Penetration Testing anonymously in Kali Linux with Anonsurf

IP spoofing, also known as IP address forgery or host file hijacking, is a hijacking technique that a hacker disguises as a trusted host to conceal his identity, cheat the web, hijack the browser, or access the network. IP addresses can be modified many ways, the most common is the use of proxy servers, VPN and TOR.
Anonsurf, which would use TOR anonymous IPTables throughout the system. Can be more convenient for you to start and stop I2P. This allows you to do all of the operations anonymously on Kali Linux while Anonsurf runs in the background. Anonsurf runs in the background and constantly changes the IP address, from time to time or you can simply restart the process to update the IP address.
How to use this repo
This repo contains the sources of both the anonsurf and pandora packages from ParrotSec combined into one.
Modifications have been made to use the DNS servers of Private Internet Access (instead of FrozenDNS), and fixes for users who don’t use the resolvconf application. I have removed some functionality such as the gui and iceweasel in ram.
This repo can be compiled into a deb package to correctly install it on a Kali system.
The easiest way to get this working is to just run the installer. See the installation section for further info.
NOTE: This may work with any debian/ubuntu system, but this has only been tested to work on a kali-rolling amd64 system
Installing
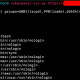
root@kali:~# git clone https://github.com/Und3rf10w/kali-anonsurf.git
root@kali:~/kali–anonsurf# ./installer.sh
It automatically updates the /etc/tor/torrc file and adds the following lines
VirtualAddrNetwork 10.192.0.0/10
AutomapHostsOnResolve 1
TransPort 9040
SocksPort 9050
DNSPort 53
RunAsDaemon 1
It also changes your parsing configuration as follows:
root@kali:~# vim /etc/resolv.conf
nameserver 127.0.0.1
nameserver 209.222.18.222
nameserver 209.222.18.218
If you do not like to use the DNS provided by the operator, change the DNS script in the following lines /etc/init.d/anonsurf
echo –e ‘nameserver 127.0.0.1\nnameserver 209.222.18.222\nnameserver 209.222.18.218’ > /etc/resolv.conf
Usage:
- anonsurf -h
- Start anonsurf:
root@kali:~# anonsurf start
- View your public IP
root@kali:~# anonsurf myip
- Restart anonsurf
root@kali:~# anonsurf restart
- Stop anonsurf
root@kali:~# anonsurf stop
DEMO
https://www.youtube.com/watch?v=uJgnxuWeZAY