PcapXray
A Network Forensics Tool – To visualize a Packet Capture offline as a Network Diagram including device identification, highlight important communication and file extraction.
PcapXray Design Specification
Goal:
Given a Pcap File, plot a network diagram displaying hosts in the network, network traffic, highlight important traffic and Tor traffic as well as potentially malicious traffic including data involved in the communication.
Solution: Speed up the investigation process
- Make a network diagram with the following features from a Pcap file Tool Highlights:
- Network Diagram – Summary Network Diagram of full network
- Information:
- Traffic with Server Details
- Tor Traffic
- Possible Malicious traffic
- Data Obtained from Packet in Report – Device/Traffic/Payloads
- Device Details
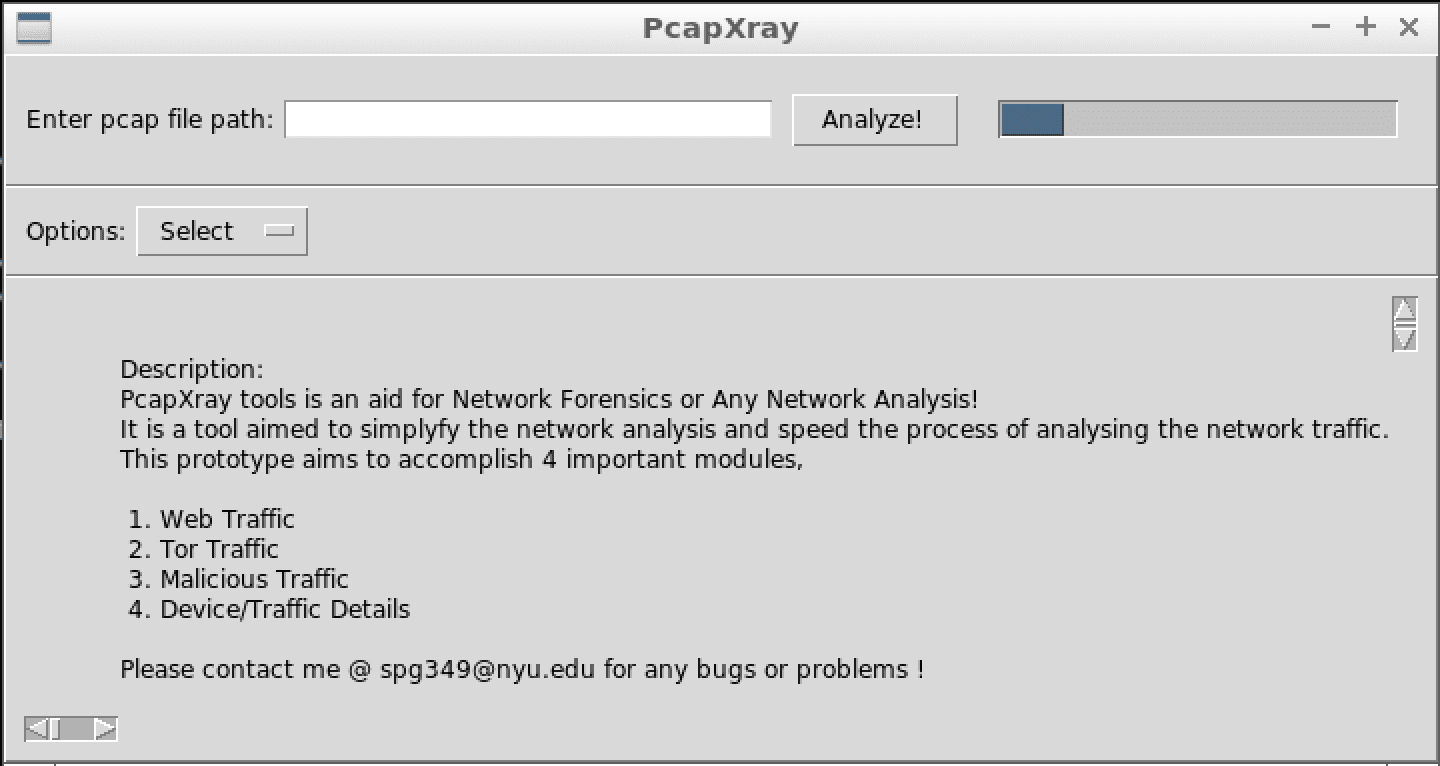
Tool Image:
Components:
- Network Diagram
- Device/Traffic Details and Analysis
- Malicious Traffic Identification
- Tor Traffic
- GUI – a gui with options to upload pcap file and display the network diagram
Python Libraries Used: – All these libraries are required for functionality
- Tkinter and TTK – Install from pip or apt-get – Ensure Tkinter and graphviz is installed (Most Linux contain by default)
- apt install python-tk
- apt install graphviz
- All these are included in the requirements.txt file
- Scapy – rdpcap to read the packets from the pcap file
- Ipwhois – to obtain whois information from ip
- Netaddr – to check ip information type
- Pillow – image processing library
- Stem – tor consensus data fetch library
- pyGraphviz – plot graph
- Networkx – plot graph
- Matplotlib – plot graph
Changelog v3.0
- Bump release as a checkpoint for 2.0 -> 3.0 work
- Update defcon27 demolabs asset
HighLights
- Covert communication
- Better UI and controls
- Interactive Map
- Python2 and Python3
- TLS Insight
Download
git clone https://github.com/Srinivas11789/PcapXray.git
Usage

Copyright (c) 2017 Srinivas Piskala Ganesh Babu
Source: https://github.com/Srinivas11789/

