PCWT
A web application that makes it easy to run your pentest and bug bounty projects.
Description
The app provides a convenient web interface for working with various types of files that are used during the pentest, automate port scan, and subdomain search.
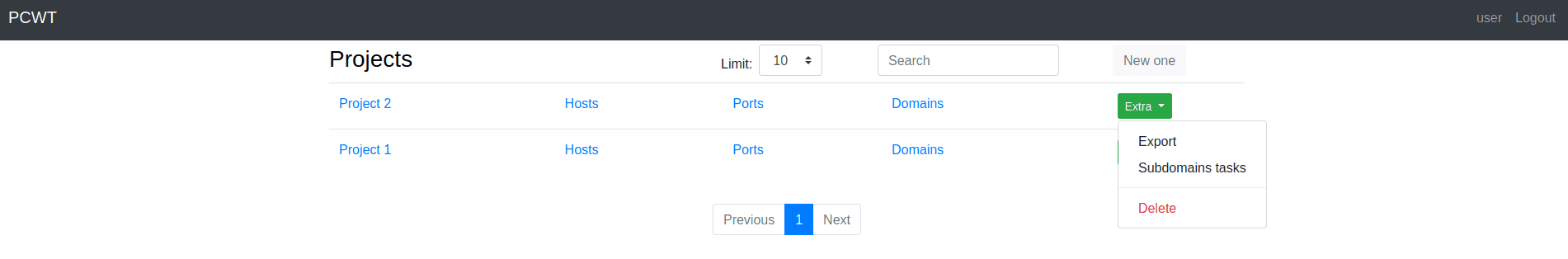
Main page
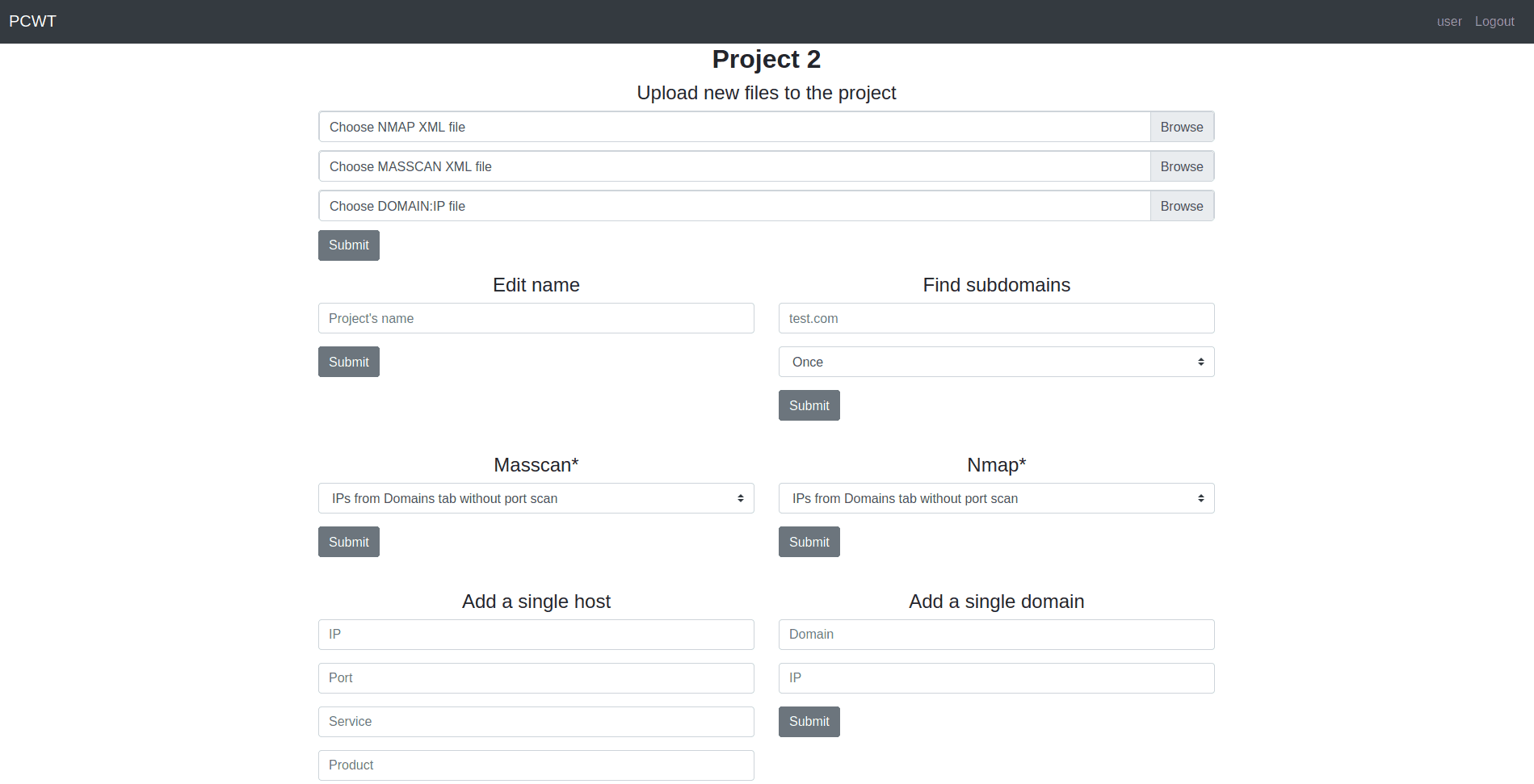
Project settings
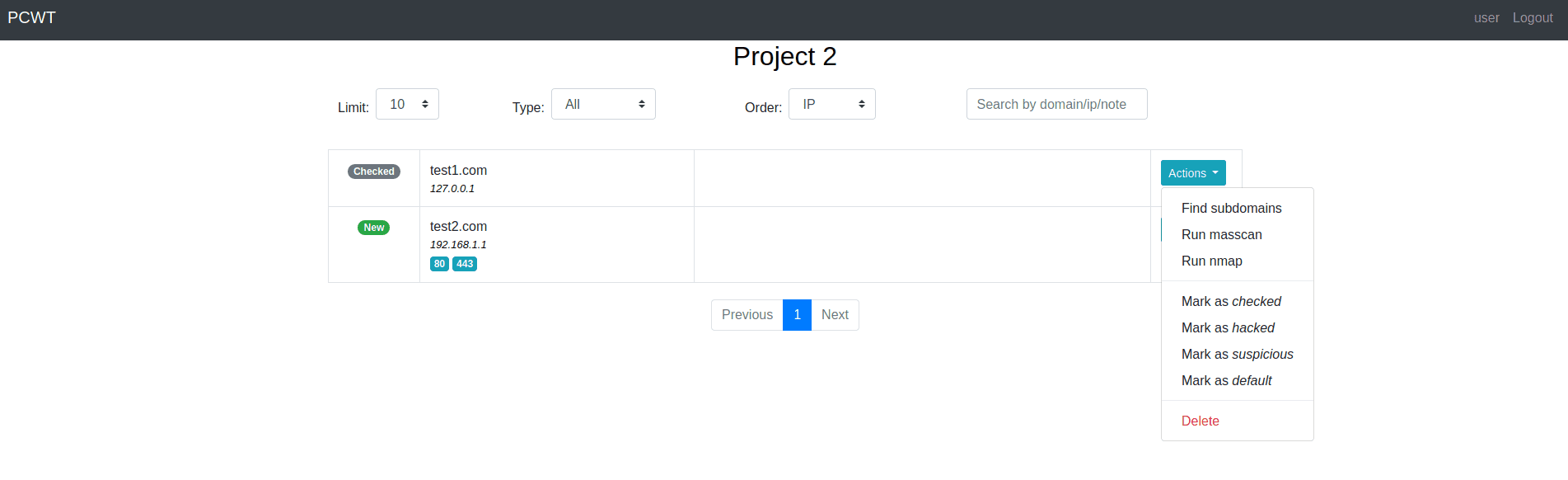
Domains dashboard
Port scan
You can scan ports using nmap or masscan. The nmap is started with the following arguments:
nmap --top-ports 10000 -sV -Pn --min-rate 300 --max-retries 2 [ip]
The masscan is started with the following arguments:
masscan -p 1-65535 --rate 2000
Subdomain search
Amass and findomain are used to find subdomains.
Features
- Leave notes to host, port, or domain.
- Mark host or domain with tags.
- Search by any field related to host, port, or domain (tags and notes are included). Regexp is available.
- Different types of sorting are available on almost all dashboards.
- Run the port scan for all hosts, hosts without port scan, or custom list.
- Create tasks for subdomains search (every 2 hours, every 5 hours, every day, or every week). You can also disable and enable them on-demand using the Subdomain tasks dashboard.
- Different types of export are available.
- Notifications about the start and end of the scan, as well as about newfound domains can be sent to Telegram. Update the config.py with your chat id and token.
Install
NOTE 1: Change the paths for amass, findomain, nmap, and masscan in config.py before running commands. NOTE 2: The app must be started as root if you want masscan to work.