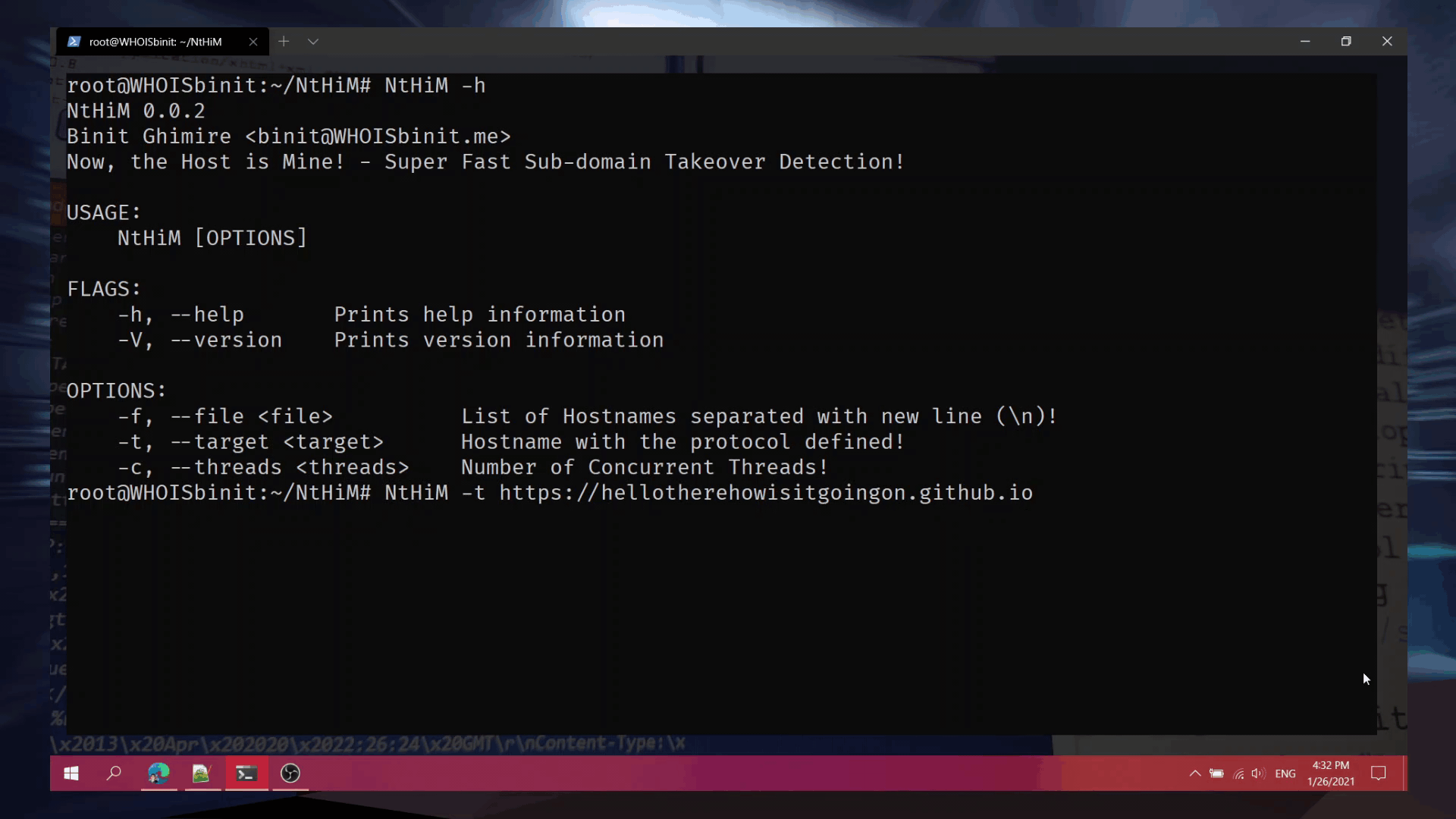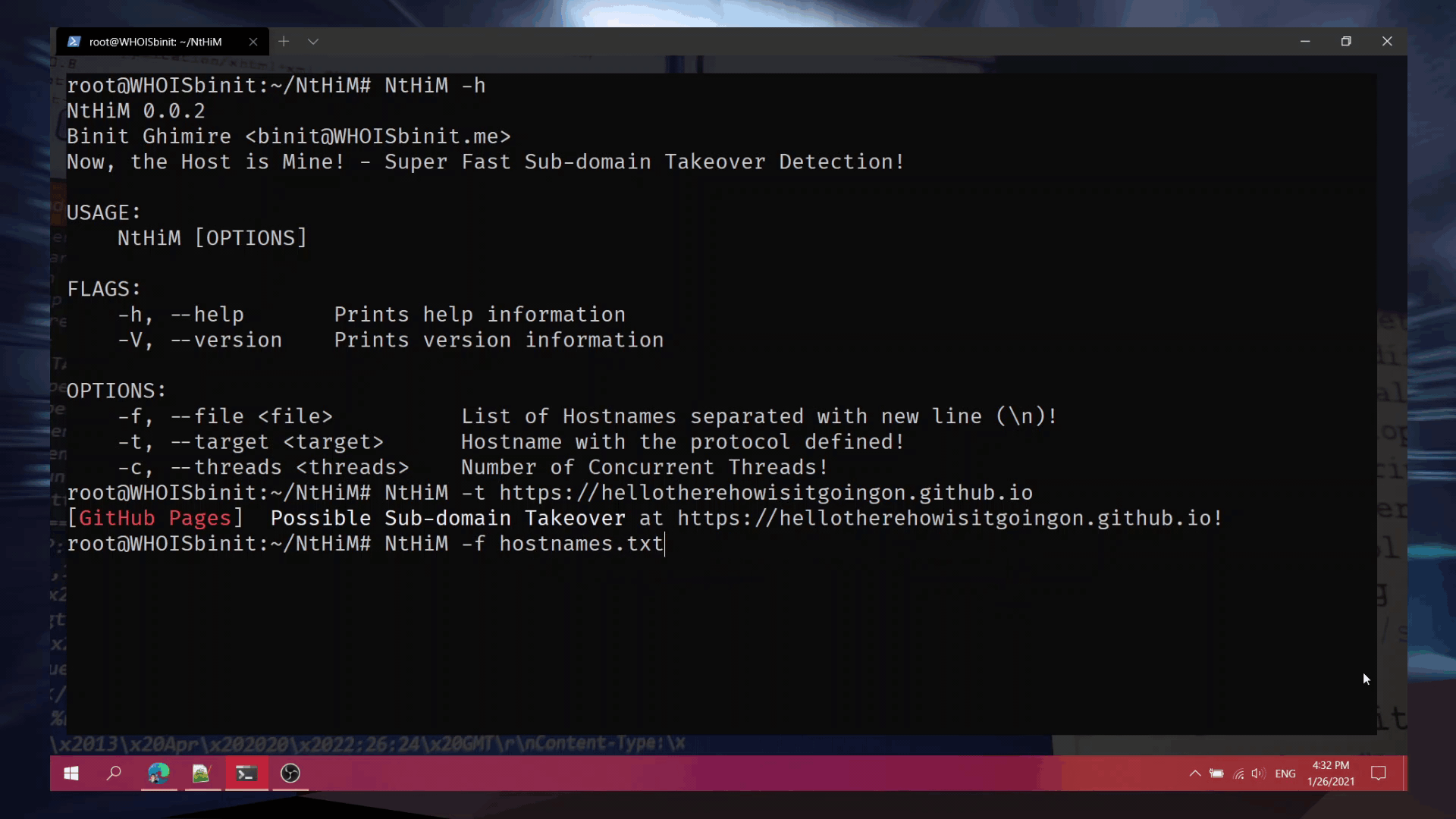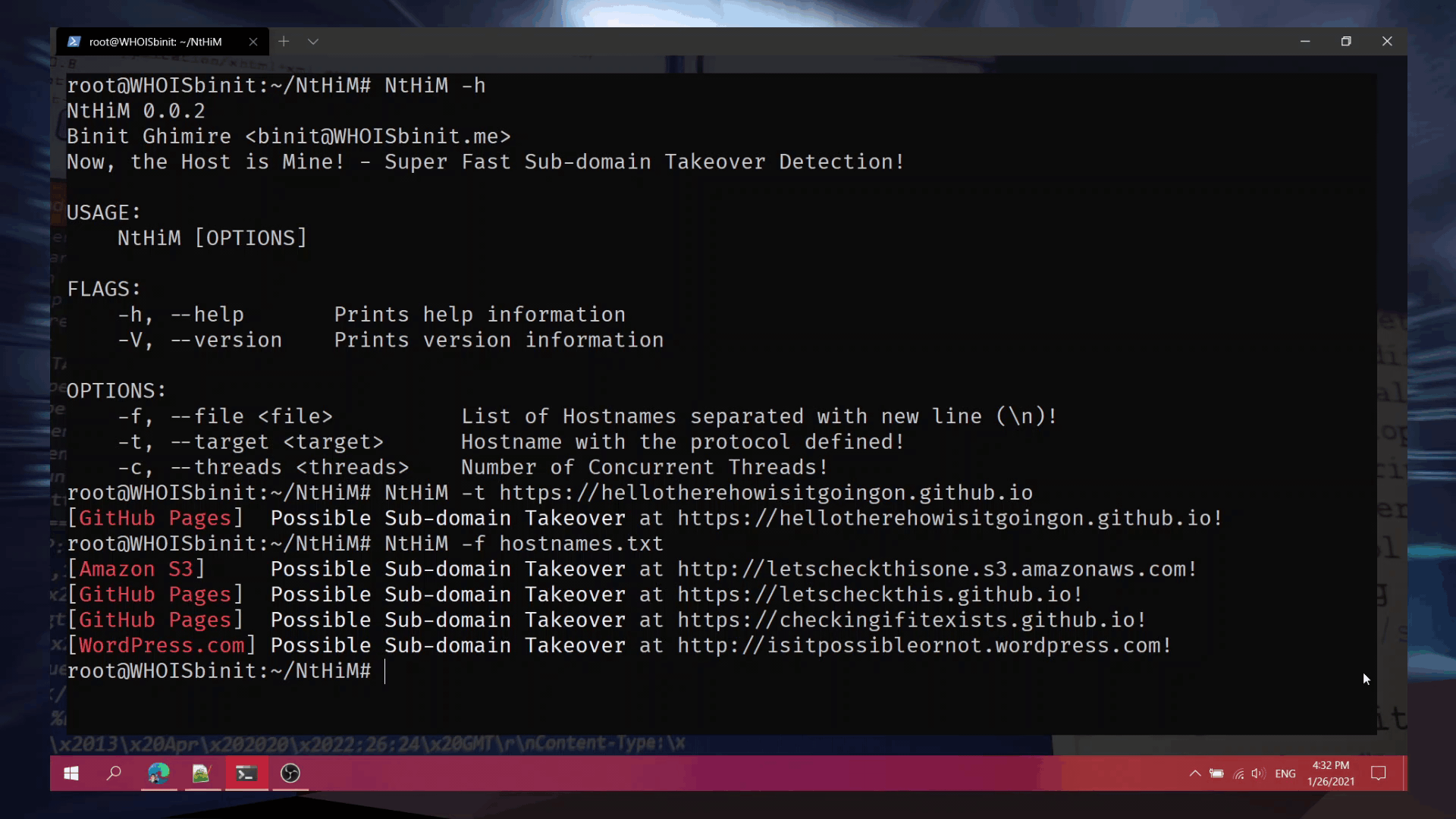
Use Case 1 (Single Target):
NtHiM -t https://example.example.com
Use Case 2 (Multiple Targets):
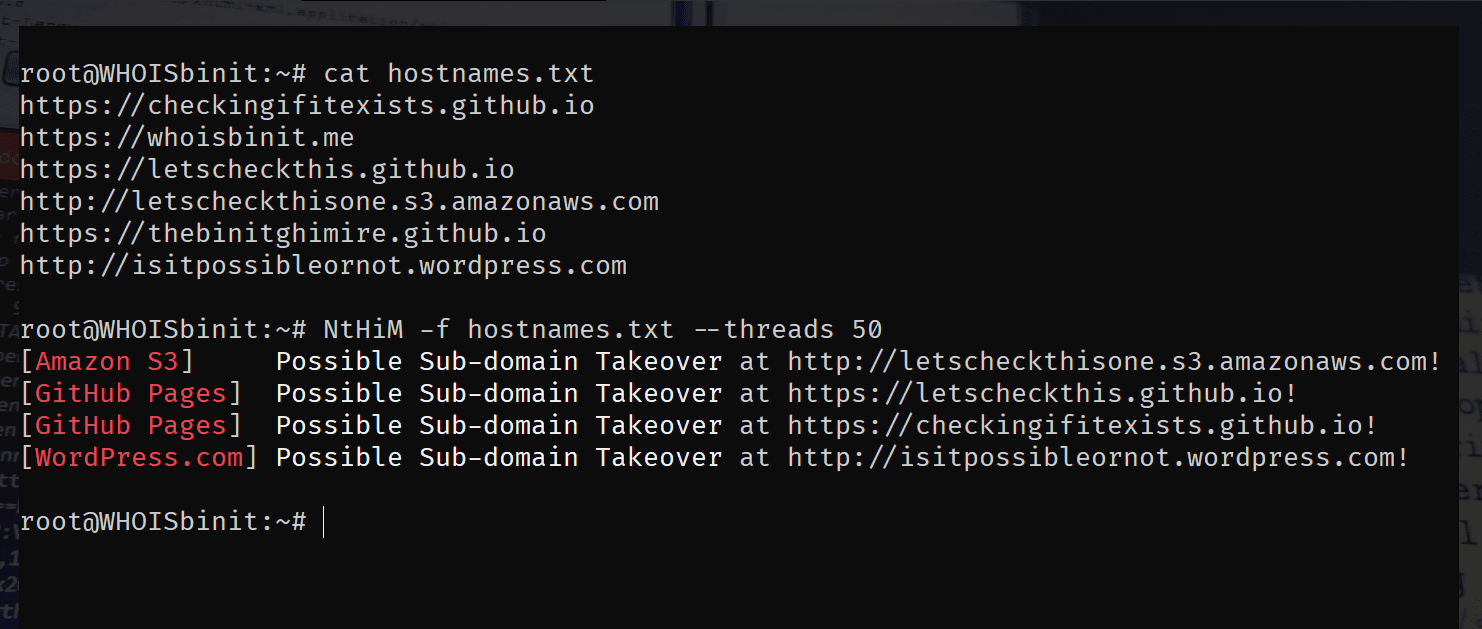
NtHiM -f hostnames.txt
Usage Demonstration:
 Examples
Examples
Single Target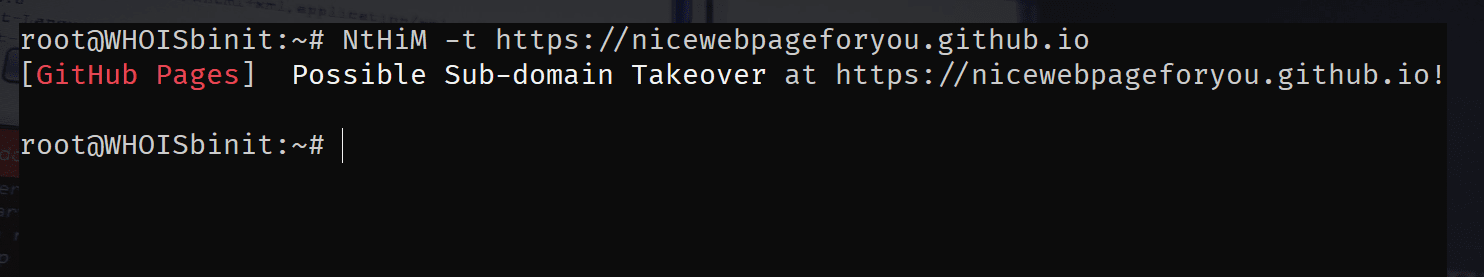
Multiple Targets using Concurrent Threads
Workflow
Platform Identification
NtHiM uses the data provided in EdOverflow/can-i-take-over-xyz for the platform identification.
Copyright (c) 2021 Binit Ghimire
Source: https://github.com/TheBinitGhimire/