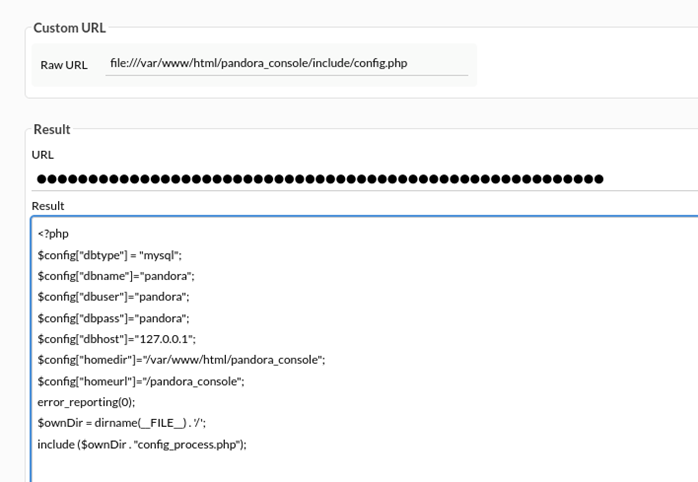
NCC Group’s security researchers unearthed 18 vulnerabilities in PandoraFMS Enterprise v7.0NG.767, a network monitoring and management application of enterprise scale.
PandoraFMS serves as a central hub for systems administrators to monitor and manage the state of computers (agents) across a network. However, the vulnerabilities identified pose significant risks, ranging from unauthenticated account takeovers to remote code execution.
The vulnerabilities discovered are diverse, each presenting unique challenges:
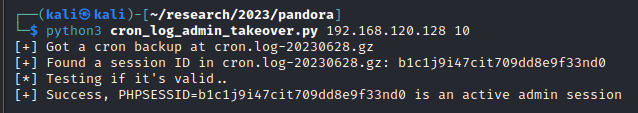
1. Admin Account Takeover via Cron Log File Backups (CVE-2023-4677, CVSS 9.9): Classified as critical, this vulnerability allows attackers to execute arbitrary commands on all connected agents, leading to mass compromise.
2. Remote Code Execution via MIBS File Uploader (CVE-2023-41788, CVSS 7.6): A high-risk flaw that could lead to the full compromise of all accounts and agents registered with the server.
3. Arbitrary File Read As Root Via GoTTY Page (CVE-2023-41808, CVSS 7.1): This medium-risk vulnerability enables attackers to retrieve sensitive data, including password hashes, potentially leading to full host privilege escalation.
4. Unauthenticated Admin Account Takeover Via Malicious Agent and XSS (CVE-2023-41789, CVSS 8.2): Another high-risk vulnerability that permits attackers to execute arbitrary commands on all connected agents.
The remaining vulnerabilities, while varying in severity, collectively highlight a pressing need for robust security measures in enterprise-level applications.
In response to these findings, PandoraFMS has released updates across versions v773, v774, and v775. These updates address the identified vulnerabilities, showcasing the company’s commitment to security.
These vulnerabilities underscore the critical importance of comprehensive security strategies in network monitoring tools. They serve as a stark reminder of the potential risks inherent in complex software systems and the ongoing need for vigilance in cybersecurity practices.