In the ever-evolving landscape of cybersecurity, a new name has emerged from the shadows, sending chills down the spines of digital defenders worldwide – Forest Blizzard. This group, also known by the moniker STRONTIUM and tracked by Microsoft, represents a formidable force in the realm of cyber threats.
Hailing from Russia, Forest Blizzard is not just any hacking collective. It’s a state-sponsored entity, linked to the notorious Unit 26165 of the Russian Federation’s military intelligence agency, the GRU. This group’s primary targets? Government, energy, and transportation sectors, as well as non-governmental organizations, spread across the United States, Europe, and the Middle East.
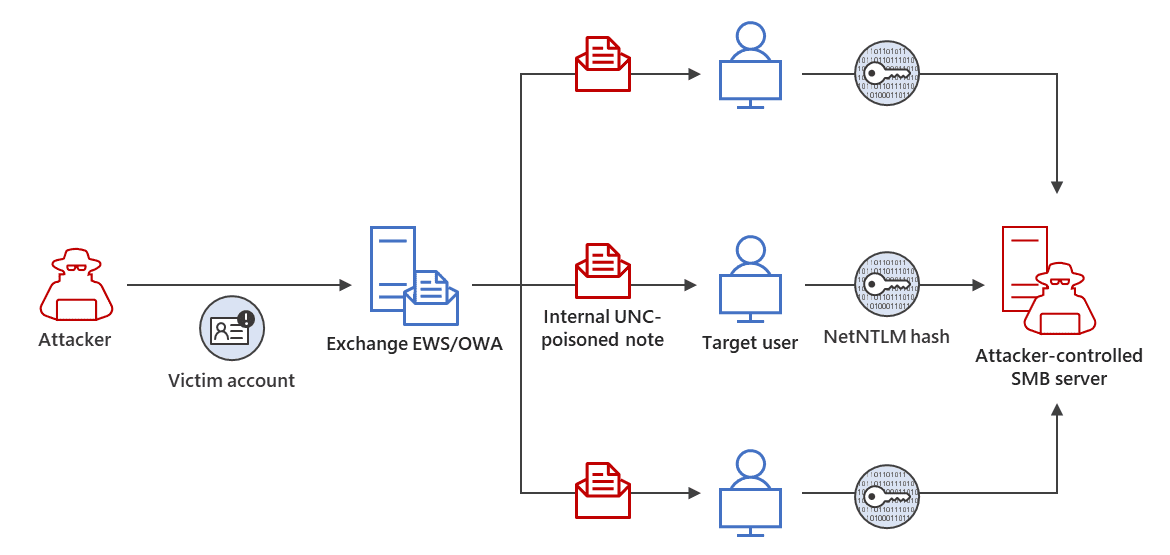
Forest Blizzard’s modus operandi is a symphony of sophisticated cyber exploits. Their latest performance? Actively exploiting CVE-2023-23397, a vulnerability in Microsoft Exchange servers, to gain unauthorized access to email accounts. But their repertoire doesn’t end there. They’ve also leveraged vulnerabilities like WinRAR CVE-2023-38831, primarily against Ukrainian government targets, and an array of other CVEs, showcasing their adaptability and thirst for exploiting any crack in digital defenses.

The Polish Cyber Command (DKWOC), in an impressive display of international cooperation and digital prowess, partnered with Microsoft to combat the Forest Blizzard menace. Together, they have developed tools and strategies to identify and mitigate the techniques used by this actor.
Forest Blizzard’s approach is one of stealth and precision. By modifying permissions to mailbox folders within Microsoft Exchange servers, they’ve created a covert pathway to email correspondence. This technique, alongside their use of the Microsoft Outlook Vulnerability (CVE-2023-23397) and password-spraying tactics, reveals a high level of sophistication and an intimate knowledge of their targets’ systems.
The actions of Forest Blizzard are not isolated incidents but part of a widespread campaign that aligns with activities described by the USA and British governments as related to APT28 and Forrest Blizzard. This group is a persistent, evolving threat with global reach.
POL Cyber Command recommends the implementation of the following guidelines.
4. Verification of mailbox delegation settings in the entire Exchange organization.
6. Audit of email access methods to identify potential attack vectors.