Pawn Storm APT Actor: A Persistent Cybersecurity Threat
Security researchers from Trend Micro detailed Pawn Storm, also known as APT28 and Forest Blizzard one persistent actor that has managed to maintain its relevance for over two decades. This advanced persistent threat (APT) group has proven its staying power by repeatedly targeting high-value individuals and organizations worldwide. Despite their seemingly repetitive tactics, Pawn Storm has continued to adapt and evolve, making them a formidable force in the world of cybersecurity.
One of Pawn Storm’s distinctive traits is its persistent use of phishing email campaigns that have spanned over a decade. These campaigns may seem antiquated, but they remain a potent tool in the group’s arsenal. While the tactics and infrastructure behind these campaigns change gradually, they still offer valuable insights into Pawn Storm’s operations, including more advanced attacks.

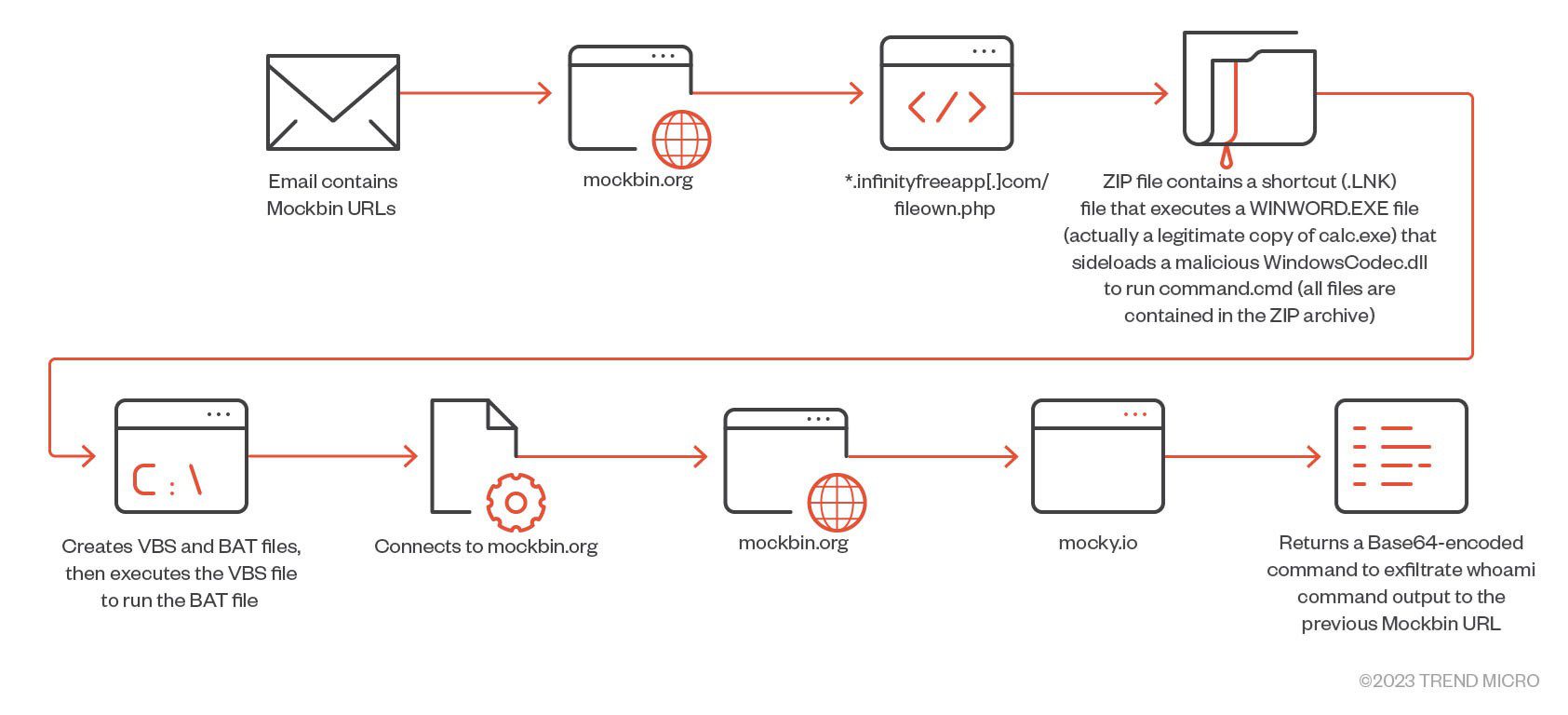
An example of a username exfiltration routine from Pawn Storm
It’s crucial to remember that the group’s apparent lack of sophistication does not undermine their success. Pawn Storm has compromised thousands of email accounts over the years, with some attacks being cleverly designed and stealthy, while others employ advanced techniques. The noise generated by their repetitive campaigns often obscures the subtlety and complexity of their initial intrusion and post-exploitation actions within victim organizations.
From April 2022 to November 2023, Pawn Storm embarked on a significant campaign involving Net-NTLMv2 hash relay attacks. These attacks targeted various government departments, including those dealing with foreign affairs, energy, defense, transportation, labor, social welfare, finance, and more. The group’s broad range of targets spanned across Europe, North America, South America, Asia, Africa, and the Middle East.
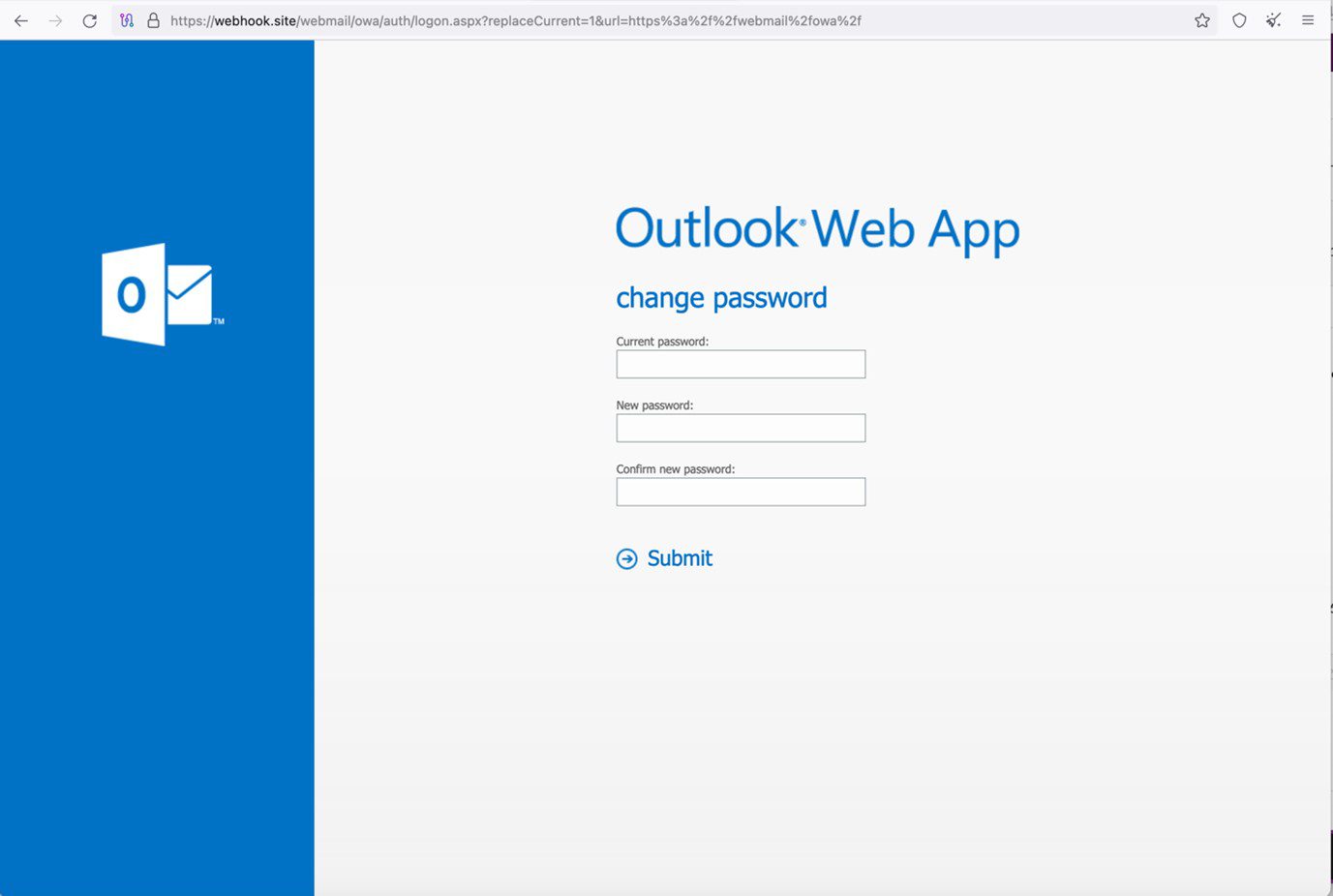
Pawn Storm’s credential phishing website using webhook[.][site URLs in November and December 2023 | Image: Trend Micro
Pawn Storm’s campaigns have yielded significant success, with thousands of email addresses breached. These compromised accounts are not only used for information gathering but also serve as infrastructure for launching further attacks. Their impact spans across various sectors, from government and defense to energy and transportation.
To maintain their anonymity and conceal their tracks, Pawn Storm employs a diverse range of tools, including VPN services, Tor, data center IP addresses, and compromised EdgeOS routers. They have also compromised email accounts worldwide, which they use as launching pads for spear-phishing attacks. Moreover, they leverage free services such as URL shorteners, free file hosting, and free email services.
In March 2023, a critical vulnerability, CVE-2023-23397, was patched in Outlook. This vulnerability, which required no user interaction, was exploited by Pawn Storm through an extended MAPI property with a UNC path to an attacker-controlled SMB server. This enabled the attacker to capture the victim’s Net-NTLMv2 hash, paving the way for a hash relay attack against other systems. This campaign began around April 2022 and lasted until at least August 2023.
Pawn Storm initially used hacked email accounts in the Middle East and Asia, relying on VPN exit nodes like Cactus VPN. Later, they shifted to using compromised EdgeOS routers instead of VPN exit nodes, incorporating more elaborate methods, including scripts hosted on Mockbin.
Pawn Storm’s use of anonymization layers, such as Tor and commercial VPN networks, was apparent in their spear-phishing emails. Their utilization of EdgeOS routers for spear-phishing, exploiting CVE-2023-23397, and proxying credential theft added another layer of complexity. While it remains uncertain whether Pawn Storm compromised these routers or used already compromised ones, patterns suggest that many were compromised.
Pawn Storm launched a credential phishing campaign against European governments in late 2023. This campaign shared similarities with their Net-NTLMv2 hash relay attacks, including the use of the same computer name and spear-phishing techniques.
In October 2022, Pawn Storm adopted a unique approach, sending spear-phishing emails with a small information stealer as an attachment. This stealer, without a command-and-control server, operated independently, exfiltrating specific file types and uploading them to a free file-sharing service.
Pawn Storm, a cyber threat that has persevered for over two decades, continues to adapt and evolve. From brute-force attacks to more sophisticated techniques, they remain a formidable adversary in the cybersecurity realm. Their ability to maintain anonymity through anonymization layers and their unorthodox methods of information stealing showcase their determination to breach high-profile targets worldwide.





