Over the past few months, the Unit 42 threat research team at Palo Alto Networks has discovered that the hacking organization Patchwork (also known as Dropping Elephant and Monsoon) has been conducting malicious attacks targeting targets in the South Asian subcontinent.
The organization took advantage of two EPS vulnerabilities in its attacks and attempted to disseminate its modified BADNEWS malware through bait files. This is a backdoor program that provides the organization with full control of infected devices.
According to Unit 42’s introduction, the lure documentation contains malicious embedded EPS files that can be exploited for vulnerabilities CVE-2015-2545 and CVE-2017-0261, which are two publicly disclosed vulnerabilities. Prior to January of this year, Patchwork was keen to use CVE-2017-0261, but by late January, the newly emerged bait document seems to have given up this loophole, but shifted to earlier disclosed CVE-2015-2545.
Bait documents appearing in recent events cover several themes, including the Pakistani Army’s recent military promotion activities, information related to the Pakistan Atomic Energy Commission, and information related to the Pakistani Ministry of the Interior.
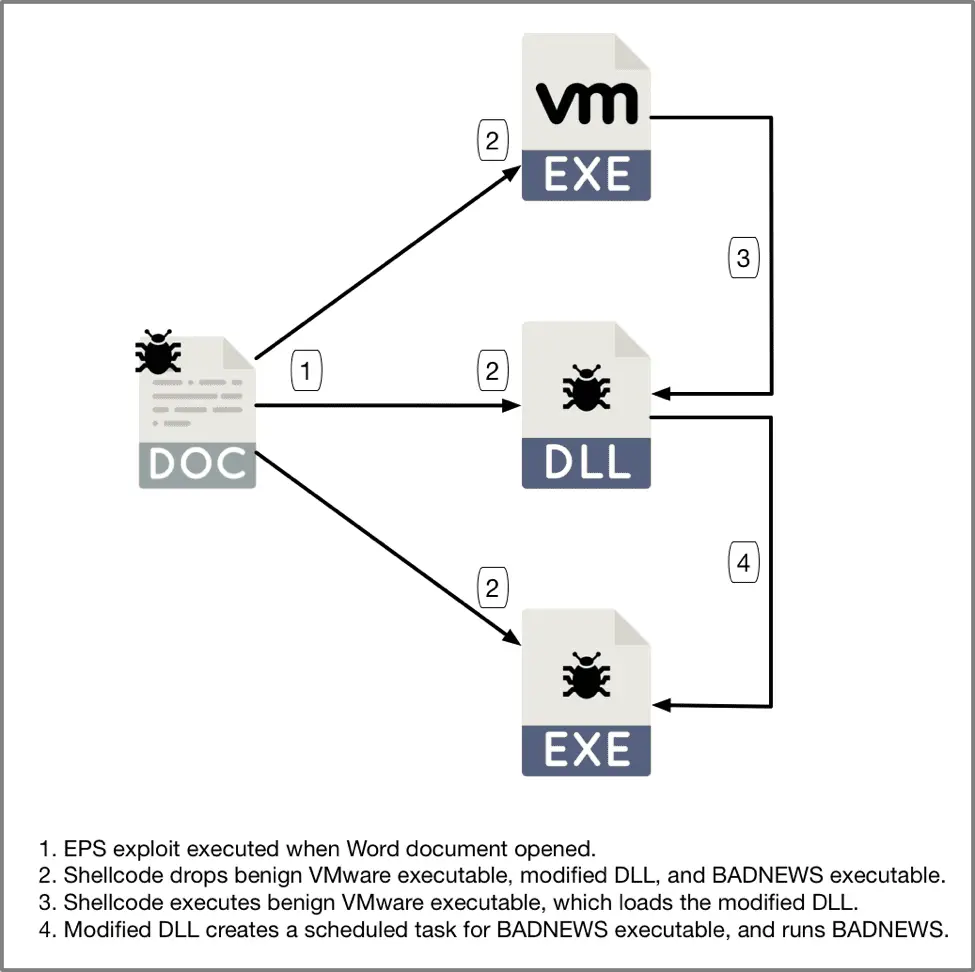
 Although the topics are different, the final payload of the bait’s document propagation is a modified BADNEWS update. When the shellcode in the malicious EPS file is executed, the following three files are downloaded:
Although the topics are different, the final payload of the bait’s document propagation is a modified BADNEWS update. When the shellcode in the malicious EPS file is executed, the following three files are downloaded:
- %PROGRAMDATA%\Microsoft\DeviceSync\VMwareCplLauncher.exe
- %PROGRAMDATA%\Microsoft\DeviceSync\vmtools.dll
- %PROGRAMDATA%\Microsoft\DeviceSync\MSBuild.exe
VMwareCplLauncher.exe is valid and signed VMware executable that provides the final payload of BADNEWS; vmtools.dll is a modified DLL that ensures the persistence of malware and loads MSBuild.exe; MSBuild.exe takes It uses the file names of legitimate Microsoft Visual Studio tools and is essentially the implementation of BADNEWS.
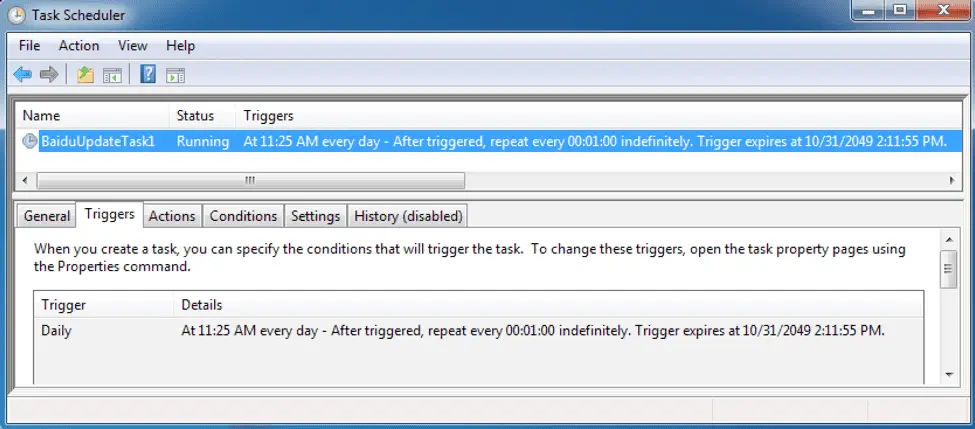
 After the file is downloaded, VMwareCplLauncher.exe will execute first and then load vmtools.dll. This DLL file creates a scheduled task named BaiduUpdateTask1 that attempts to run malicious MSBuild.exe every minute.
After the file is downloaded, VMwareCplLauncher.exe will execute first and then load vmtools.dll. This DLL file creates a scheduled task named BaiduUpdateTask1 that attempts to run malicious MSBuild.exe every minute.
The following figure shows the scheduled tasks created by vmtools.dll to ensure that BADNEWS can keep running on the infected device.
As stated at the beginning of the article, the BADNEWS malware family is often used as a backdoor to communicate over HTTP. It provides attackers with many features, including downloading and executing additional information, uploading documents, and screenshots.
Source, Image: paloaltonetworks