pack: Password Analysis and Cracking Toolkit
PACK (Password Analysis and Cracking Toolkit) is a collection of utilities developed to aid in the analysis of password lists in order to enhance password cracking through pattern detection of masks, rules, character-sets and other password characteristics. The toolkit generates valid input files for Hashcat family of password crackers.
NOTE: The toolkit itself is not able to crack passwords, but instead designed to make the operation of password crackers more efficient.

Download
git clone https://github.com/iphelix/pack.git
Use
Selecting passwords lists for analysis
Before we can begin using the toolkit we must establish selection criteria of password lists. Since we are looking to analyze the way people create their passwords, we must obtain as large of a sample of leaked passwords as possible. One such excellent list is based on RockYou.com compromise. This list both provides large and diverse enough collection that provides good results for common passwords used by similar sites (e.g. social networking). The analysis obtained from this list may not work for organizations with specific password policies. As such, selecting sample input should be as close to your target as possible. In addition, try to avoid obtaining lists based on already cracked passwords as it will generate statistics bias of rules and masks used by an individual(s) cracking the list and not actual users.
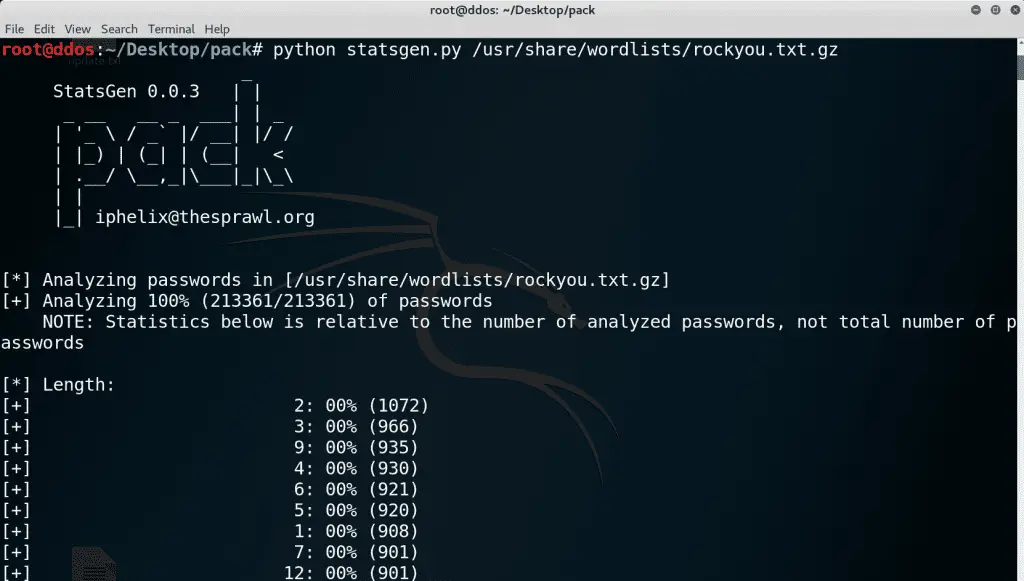
The most basic analysis that you can perform is simply obtaining most common length, character-set and other characteristics of passwords in the provided list. In the example below, we will use ‘rockyou.txt’ containing approximately 14 million passwords. Launch `statsgen.py` with the following command line:
$ python statsgen.py rockyou.txt
Tutorial
Copyright (c) 2013, Peter Kacherginsky





