pathbrute v0.0.10 releases: brute force directories and files names on web/application servers
pathbrute
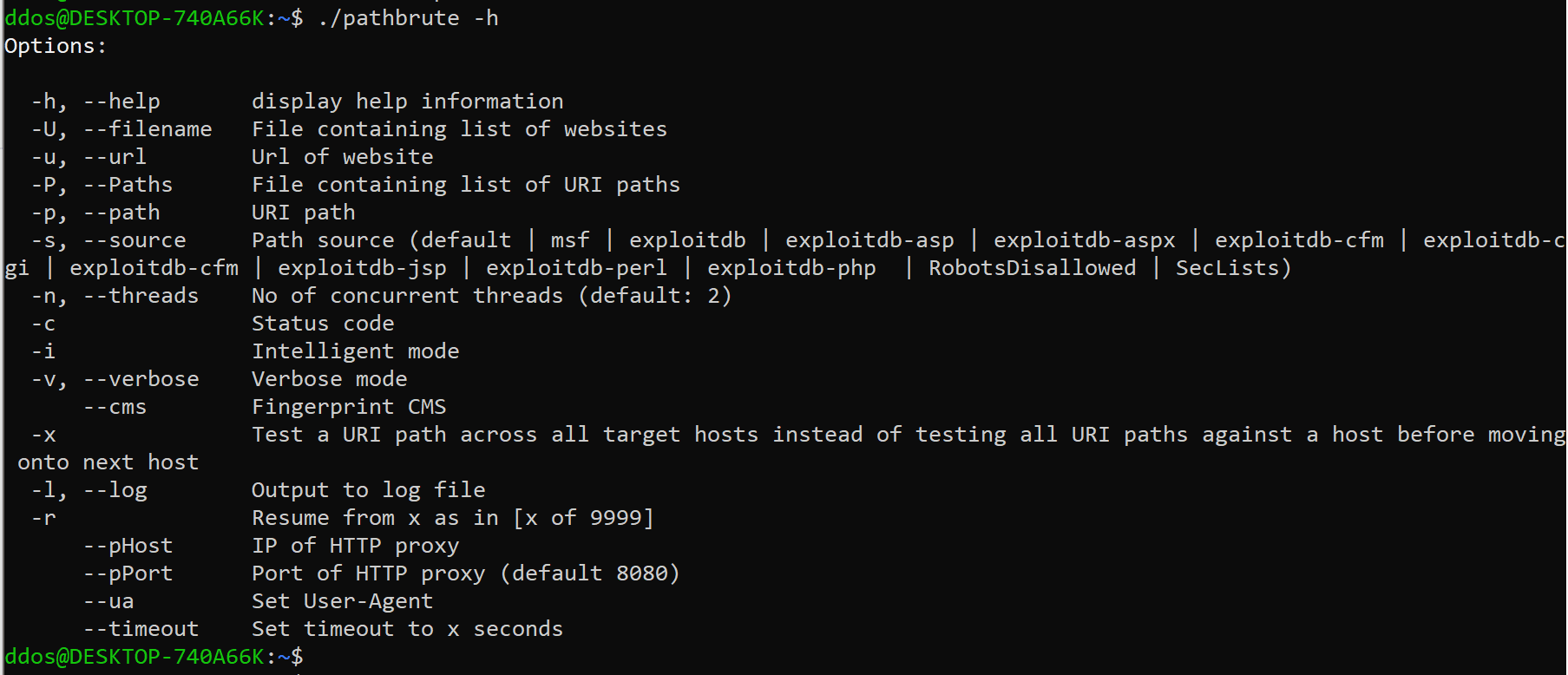
Pathbrute is a DirB/Dirbuster type of tool designed to brute force directories and files names on web/application servers.
However, it has some new tricks. It is no longer a dumb directories/files brute force tool if you use the -v and -i option.
Some of it includes:
- Wordlists from Exploit databases and Metasploit
- Identify interesting URLs even though websites return HTTP status code 200 for all URI paths.
- Identify valid paths that require authentication (HTTP status code 401)
- Reduce the number of results for wordlists with URI paths with nested directories
Pathbrute has a number of wordlists from Metasploit/exploit-database and other sources that it uses to discover interesting content on servers.
It contains/uses a number of self-compiled wordlists for identifying “interesting” content and potentially vulnerable websites.
- More than 13924 URI paths from Exploit-Database
- URI paths from Metasploit Framework
pathBrute can also use wordlists from other sources if you prefer.
It can also be used for identifying if any type of CMS (Joomla, WordPress, and Drupal) is running on the target websites and fingerprint the versions of the CMS using the –cms option.
Changelog v0.0.10
- 298f89f add -e option to exclude specific status code from stdout (E.g. 404) – reduce noise output
- 1d6f960 add /api – traefik instances /api endpoint discloses private keys of SSL certificates
- dd732f6 add packetstorm to README.md
- 6c18ed8 update README.md
- 994f4b0 fix bug abt being unable to access pathbrute.sqlite in Docker
- f652bd9 update Dockerfile
- 95a4e3f update README.md
- 1c12725 update README and msfPaths.txt
- c6cbbd6 add –query/-q option to lookup URI paths in ExploitDB database and also added “code=xxx to the status code
- output for easier grep
- a92e66c update README.md #9
- d2e8da2 update wordlists
- eeba6a7 update exploitdb paths
Usage

Source: https://github.com/milo2012/