OverRide: Explore disassembly, binary exploitation & reverse-engineering
OverRide
Explore disassembly, binary exploitation & reverse-engineering through 10 little challenges.
In the folder for each level you will find:
- flag – password for next level
- README.md – how to find password
- source.c – the reverse-engineered binary
- dissasembly_notes.md – notes on asm
See the subject for more details.
Level Up
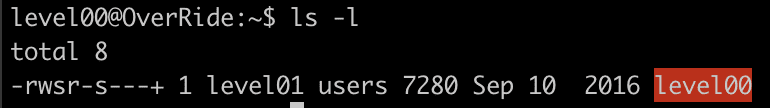
As the user level00 the goal is to read the password for user level01, found at /home/users/level01/.pass. However, the user level00 does not have permission to read this file.
In the home folder for user level00 is a binary level00 with SUID set and owner level01.
This means when we execute the binary level00, we do so with the permissions of the user level01.
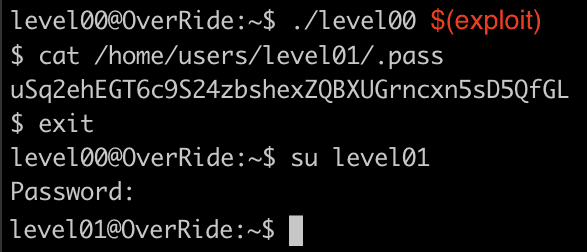
We must find a vulnerability in the binary level00 with gdb. Then exploit the vulnerability to run the system(“/bin/sh”), opening a shell as user level01 where we have permissions to read the password.
cat /home/users/level01/.pass
Then log in as user level01.
su level01
Repeat for each level.
Reverse-engineered binary
For each level, we reverse-engineered the original source.c by examining the gdb disassembly of the binary.
Levels Overview
- 0 – Hardcoded password
- 1 – Ret2Libc attack
- 2 – printf() format string attack
- 3 – Brute force password
- 4 – gets() stack overflow + Return-to-libc attack
- 5 – Shellcode in env variable + printf() format string attack
- 6 – Hash value discoverable with gdb
- 7 – Ret2Libc Attack on the unprotected data table
- 8 – Binary backs up a password via a symlink
- 9 – Off-by-one error