OSXAuditor: free Mac OS X computer forensics tool
OS X Auditor
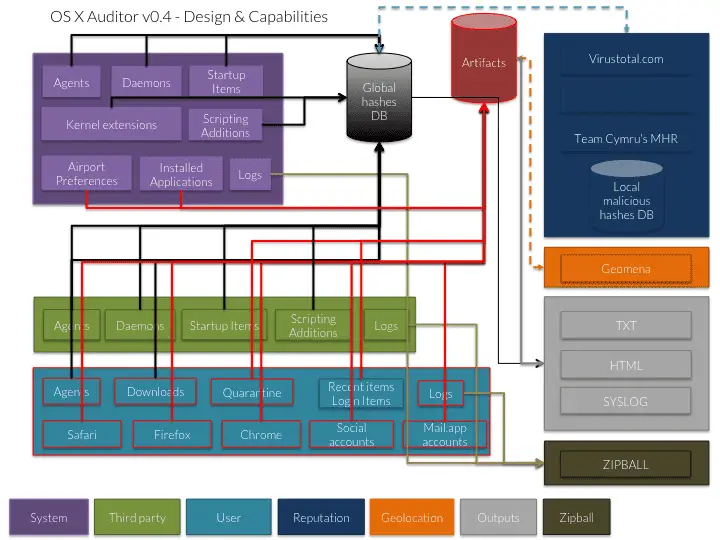
OS X Auditor is a free Mac OS X computer forensics tool.
OS X Auditor parses and hashes the following artifacts on the running system or a copy of a system you want to analyze:
- the kernel extensions
- the system agents and daemons
- the third party’s agents and daemons
- the old and deprecated system and third party’s startup items
- the users’ agents
- the users’ downloaded files
- the installed applications
It extracts:
- the users’ quarantined files
- the users’ Safari history, downloads, topsites, LastSession, HTML5 databases and localstore
- the users’ Firefox cookies, downloads, formhistory, permissions, places and signons
- the users’ Chrome history and archives history, cookies, login data, top sites, web data, HTML5 databases and local storage
- the users’ social and email accounts
- the WiFi access points the audited system has been connected to (and tries to geolocate them)
It also looks for suspicious keywords in the .plist themselves.
It can verify the reputation of each file on:
- Team Cymru’s MHR
- VirusTotal
- your own local database
It can aggregate all logs from the following directories into a zipball:
- /var/log (-> /private/var/log)
- /Library/logs
- the user’s ~/Library/logs
Finally, the results can be:
- rendered as a simple txt log file (so you can cat-pipe-grep in them… or just grep)
- rendered as a HTML log file
- sent to a Syslog server
Installation
pip install pyobjc biplist plist
git clone https://github.com/jipegit/OSXAuditor.git
Usage
- OS X Auditor runs well with python >= 2.7.2 (2.7.9 is OK). It does not run with a different version of python yet (due to the plist nightmare)
- OS X Auditor is maintained to work on the lastest OS X version. It will do its best on older OS X versions.
- You must run it as root (or via sudo) if you want to use is on a running system, otherwise it won’t be able to access some system and other users’ files
- If you’re using API keys from environment variables (see below), you need to use the
sudo -Eto use the users environment variables
Type osxauditor.py -h to get all the available options, then run it with the selected options
eg. [sudo -E] python osxauditor.py -a -m -l localhashes.db -H log.html
Setting Environment Variables
export VT_API_KEY=aaaabbbbccccddddeeee
OS X Auditor Copyright (C) 2013 Jean-Philippe Teissier
Source: https://github.com/jipegit/