ph0neutria v1.0.1 releases: malware crawler
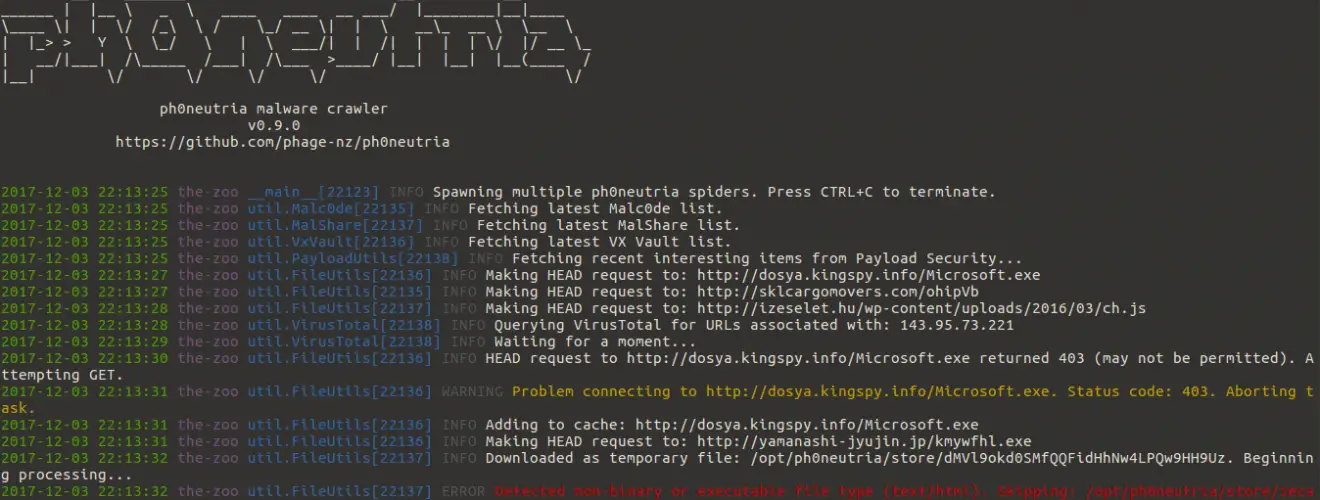
ph0neutria is a malware zoo builder that sources samples straight from the wild. Everything is stored in Viper for ease of access and manageability.

This project was inspired by Ragpicker (https://github.com/robbyFux/Ragpicker, formerly known as “Malware Crawler”). However, ph0neutria aims to:
- Limit the scope of crawling to only frequently updated and reliable sources.
- Maximise the effectiveness of individual indicators.
- Offer a single, reliable and well-organized storage mechanism.
- Not do work that can instead be done by Viper.
Sources
As of version 1.0.0 all sources are created as ‘plugins’, found in the plugin sub-directory of the core scripts folder. Default sources are:
- 0xffff0800’s Malware Library (credit: http://0day.coffee).
- CleanMX (requires approved user-agent).
- Cymon, which includes: Abuse.ch trackers, Bambenek C2 feed, Cyber Crime Tracker, Malc0de, URLVir and VX Vault.
- Hybrid Analysis (requires vetted API key).
- OTX.
- Shodan, using the Malware Hunter search facility.
- URLhaus.
Each plugin has parameters that must be completed prior to operation. You’ll find these at the top of each plugin file.
VirusTotal is a core component of ph0neutria that cannot be disabled. IP lists are fed into it to discover URL’s that are known for the IP’s. If you have a standard 5 requests/minute API key then I’d encourage being conservative with what you feed it. You can do this by:
- Reducing the number of Cymon feeds.
- Reducing your OTX subscription count.
- Setting the Hybrid Analysis SCORE_MIN parameter to 100.
Changelog v1.0.1
- Source update (added 0xffff0800’s library). Samples can now be tagged with VirusTotal sourced classification.
Installation
The following script will install ph0neutria along with Viper and Tor:
wget https://raw.githubusercontent.com/phage-nz/ph0neutria/master/install.sh
chmod +x install.sh
sudo ./install.sh
Simple as that!
Optional:
Configure additional ClamAV signatures:
Rename os.<yourdistro>.conf to os.conf, for example:
Modify configuration files:
- master.conf: search for “Enabled Databases” and enable/disable desired sources.
- user.conf: uncomment the required lines for sources you have enabled and complete them. user.conf overrides master.conf. You must uncomment user_configuration_complete=”yes” once you’ve completed setup for the following commands to succeed.
For more configuration info see: https://github.com/extremeshok/clamav-unofficial-sigs
mkdir /var/log/clamav-unofficial-sigs
clamav-unofficial-sigs.sh –install-cron
clamav-unofficial-sigs.sh –install-logrotate
clamav-unofficial-sigs.sh –install-man
clamav-unofficial-sigs.sh
cd /tmp/clamav-unofficial-sigs
cp systemd/* /etc/systemd
cd ..
rm -rf clamav-unofficial-sigs
It’ll take a while to pull down the new signatures – during which time ClamAV may not be available.
Usage
Take precautions when piecing together your malware zoo:
- Do not disable Tor unless replacing with an anonymous VPN.
- Operate on an isolated network and on dedicated hardware.
- Only execute samples in a suitable Sandbox (refer: https://github.com/phage-nz/malware-hunting/tree/master/sandbox).
- Monitor for abuse of your API keys.
Ensure Tor is started:
service tor restart
Start the Viper API:
cd /opt/viper
sudo -H -u spider python viper-api
Start the Viper web interface:
cd /opt/viper
sudo -H -u spider python viper-web
- Complete the config file at: /opt/ph0neutria/config/settings.conf
- Complete the config file at: /home/spider/.viper/viper.conf
Start ph0neutria:
cd /opt/ph0neutria
sudo -H -u spider python run.py
You can press Ctrl+C at any time to kill the run. You are free to run it again as soon as you’d like – you can’t end up with database duplicates.
To run this daily, create a script in /etc/cron.daily with the following:
#!/bin/bash
cd /opt/ph0neutria && sudo -H -u spider python run.py
Copyright 2018 Chris Campbell (phage-nz)
Source: https://github.com/phage-nz/