
Web-link accessed right away after opening the maldoc
In the fast-paced world of cybersecurity, where new threats emerge daily, it’s all too easy to forget about the dangers lurking in the shadows of the past. However, a recent investigation by Check Point serves as a stark reminder that old vulnerabilities never truly disappear; they simply evolve. This research sheds light on the persistent exploitation of three aged CVEs in Microsoft Word and Excel, illustrating how cyber threats tend to resurface across generations.
Despite these vulnerabilities—CVE-2017-11882, CVE-2017-0199, and CVE-2018-0802—not being zero-day exploits, they continue to be effectively employed in cyberattacks, demonstrating their enduring relevance in cybercriminals’ arsenal.
The landscape of cybersecurity is ever-changing, but some threats withstand the test of time. More than 13,000 samples utilizing these old CVEs were detected in the wild in 2023, showcasing their persistent presence in the cybersecurity ecosystem. These samples employ various formats and tactics, including DOC(X), XLS(X), and RTF files, all with the singular aim of enticing victims to click and propagate malware.

Throughout their history, these vulnerabilities have been exploited to disseminate a plethora of notorious malware families. From the infamous Dridex in 2017 to the more recent Guloader in 2021, these CVEs have significantly impacted the spread of malware. In 2023, additions to the roster included samples used by threat actors such as Gamaredon APT, Agent Tesla, and Formbook/Xloader, underscoring the versatility and enduring appeal of these vulnerabilities to cyber criminals.
Despite being well-documented for several years, MalDocs leveraging old CVEs often evade detection due to their sophisticated evasion techniques. These techniques include encryption, obfuscated URLs, and shellcode obfuscation, making them particularly elusive for automated security systems to identify and neutralize.
The industries targeted by these MalDocs are chosen strategically, focusing on sectors where the potential for data exploitation and financial gain is significant. Finance/banking, governmental agencies, and healthcare organizations are prime targets due to the sensitive nature of the data they handle. Payloads delivered by these MalDocs are tailored to specific objectives, whether financial gain, data theft, or service disruption.
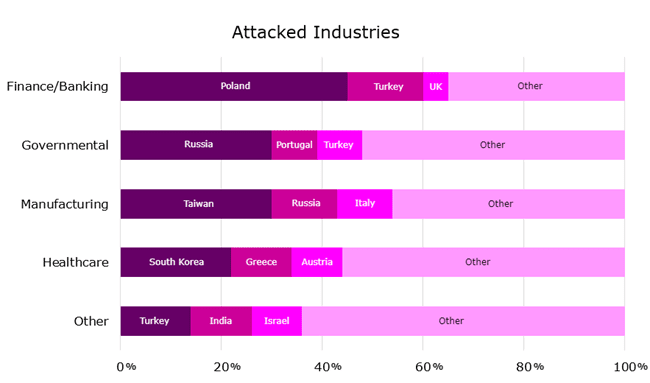
While specific details on affected countries may be limited, it’s evident that countries with significant economic or geopolitical importance are prime targets. This underscores the global reach and impact of cyber threats exploiting old vulnerabilities.
Despite their age, these CVEs have evolved to bypass modern security defenses, employing techniques such as code obfuscation, legitimate-looking URLs, and timing-based execution to evade detection. The evolving tactics of cybercriminals highlight the need for a multi-faceted approach to cybersecurity, combining advanced detection technologies with heightened user awareness.
In conclusion, the persistence of old vulnerabilities underscores the importance of ongoing vigilance in cybersecurity. To mitigate these risks, it’s crucial to keep operating systems and applications updated, exercise caution with email attachments and links, enhance cybersecurity awareness among employees, and seek guidance from security specialists when in doubt.