
Industrial environments are increasingly relying on wireless technologies to power critical operations. However, a recent report from Nozomi Networks Labs reveals that this technological shift is exposing industrial networks to significant cybersecurity risks. The team identified 20 vulnerabilities in the firmware of Advantech EKI-6333AC-2G wireless access points, a popular choice for challenging industrial environments such as automobile manufacturing and logistics operations.
Nozomi Networks Labs focused on firmware version 1.6.2 of the EKI-6333AC-2G, a device designed for robust and stable dual-band Wi-Fi connectivity in mission-critical applications. The vulnerabilities discovered are not just theoretical risks—they enable unauthenticated attackers to remotely execute code with root privileges. This effectively compromises the confidentiality, integrity, and availability of the devices.
Among the most critical vulnerabilities are:
- CVE-2024-50370 through CVE-2024-50375 (CVSS 9.8): Improper neutralization of operating system commands, enabling attackers to inject malicious payloads.
- CVE-2024-50376 (CVSS 7.3): A cross-site scripting (XSS) vulnerability that can be exploited remotely.
- CVE-2024-50359 (CVSS 7.2): A command injection vulnerability requiring authentication, which can be chained with CVE-2024-50376 for devastating effects.
One highlighted attack vector leverages over-the-air proximity exploits. An attacker can use a rogue wireless access point to broadcast malicious beacon frames to the EKI device. These frames exploit CVE-2024-50376 by injecting malicious JavaScript into the device’s management interface. The attack can escalate by chaining CVE-2024-50359, allowing the attacker to execute arbitrary commands with root privileges.
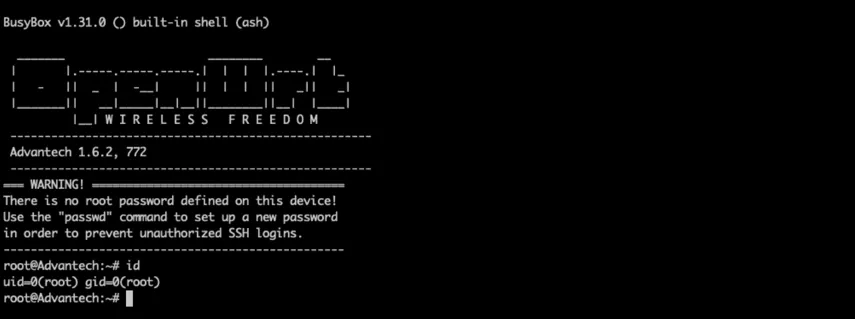
The implications of such attacks are severe:
- Persistent Access: Attackers can implant backdoors for ongoing control.
- Denial of Service (DoS): Disruption of critical automation processes, such as those involving rail-guided vehicles (RGVs) in manufacturing plants.
- Lateral Movement: Using compromised devices as gateways to infiltrate deeper into corporate networks.
Advantech acted swiftly, releasing updated firmware to address these vulnerabilities:
- EKI-6333AC-2G and EKI-6333AC-2GD: Firmware v1.6.5
- EKI-6333AC-1GPO: Firmware v1.2.2
Industrial operators are urged to upgrade immediately to these versions to mitigate the risks. “We encourage all asset owners to upgrade to this latest version to protect their network and devices from unauthorized access,” the report advises.
Related Posts:
- Kaspersky Report: Energy Industry becomes the largest area affected by vulnerabilities in industrial automation systems
- Positive Technologies: “73 percent of industrial organizations’ networks are vulnerable to hackers”