SharpShooter: Payload Generation Framework
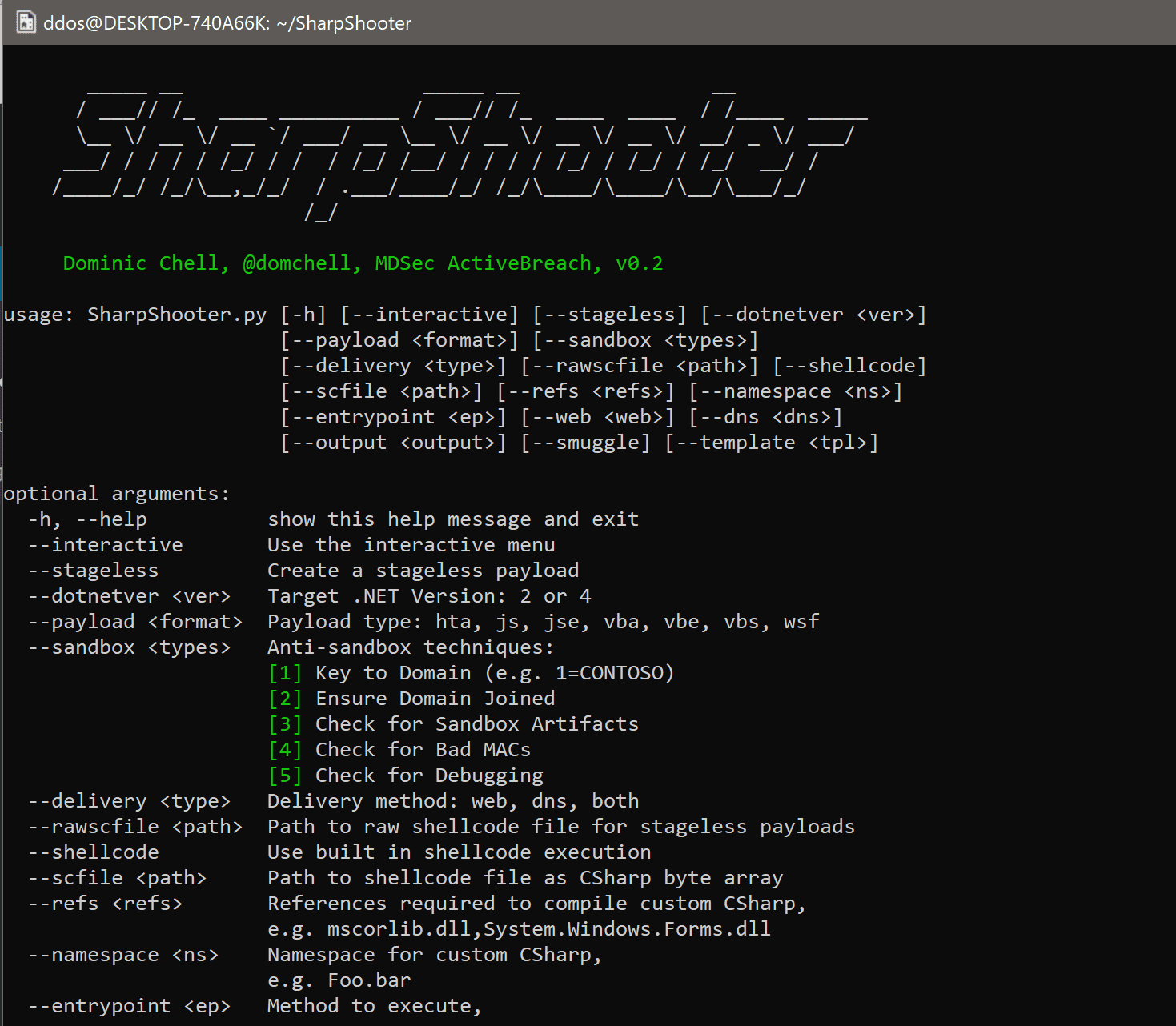
SharpShooter is a payload creation framework for the retrieval and execution of arbitrary CSharp source code. It is capable of creating payloads in a variety of formats, including HTA, JS, VBS, and WSF. It leverages James Forshaw’s DotNetToJavaScript tool to invoke methods from the SharpShooter DotNet serialized object. Payloads can be retrieved using Web or DNS delivery or both; it is compatible with the MDSec ActiveBreach PowerDNS project. Alternatively, stageless payloads with embedded shellcode execution can also be generated for the same scripting formats.
SharpShooter payloads are RC4 encrypted with a random key to providing some modest anti-virus evasion, and the project includes the capability to integrate sandbox detection and environment keying to assist in evading detection.
It includes a predefined CSharp template for executing shellcode with staged and stageless payloads, but any CSharp code can be compiled and invoked in memory using reflection, courtesy of CSharp’s CodeDom provider.
Finally, it provides the ability to bundle the payload inside an HTML file using the Demiguise HTML smuggling technique.
SharpShooter targets v2, v3, and v4 of the .NET framework which will be found on most end-user Windows workstations.

Installation
git clone https://github.com/mdsecactivebreach/SharpShooter.git
pip install -r requirements.txt
Author: Dominic Chell, MDSec ActiveBreach @domchell, and @mdseclabs





