In a recent discovery, cybersecurity researchers at Trend Micro have unearthed a concerning development in the world of cyber threats. An active exploitation of CVE-2023-36025 has been identified, leading to the propagation of a previously unknown variant of malware known as Phemedrone Stealer.
Phemedrone Stealer is a stealthy malware strain that primarily targets web browsers, cryptocurrency wallets, and messaging apps, including popular platforms like Telegram, Steam, and Discord. This multifaceted malware goes beyond stealing data; it also captures screenshots and collects critical system information, such as hardware details, location, and operating system specifics. The stolen data is discreetly transmitted to the attackers through Telegram or their command-and-control server. What sets Phemedrone Stealer apart is its open-source nature, written in C#, and actively maintained on GitHub and Telegram.

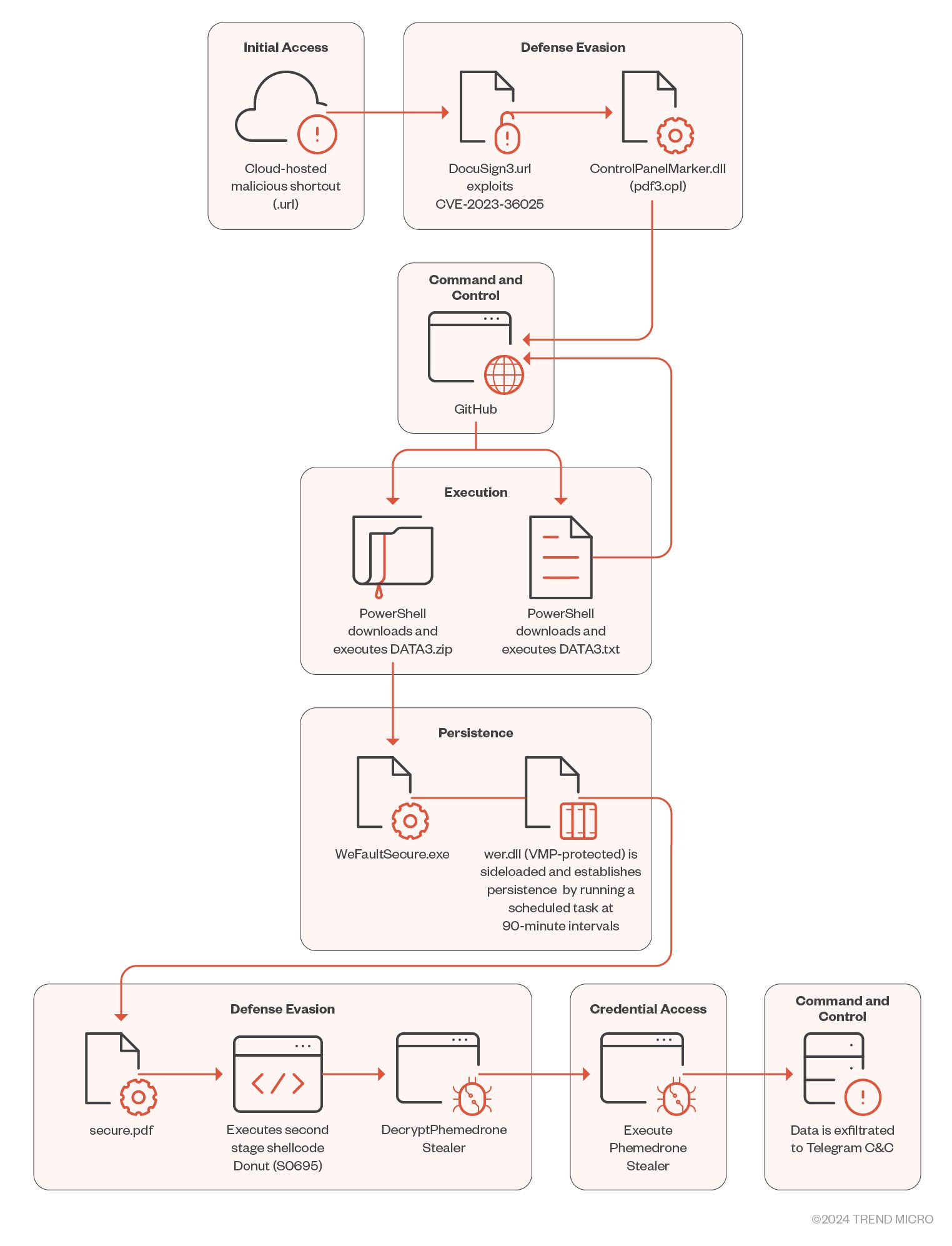
The root of Phemedrone Stealer’s success lies in its exploitation of CVE-2023-36025, a vulnerability affecting Microsoft Windows Defender SmartScreen. This vulnerability results from a lack of checks and associated prompts on Internet Shortcut (.url) files, which threat actors leverage to craft malicious .url files. These files download and execute malicious scripts, effectively bypassing Windows Defender SmartScreen warnings and checks. Microsoft patched this vulnerability on November 14, 2023, but the emergence of in-the-wild exploitation prompted the Cybersecurity and Infrastructure Security Agency (CISA) to include it in the Known Exploited Vulnerabilities (KEV) list.
Phemedrone Stealer’s infection chain begins with the hosting of malicious Internet Shortcut files on platforms like Discord or cloud services like FileTransfer.io. These files are often disguised using URL shorteners, making it easier for unsuspecting users to fall victim to these attacks. Once a user opens the malicious .url file, the exploitation of CVE-2023-36025 commences.
Upon execution of the malicious .url file, Phemedrone Stealer connects to an attacker-controlled server to download and execute a control panel item (.cpl) file. To elude Windows Defender SmartScreen’s security prompts, the attackers cleverly employ .cpl files as part of their malicious payload delivery mechanism. Leveraging MITRE ATT&CK technique T1218.002, they abuse the Windows Control Panel process binary (control.exe) to execute these .cpl files, which are, in fact, DLL files.
The journey doesn’t stop here. The malicious .cpl file, once executed, calls upon rundll32.exe to execute the DLL. This malicious DLL acts as a loader, invoking Windows PowerShell to download and execute the next stage of the attack, hosted on GitHub. This subsequent stage is another PowerShell loader named DATA3.txt.
DATA3.txt employs obfuscation techniques, making it challenging to decipher its true purpose during static analysis. By combining static and dynamic analysis, researchers manage to deobfuscate the GitHub-hosted loader. This results in the discovery of a ZIP file hosted on the same GitHub repository, comprising three files: WerFaultSecure.exe (legitimate), Wer.dll (malicious), and Secure.pdf (RC4-encrypted second-stage loader).
Wer.dll plays a crucial role in achieving persistence by creating scheduled tasks. The loader employs DLL sideloading, tricking the operating system into loading the malicious file instead of the legitimate one. This technique involves dynamic API resolving, using the CRC-32 hashing algorithm to import necessary APIs dynamically at runtime. XOR-based algorithms are used for string decryption, adding another layer of complexity.
Phemedrone Stealer is well-equipped to harvest a wide array of sensitive information, including browser data, cryptocurrency wallet details, Discord tokens, and much more. It employs a custom method to dynamically locate all subclasses of IService, efficiently processing them. Following data collection, it compresses and exfiltrates the information through network traffic via the Telegram API.
CVE-2023-36025’s exploitation continues to be a serious threat, as cybercriminals leverage it to introduce malware like Phemedrone Stealer. This case highlights the interconnected nature of open-source malware and public proof-of-concept exploits. To mitigate the risk, organizations must promptly update their Microsoft Windows installations and stay vigilant against evolving threats in the ever-changing cybersecurity landscape.