of-CORS: identifying and exploiting CORS misconfigurations
of-CORS
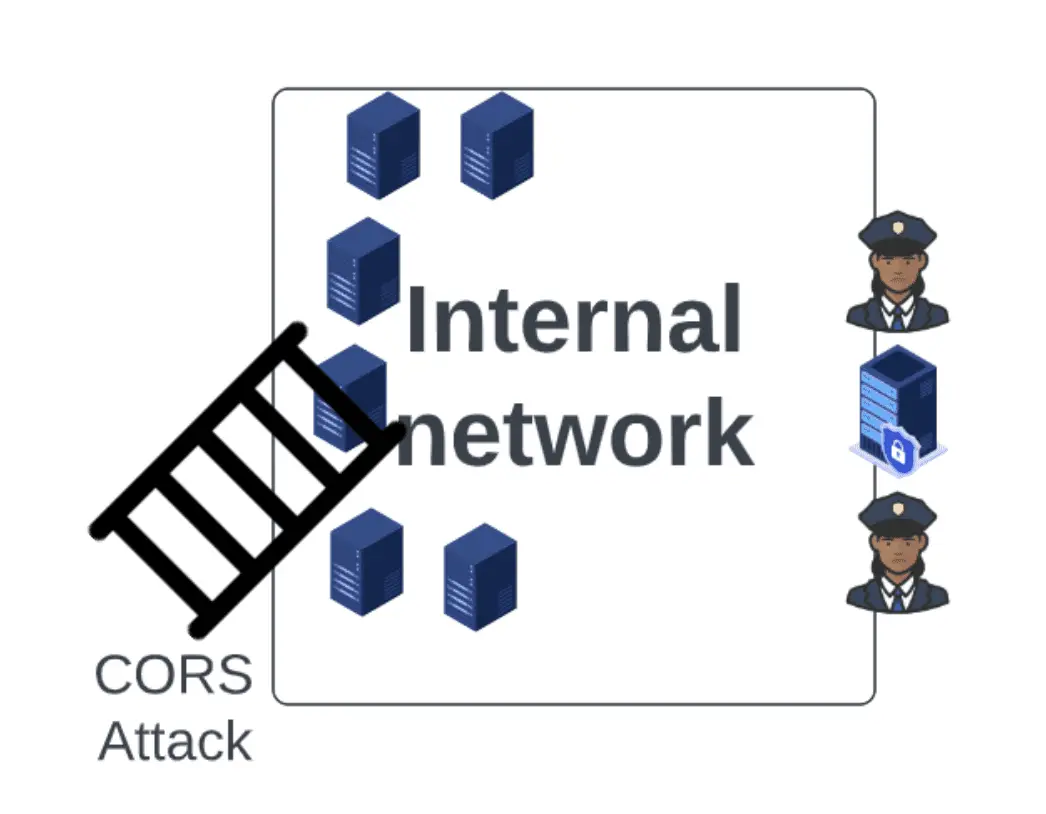
of-CORS is Truffle Security’s tool suite for identifying and exploiting CORS misconfigurations on the internal networks of bug bounty targets using typosquatting.
How Does it Work??

of-CORS is a Python3 web application built on top of Django and Django Rest Framework. Once set up and configured of-CORS will automatically register browser service workers in the browsers of any victims that visit the application. These service workers send HTTP requests to a list of pre-configured internal domains with the intention of discovering CORS misconfigurations on internal networks. The results of these requests (whether successful or otherwise) are then submitted via API back to the of-CORS instance.
Once a service worker has been registered in a victim’s browser, a JavaScript payload redirects the browser away to the page that of-CORS believes they were originally trying to access.
The collected results can subsequently be viewed in a minimalist dashboard available on the of-CORS application.
of-CORS would do all the following:
- Enumerate likely internal subdomains for target organizations
- Launch a JavaScript payload to prod for CORS misconfigurations against configured domains
- Utilize a service worker to make requests long after the victim is redirected off the typosquatting domain
- Accept results from the victim’s browser and provide some level of result queryability in a UI
- Make some level of attempt to hide itself
- Is likely to be visited by employees of target organizations





