paragon v0.4.4 releases: Red Team engagement platform
paragon
Paragon is a Red Team engagement platform. It aims to unify offensive tools behind a simple UI, abstracting much of the backend work to enable operators to focus on writing implants and spend less time worrying about databases and css. The repository also provides some offensive tools already integrated with Paragon that can be used during engagements.
This repository is still under heavy development and is not ready for production use. When it is considered stable, a V1.0.0 tag will be released. Until then, the API may encounter breaking changes as we continually simplify our design. Please read the developer documentation below if you’d like to help us reach this milestone faster.
Feature Highlights
- Easily integrate custom tools to unify operations behind a single interface
- Query the Red Team knowledge graph using a provided GraphQL API
- Event emission for low latency automation and real-time processing
- Python-like scripting language for deployments, post-exploitation, and more
- Cross-platform implants & deployment included
- Record operator activity to conveniently aggregate into a post-engagement report for review
Component Overview
Scripting Language
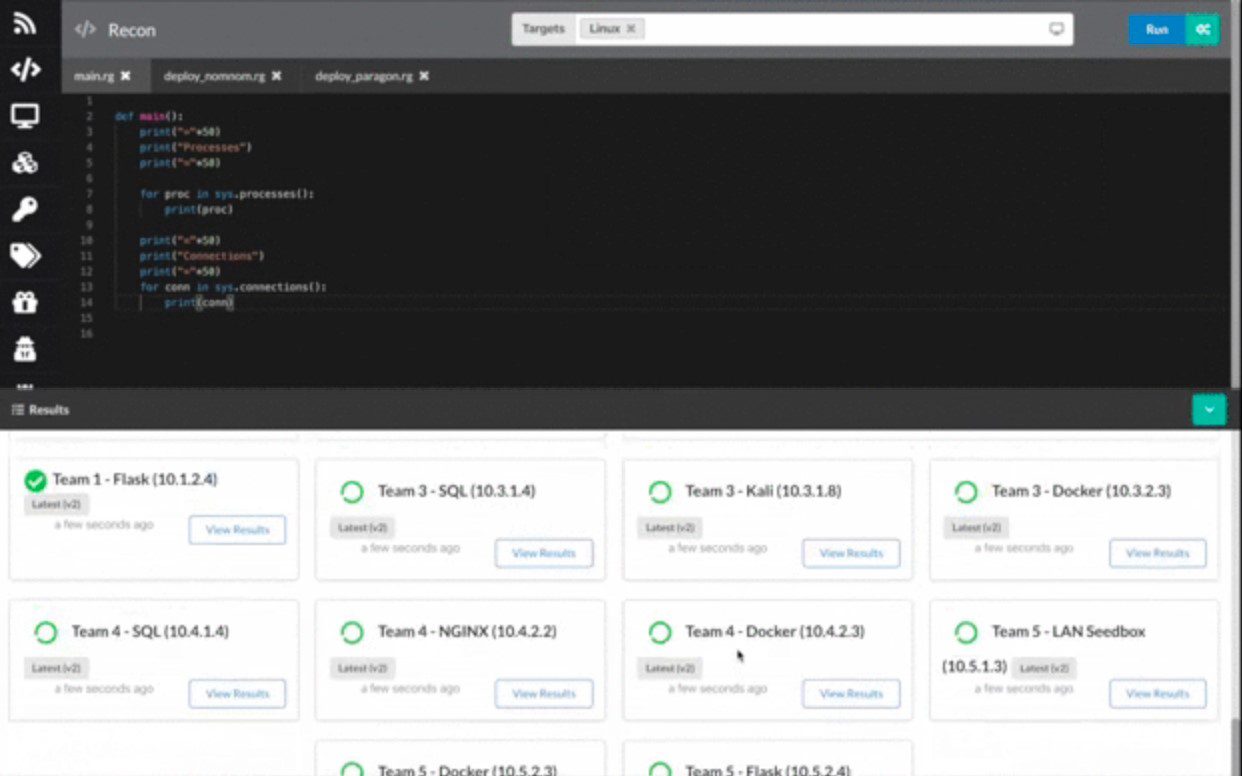
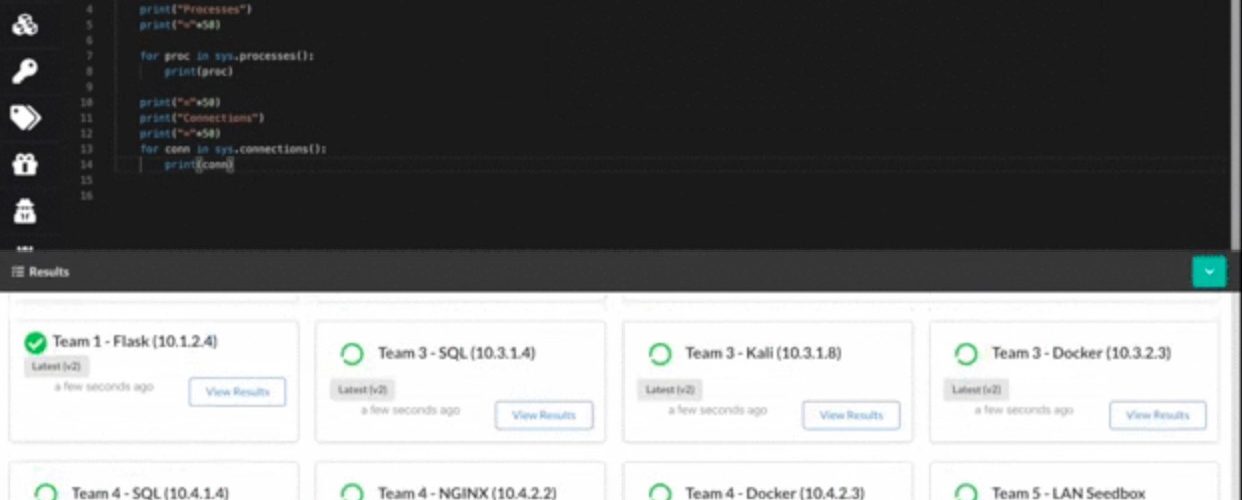
Most components in this repository rely on a Python-like scripting language which enables powerful control and customization of their behavior. The language is a modified version of Google’s starlark, extended with cross-platform functionality for operators. This also enables tools like the agent and dropper (discussed below) to execute tasks without relying on system binaries (curl, bash, etc). All operations are executed as code in Golang, so it’s intuitive to add additional functionality to the scripting environment. Here is an example script:
Teamserver
Provides a simple web application and GraphQL API to interface with a Red Team knowledge graph, unifying tools behind a centralized source of truth and abstracting many tedious backend concerns from operators. Integrate your custom tools with the Teamserver (using the GraphQL API or event subscriptions) to save time on the backend work. The Teamserver records all activity, so with all of your tools unified in one place, writing post-engagement reports becomes significantly easier.
Built-In Tools
The below tools are also included within the repository. They can easily be extended to fit many cross-platform use cases.
Dropper
- Fully cross-platform
- Statically compile assets into a single binary
- Provides Python-like scripting language for custom deployment configuration
Paragon provides a tool for packaging assets (binaries, scripts, etc.) into a single binary that when executed will execute your custom deployment script that may write assets to the filesystem, launch processes, download files, handle errors, and more. It is fully cross-platform and statically compiled, providing reliable deployments. If you wish to extend its functionality, you may simply extend the generated golang file before compiling it.
Agent
- Fully cross-platform
- Provides Python-like scripting language for post-exploitation
- Modular communication mechanisms, only compile in what you need
- Utilize multiple options to ensure reliable callbacks
- Customize how the agent handles communication failures
An implant that executes tasks and reports execution results. It is configured by default to execute tasks using Paragon’s Python-like scripting language and to communicate with a C2 via http(s). It is written in Go and can be quickly modified to add new transport methods (i.e. DNS), execution options, failover logic, and more.
C2
- Lightweight deployment
- Highly performant, able to handle thousands of Agents
- Dependent on system resources and available bandwidth
- Distributed service, utilize as many C2s as you’d like
Acts as a middleman between the Agent and the Teamserver. It handles agent callbacks for a variety of communication mechanisms and provides it with new tasks from the teamserver queue.
Runner
- Low latency, real-time task execution
- Easily extended to add support for more communication mechanisms
- Distributed service, utilize as many runners as you’d like
Instead of waiting for a callback, some situations might require a forward connection to quickly execute a task and view its output. The runner accomplishes this by subscribing to task queues and establishing a connection to the target machine (i.e. using ssh). This enables shell-like integrations to utilize the same interface as implants and C2s. It also allows for initial implant deployment to be conducted through this interface.
Scanner
- Monitor reachable target services
- Automate responses when services become (un)available
- Provide network information to the knowledge graph, which may be utilized by other tools
- Distributed service, utilize as many scanners as you’d like
Monitor target network activity and visible services. Map out a graph of the engagement network, and trigger automation on state changes (i.e. ssh becomes available).
Install & Use
Copyright (C) 2019 KCarretto