The initial alarm for the autorun registry key creation | Image: Levelblue
Security researcher Jeff Kieschnick from LevelBlue uncovered the stealthy tactics of a Potentially Unwanted Application (PUA) masquerading as a PDF conversion tool. The report details the crafty maneuvers of the application named “PDFFlex” and its browser extension “ExtensionOptimizer” which uses a double layer of persistence to hide on a system.
Persistence mechanisms, while critical for legitimate applications, are often exploited by threat actors to maintain long-term control over systems. As Kieschnick notes in his report, “monitoring for and investigating persistence indicators are key components of any robust cybersecurity platform.” Two common techniques—AutoStart Execution and Scheduled Tasks—were leveraged by the PUA to establish a robust foothold in targeted environments.
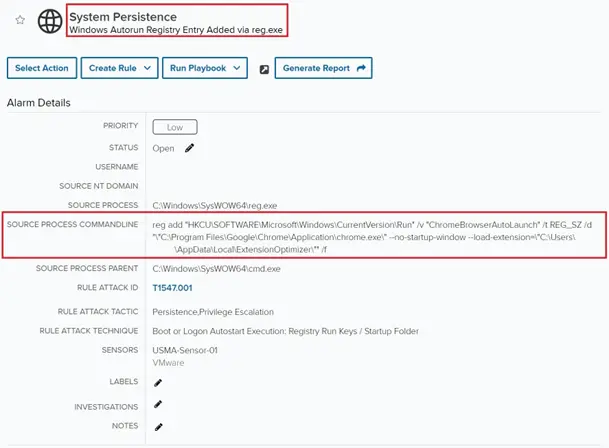
The saga began when a LevelBlue MDR SOC analyst detected an alarm from a Windows Autorun registry key named “ChromeBrowserAutoLaunch.” While seemingly innocuous, further analysis revealed it was tied to a sideloaded browser extension not sourced from the Chrome Web Store.
The extension’s dubious origin became apparent during a deeper investigation. The analyst uncovered that the registry key was created by a JavaScript process running under the guise of “node.exe” in the suspicious “PDFFlex” folder. Additionally, the application employed a Scheduled Task to maintain its persistence. According to the report, “this task was responsible for executing the process that was creating the Autorun registry key in an apparent double layer of persistence established on the endpoint.”
LevelBlue’s investigation extended to open-source intelligence (OSINT) tools, which flagged the application’s installer, FreePDF_49402039.msi, as potentially malicious. OSINT findings showed:
- The MSI installer was signed by “Eclipse Media Inc.,” a signature also linked to other suspicious files.
- VirusTotal and ANY.RUN classified the hash as malicious.
- The domain “pdfflex.io” was unregistered, adding to its questionable legitimacy.
LevelBlue promptly recommended remediation steps, including the removal of the related AppData folders, registry keys, and scheduled tasks. In one instance, the application had been whitelisted in a customer environment due to insufficient negative OSINT findings. However, the team’s persistence and detailed analysis persuaded the customer to move the hash to a blocklist instead.
“The application was neither desired nor expected in the customer environment,” Kieschnick noted, emphasizing that its persistence mechanisms and OSINT findings firmly placed it as a PUA, if not outright malicious.
Related Posts:
- npm’s Hidden Threat: The Covert Trojan Lurking in Your Windows System
- Malware Hiding in PDFs: What You Need to Know