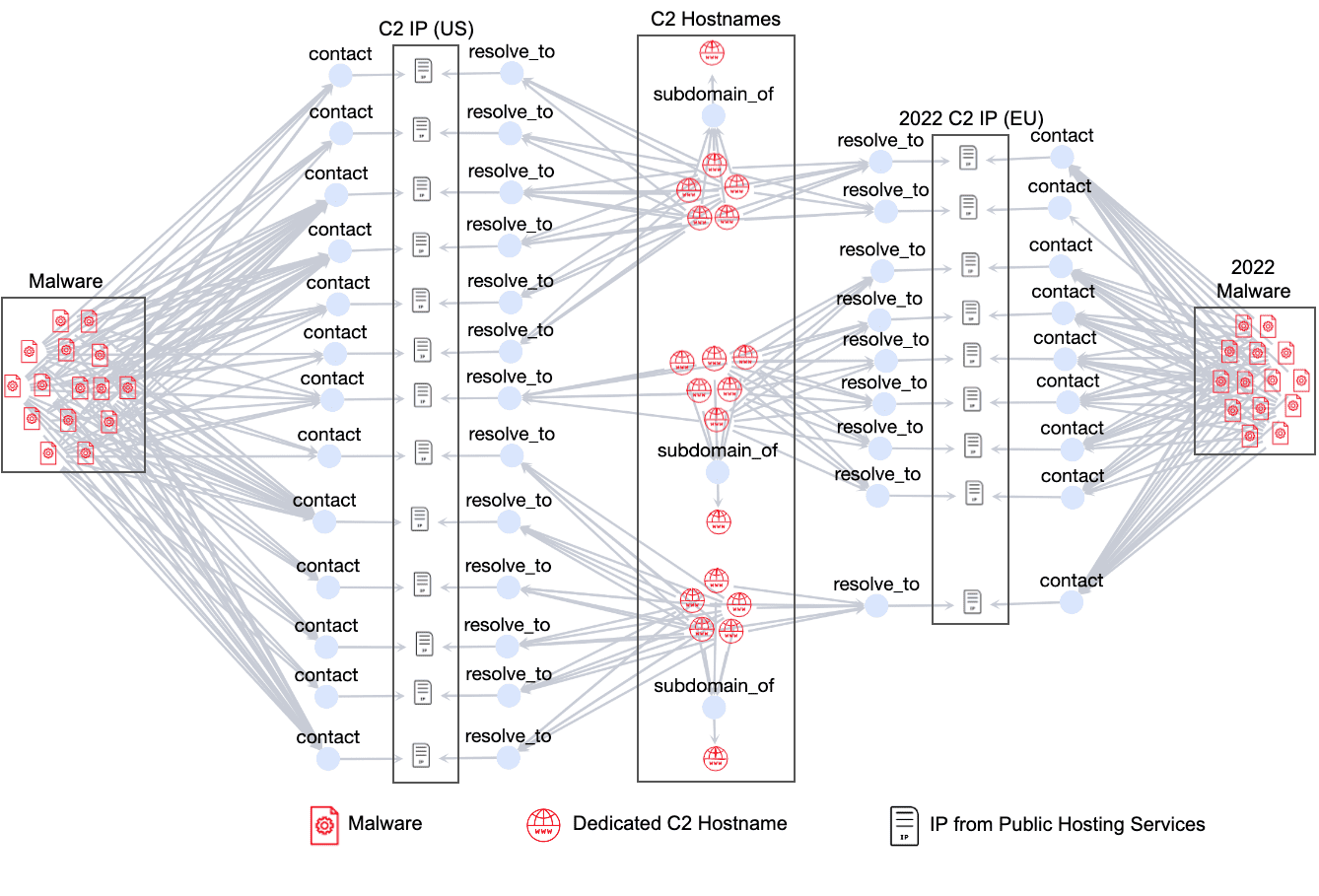
Network infrastructure of XorDDoS campaign | Image: Palo Alto Networks
Palo Alto Networks has recently unearthed a new wave of attacks emanating from the XorDDoS Trojan. A rigorous investigation led to the discovery of a concealed network infrastructure responsible for a significant amount of command and control (C2) traffic. Comparisons of the recent attacks to a previous campaign in 2022 revealed that while the attacking domains remained unchanged, the attackers had shifted their infrastructure to hosts on legitimate public hosting services.
Many security firms have classified these C2 domains as malicious and placed barriers against them. Yet, active malware traffic persists, suggesting that defense mechanisms need to extend beyond just blocking known malicious hosts.

The XorDDoS Trojan specifically targets Linux devices, turning them into remote-controlled ‘zombies’. Once infected, these devices can be manipulated to launch distributed denial of service (DDoS) attacks. The recent campaign was most active between July 31 and August 5, 2023, after which a surge on August 12 saw the delivery of 30 unique malware variants.
Preceding a successful device compromise, attackers initiated scanning, using HTTP requests to identify vulnerabilities. The primary focus was on detecting an HTTP service prone to directory traversal, a vulnerability that could allow unauthorized access to server files. Many victim machines received scanning traffic attempting to access the ‘/etc/passwd’ file, which generally precedes C2 requests.
Once inside, the attackers leveraged SSH brute-force attacks to gain initial access, then proceeded to download and deploy malware. The XorDDoS Trojan employs an XOR encryption key to encrypt its execution data. Upon activation, the Trojan harvests essential information from the infected device, communicating with the C2 server using this data.
XorDDoS also employs multiple persistence mechanisms. For instance, it sets up recurring tasks to execute malware every three minutes and ensures the malware runs at system startup. To further camouflage its presence, it runs as a background service, mimicking legitimate processes.
A telling aspect of the Trojan is its ability to self-replicate, producing numerous malware executables. This behavior can confuse certain detection systems that rely on file hashes. Over the course of eight months, 26,000 replicated malware samples were identified across several industries, including semiconductor, telecom, transportation, finance, insurance, and retail sectors.
The investigation also shed light on the C2 domains associated with the attacks. These domains, registered for malicious traffic purposes for years, showed patterns of heavy activity during specific months. Despite similarities between the 2022 and 2023 campaigns, the attackers had changed IP addresses for the C2 domains in anticipation of the recent attacks. By mid-August 2023, the campaign reached its peak, generating nearly a million DNS requests for the C2 domains in a single day.
A significant challenge for security vendors is that the malicious C2 domains share IP addresses with legitimate domains. Therefore, simply blocking these IP addresses is not a feasible solution. This fact highlights the urgency of advancing protective measures beyond just targeting known malicious hosts.
An analysis of the network structures of the XorDDoS attacks showed a distinct geographical shift. While the 2022 campaign spread its C2 servers across European countries, the recent campaign primarily targeted the United States. Regardless of their location, the IP addresses are linked to a consistent set of C2 hostnames.
In conclusion, the XorDDoS Trojan campaign presents a nuanced threat landscape. Its shared web hosting infrastructure makes classifying connections as benign or malicious a challenge. However, by focusing on patterns of multiple connections within a short period, security professionals can better discern C2 activity from regular network traffic. Leveraging these insights will be pivotal in crafting advanced signatures to detect and counteract malware activities in the future.