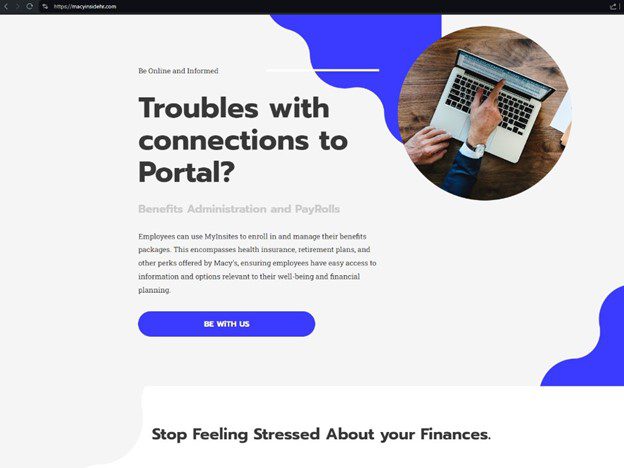
Example of strange language on the phishing page | Image: Silent Push
Silent Push Threat Analysts have uncovered a large-scale phishing operation dubbed the “Payroll Pirates,” which leverages sophisticated techniques to target employees’ payroll information. This campaign, which primarily exploits HR portals such as Workday, has affected numerous high-profile organizations, including retailers, healthcare providers, and government agencies.
At its core, the Payroll Pirates campaign involves redirecting payroll funds by infiltrating employee HR portals. Silent Push explains, “The threat actors have been utilizing malicious search advertising campaigns with sponsored phishing websites and spoofed HR pages via Google to lure unsuspecting victims.” Once inside an employee’s portal, the attackers modify banking information to reroute payroll funds into accounts they control.
The campaign employs an arsenal of tactics and resources:
- Search Ads with Brand Keywords: Threat actors buy search ads targeting brand-specific keywords to ensure their phishing sites appear at the top of search results.
- Website Builders for Rapid Deployment: Builders like Leadpages, Mobirise, and Wix are used to create phishing sites swiftly. Silent Push notes that many phishing pages replicate legitimate directory structures to increase credibility.
- Dedicated Infrastructure: The attackers utilize specific registrars (Dynadot, Porkbun, Namecheap) and unique IP ranges to manage their extensive network of phishing domains.
The campaign has predominantly focused on high-profile organizations, including Workday clients and entities such as Macy’s, Kaiser Permanente, and the California Employment Development Department. Silent Push’s research highlights a recent shift in tactics: “The threat actor was running an Unemployment Benefits scam targeting Kroger Grocery before switching to payroll phishing.”
The campaign’s scale is evident from the variety of targeted domains and infrastructure. For instance:
- Phishing for BambooHR and Roche: The attackers used domains like
myrocshe[.]comandmentalroccehget[.]comto host phishing pages masquerading as legitimate HR portals. - Custom Directory Structures: Some sites mimic the exact structure of real corporate HR portals, making it challenging for victims to discern their authenticity.
- Unemployment Portals and Credit Unions: Phishing campaigns have also targeted unemployment benefits portals and financial institutions such as Florida Credit Union and Weokie Credit Union.
The Payroll Pirates exploit human vulnerability and organizational trust. The phishing pages often include professionally worded content, with Silent Push citing, “strange language on the homepage emphasizing mental health and financial advice,” to build trust with victims.
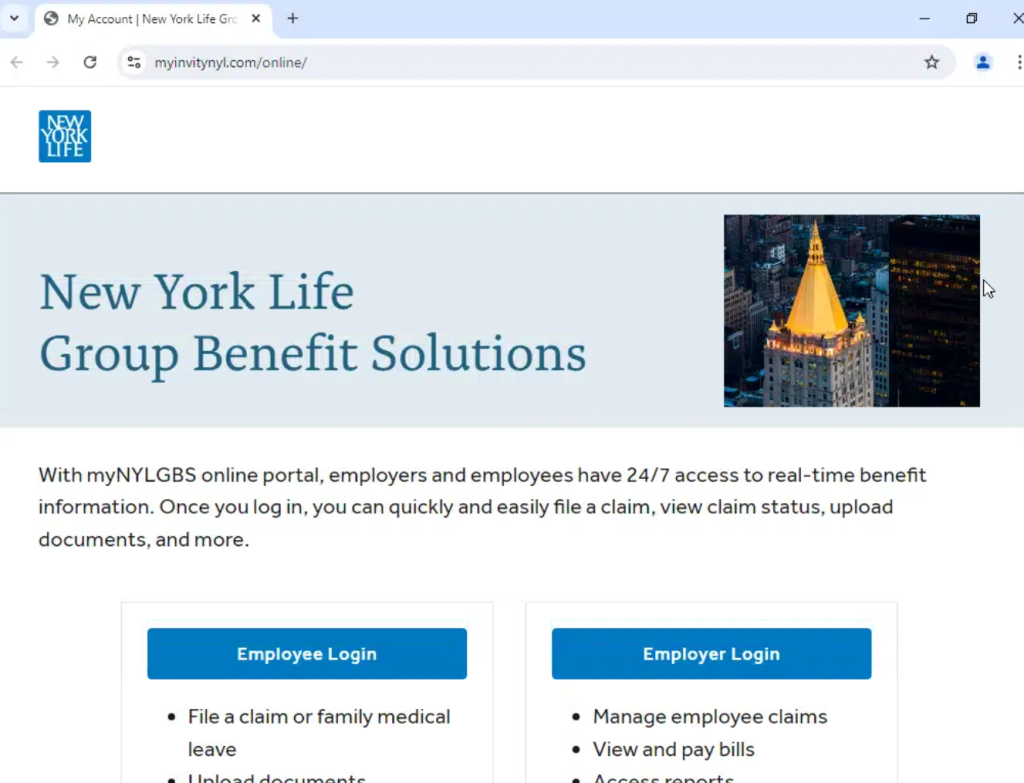
Despite efforts to disrupt the campaign, the Payroll Pirates remain active. Silent Push has identified over 100 new domains tied to the operation within hours of setting up monitors.
Related Posts:
- Hackers make poisoned Final Cut Pro specifically to target Mac users
- The Hidden Threat in Pirated macOS Applications: Unveiling a New Malware Campaign
- Pirated UltraEdit Software Hides macOS Malware Campaign
- Silent Skimmer Reemerges: New Tactics Target Payment Gateways
- US Enterprises Targeted: Silent Push Unmasks Scattered Spider’s Phishing Web