Image: Aquasec
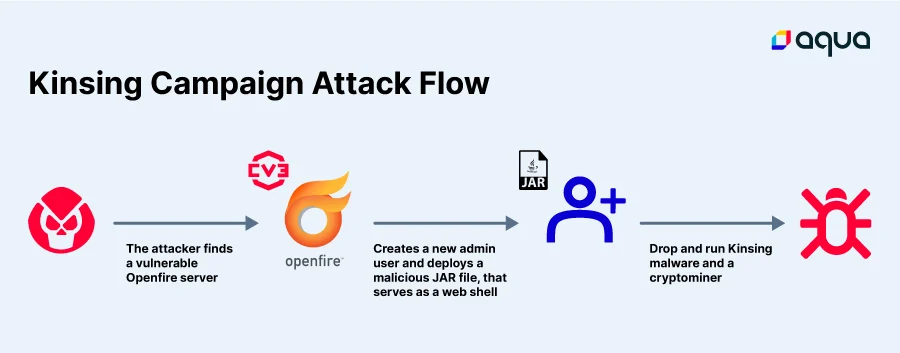
A recent discovery by Aqua Nautilus has unveiled a new campaign targeting the Openfire vulnerability (CVE-2023-32315). Revealed in May this year, this flaw is exploited to release the Kinsing malware and a cryptominer, posing significant risks for users.
Openfire, a real-time collaboration (RTC) server, serves as a communication platform using the XMPP protocol. It facilitates secure and segmented instant messaging for large enterprises, capable of supporting more than 50,000 concurrent users. However, the recent vulnerability found in its console could compromise its security credentials.

This flaw pertains to path traversal within the Openfire setup environment. Once exploited, unauthorized users can access restricted admin setup files in the Openfire Admin Console. The aftermath? Threat actors potentially adding new admin users or uploading malicious plugins, which could grant them full control of the affected server.
Exploiting the above vulnerability, the Kinsing campaign drops the Kinsing malware and a cryptominer in real time, aiming for stealth and persistence. Once the threat actor identifies an Openfire server, they test for its vulnerability to CVE-2023-32315.
With this flaw, threat actors can create new admin users and upload malicious plugins, specifically the cmd.jsp plugin in this campaign, setting the stage for the Kinsing malware’s deployment.
The entire process involves:
- Sending user creation commands.
- Authenticating in the Openfire Administration Panel with the newly created admin user, thereby acquiring full system control.
- Uploading a malicious plugin facilitating web shell commands. This plugin, flagged as malicious in VirusTotal, enables file downloads and command execution on the server.
- Broad communication between the malware and its C2 server.
- Downloading a secondary payload via a new shell script, ensuring persistent malware presence on the server.
Given Openfire’s widespread use, Aqua Nautilus probed the extent of potential exposure. An inquiry into Shodan revealed 6,419 globally connected servers with Openfire service. Surprisingly, 19.5% of the reachable servers (984 out of 5,036) were susceptible to this vulnerability. The majority of these servers were predominantly located in the USA, China, and Brazil.
Aqua Nautilus’s Openfire honeypot observed over 1,000 attacks in less than two months, with 91% attributed to the Kinsing campaign. These attacks can be categorized into two types. The first deploys a web shell, allowing the attacker to introduce Kinsing malware and cryptominers. The second uses a similar exploit without progressing the attack after collecting system information.
In summary, this discovery by Aqua Nautilus underscores the persistent threat of vulnerabilities even in reputed software. Regular patching, staying updated, and monitoring for irregularities remain crucial for cybersecurity.