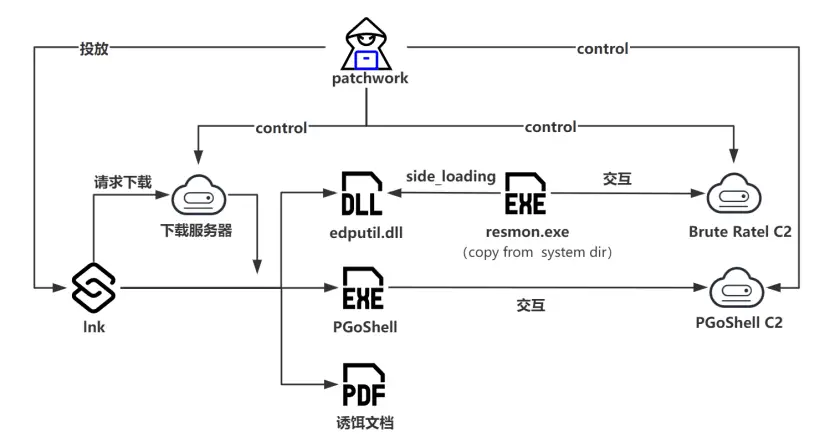
Attack Chain | Image: Knownsec 404 Advanced Threat Intelligence
Recently, the Knownsec 404 Advanced Threat Intelligence team identified suspicious activity by the Patchwork group targeting Bhutan. The attack utilized an updated backdoor written in Go, known as PGoShell, as well as a new hacking tool, Brute Ratel C4. This incident underscores the group’s commitment to technological advancement.
Patchwork, also known as Dropping Elephant, has been active since 2014, targeting governmental, defense, and diplomatic organizations, as well as universities and research institutions in East and South Asia.
The attack commenced with the distribution of a decoy file in .lnk format named Large_Innovation_Project_for_Bhutan.pdf.lnk. This file appeared to be a PDF document but, when executed, downloaded and launched several malicious components. Specifically, the following files were downloaded:
- A decoy document to distract users.
- The malicious library edputil.dll, masquerading as a legitimate file.
- The file Winver.exe, used for further propagation of the malware.
Tools and Methods
- Brute Ratel C4Brute Ratel C4 is a new tool used by attackers for managing file systems, port scanning, uploading and downloading files, and capturing screens. During the attack, this tool was loaded into memory, complicating its detection by security measures. Traditional defense mechanisms were circumvented through sophisticated anti-virtualization and anti-debugging techniques.
- PGoShellPGoShell, developed in Go, has been significantly enhanced. It now supports remote control, screen capture, and file downloads. The tool collects system information, including IP address, OS version, username, and processor architecture, and transmits this data to the attackers’ server. All transmitted information is encrypted using the RC4 algorithm and encoded in base64.
This attack highlights the growing capabilities of the Patchwork group, which is actively updating its tools and methods. The use of Brute Ratel C4 and the improved PGoShell demonstrates a high level of sophistication and preparedness within the group.
Patchwork continues to evolve its technologies and techniques, making their attacks increasingly complex and difficult to detect. This necessitates enhanced cybersecurity measures and continuous monitoring of suspicious activities by targeted organizations.
Related Posts:
- Volexity: Indian APT hacker organization Patchwork target US think tanks
- Palo Alto Networks: Patchwork hacker group is targeting the Indian Subcontinent
- The Hidden Threat: Android Apps with VajraSpy RAT Exposed