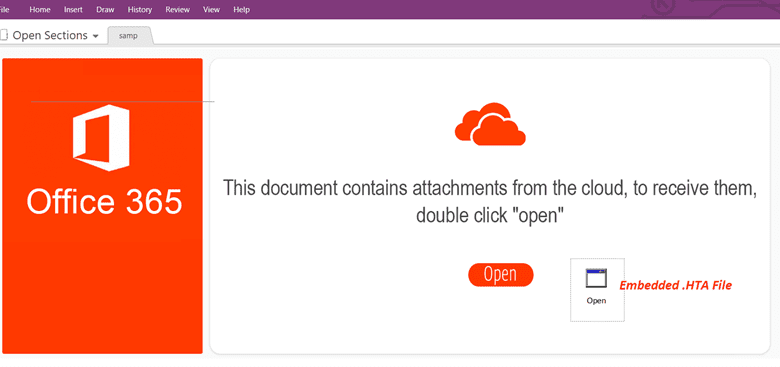
OneNote Template. Source: mcafee
Recently, McAfee Labs uncovered a series of malware campaigns leveraging the popular note-taking application, Microsoft OneNote, to deliver and execute various strains of malicious software.
With Microsoft’s policy change disabling Office macros by default, malicious actors have shifted their focus to alternate delivery methods, such as LNK files. OneNote documents have emerged as a viable alternative, thanks to their file attachment capabilities. Recent campaigns have deployed an array of malware families through OneNote, including IceID, Qakbot, RedLine, AsyncRat, Remcos, AgentTesla, QuasarRAT, XWORM, Netwire, Formbook, and Doubleback.

Phishing emails serve as the primary delivery method for these malicious OneNote documents, often disguised as invoices or legal notices to entice victims into opening them. Once opened, the documents contain either Windows batch scripts or Visual Basic scripts that invoke PowerShell to drop the malware payload onto the target system.
Two distinct Qakbot campaigns have been identified, each utilizing OneNote documents to deliver and execute the malware. In the first campaign, the malware author used phishing emails to deliver the malicious OneNote document, either as an attachment or via a URL link. The document contained an HTA file that, when executed, leveraged the curl utility to download and execute the Qakbot payload.
In the second campaign, the OneNote document featured an embedded batch file that, when executed, used PowerShell to fetch the Qakbot payload from the internet and execute it on the target system. This section delves into the technical details of the dropper scripts used to deploy Qakbot.
The recent emergence of OneNote-based malware campaigns is a stark reminder of the relentless creativity and determination of cybercriminals. It is crucial for individuals and organizations to remain vigilant and proactive in the face of such threats, continuously updating their cybersecurity strategies to stay one step ahead of the game.