The Common Weakness Enumeration (CWE) Top 25 list for 2024 has been released, and it provides a...
Security researcher Snoolie K has published an in-depth analysis of a significant security flaw in WorkflowKit, which...
Recently, Palo Alto Networks has released an in-depth analysis of FrostyGoop, also known as BUSTLEBERM, a sophisticated...
CrowdStrike has revealed a new China-nexus state-sponsored adversary tracked as LIMINAL PANDA, which has been systematically targeting...
Veritas has released a security advisory regarding a critical remote code execution (RCE) vulnerability affecting multiple versions...
Aqua Nautilus security researchers have uncovered a novel attack vector where threat actors exploit misconfigured servers, particularly...
Ruckus APs running specific software versions are vulnerable to unauthenticated remote code execution attacks. Ruckus Networks has...
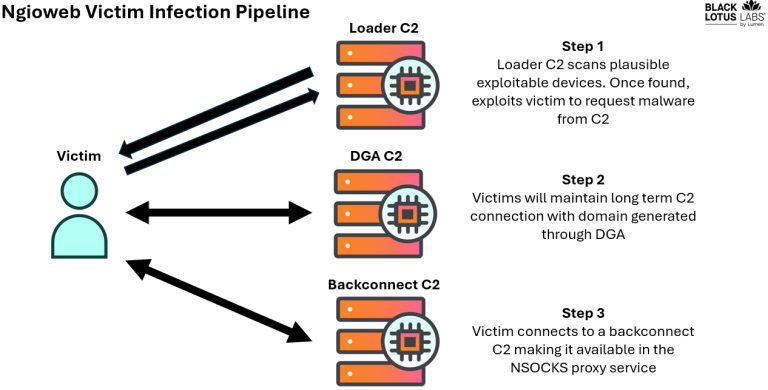
A recent report by Black Lotus Labs at Lumen Technologies has exposed the scale and sophistication of...
D-Link has issued a security announcement concerning several End-of-Life (EOL) and End-of-Service (EOS) router models, including the...
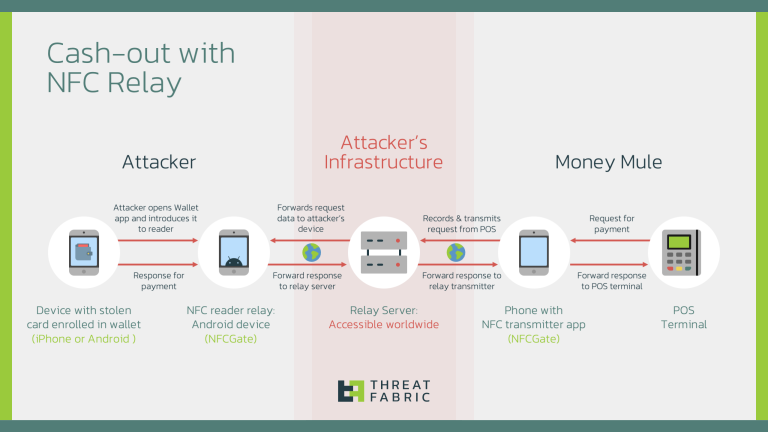
ThreatFabric reveals a new tactic allowing fraudsters to anonymously drain stolen credit cards linked to mobile wallets....
As the e-commerce market continues to grow, so does the allure of online shopping. However, the rising...
Qualys Threat Research Unit uncovers five local privilege escalation flaws, enabling unprivileged users to gain root access....
A recently discovered vulnerability in the Trend Micro Deep Security 20 Agent could have allowed attackers to...
The cybersecurity employment market is at a record-high level, and it is only going to get bigger...
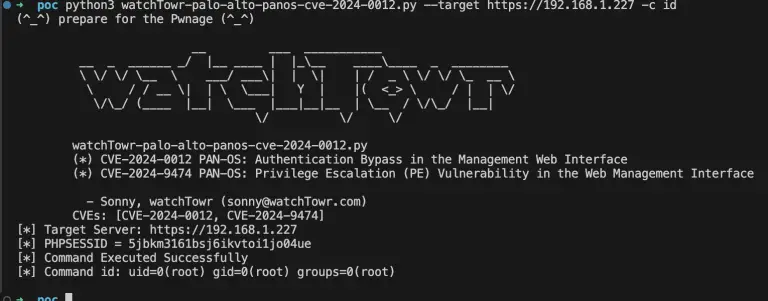
In a recent analysis, security researcher Sonny from watchTowr unveiled the technical intricacies of two zero-day vulnerabilities...