
Mandiant has uncovered alarming evidence of a sophisticated Iranian state-sponsored cyber campaign orchestrated by UNC1860, a threat actor likely affiliated with Iran’s Ministry of Intelligence and Security (MOIS). Known for its specialized tools and passive backdoors, UNC1860 is emerging as a formidable player in the cyber espionage landscape, targeting critical networks across the Middle East, particularly in government and telecommunications sectors.
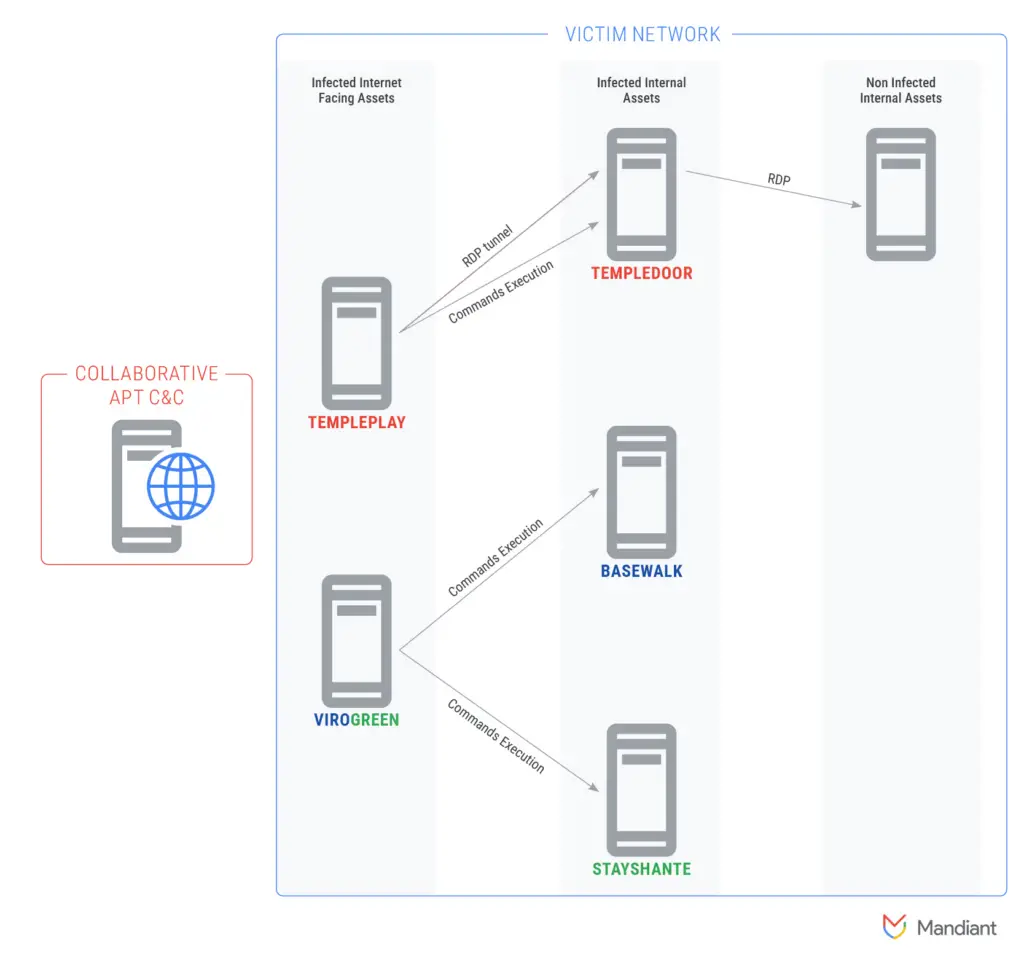
UNC1860 has garnered attention for its unique ability to gain persistent access to high-priority networks. By employing GUI-operated malware controllers such as TEMPLEPLAY and VIROGREEN, the group facilitates remote access and offers third-party actors the tools needed to control infected systems. These tools are indicative of a broader role that UNC1860 plays in the Iranian cyber ecosystem: providing initial access for more destructive cyber operations.
While Mandiant cannot conclusively prove that UNC1860 was responsible for specific attacks, the group’s tactics resemble those of other Iran-based actors like Shrouded Snooper and Scarred Manticore, which targeted Israel and Albania in high-profile campaigns using malware like BABYWIPER and ROADSWEEP.
A key strength of UNC1860 is its ability to deploy passive backdoors designed for long-term network access. These backdoors are stealthy, leveraging legitimate software components to avoid detection. For example, the group repurposed a legitimate Iranian antivirus software driver to create WINTAPIX, a Windows kernel mode driver capable of evading security tools.
Mandiant’s report highlights the group’s reverse engineering prowess, particularly in Windows kernel components, which allows them to design backdoors that remain hidden for extended periods. These capabilities position UNC1860 as a powerful cyber threat, capable of supporting espionage and network attack operations with minimal risk of detection.
UNC1860’s modus operandi centers on initial access and the exploitation of vulnerable internet-facing servers. Once inside a target environment, the group deploys web shells like STAYSHANTE and SASHEYAWAY, which serve as gateways for deeper infiltration. These tools provide external actors with remote access to compromised systems and enable the deployment of more sophisticated payloads like TEMPLEDOOR, FACEFACE, and SPARKLOAD, which can be used for both espionage and disruptive operations.
Mandiant’s analysis of these tools reveals that they are designed to bypass traditional command-and-control (C2) detection methods. For instance, UNC1860’s passive implants do not initiate outbound traffic, making them difficult to detect through network monitoring. Instead, they rely on encrypted HTTPS traffic and exploit VPN nodes, allowing the group to blend in with legitimate network traffic.
UNC1860 has also been linked to APT34, another Iranian cyber-espionage group. Mandiant observed several instances where organizations compromised by APT34 were previously targeted by UNC1860. This overlap suggests a coordinated effort between the two groups, with UNC1860 providing initial access and APT34 handling lateral movement and deeper exploitation.
One of the most concerning aspects of UNC1860’s activity is its regional focus. Mandiant has documented numerous instances where the group targeted Saudi Arabia and Qatar, exploiting VPN servers and validating credentials across multiple domains. The group’s ability to scan for vulnerabilities in critical infrastructure, such as telecommunications and government networks, poses a significant threat to the region’s cybersecurity landscape.
Related Posts:
- Iranian Cyberespionage Campaign Targets Iraqi Government
- Menorah Malware: APT34’s Latest Cyberweapon Unmasked by Trend Micro
- Mandiant Exposes Ongoing Exploits Against Citrix Users
- The Iranian government blocked Instagram and Telegram
- A New Set of Tools for Cyber Espionage: Targeting the Middle East, Africa, and the US