Over 1,000 Lexmark printers worldwide are exposed online
Security researchers at NewSky Security have again brought us bad news about IoT security once again and they found that over 1,000 Lexmark printers were exposed online because of misconfiguration and that anyone with Internet access could Easily access them.
The number of vulnerable printers determined by the researchers was 1123, none of which was password-protected. This means that as long as potential attackers find these printers, they can perform many different types of activities. For example, adding a backdoor, hijacking a print job, taking a printer offline, or even sending lots of job instructions to print junk content can cause physical damage to the printer.
These printers come from many countries around the world, involving businesses, universities, and even some national government offices. Researchers at NewSky Security, using the Shodan engine to search, found an online printer that appeared to belong to the city office in Lafayette, USA.
Researchers used a custom shodan dorks to get a list of networked Lexmark printers. Shodan Engine lists 1475 unique IP addresses, which means 1475 printers were found.
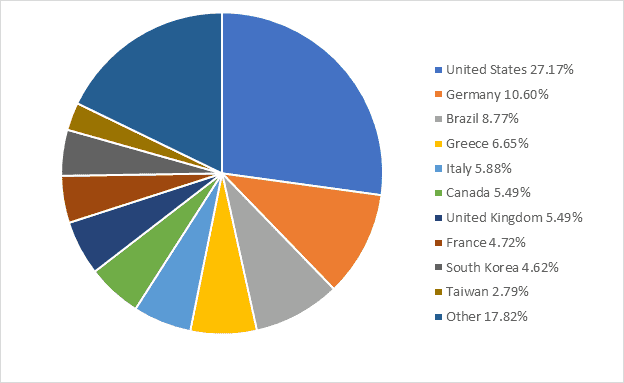
The researchers confirmed that only 352 (about 24%) will redirect visitors to the login page, which means they are password protected. The remaining 1123 units have no password at all, and most of them come from the United States. The following is a national and regional distribution of Lexmark printers without a password:
The researchers noted that for Lexmark printers, it allows users to remotely access the administration panel over TCP ports 80 and 443. But because Lexmark does not force the user to set a password, it creates a very dangerous situation. Once potential attackers have access to these printers, they have full access to the Lexmark printer.
The authorities also warned: “These printers also have several ports open, including TCP port 21 (FTP) and TCP port 23 (Telnet), which creates additional opportunities for potential attackers to launch attacks.”
According to the researchers, this access to network printers allows remote attackers to view the status of the device, printer model, serial number and MAC address, firmware version, and amount of ink. In addition, it allows you to enable the agent’s network configuration, change administrator passwords, change volume, contact information, device status, time and date, create self-signed certificates and private keys, and even upload files and send jobs to the printer.
NewSky Security has now notified Lexmark of this discovery and is working with Lexmark to issue security warnings to the affected organizations, including the Lafayette County Office.
Reference: threatpost





